OVERPASS
Some background on this lab
What happens when a group of broke Computer Science students try to make a password manager?
Obviously a perfect commercial success!
This lab has only 2 things it appears to be looking for. A User.txt flag and a root.txt flag.
First thing we are going to do it load up the virtual machine.
Next we are going to enumerate with nmap

Some interesting ports that are open are 22 (SSH) and 80 (http). 80 means we have a webpage

Next I am going to run Gobuster against the site to look for any hidden directories

Another few interesting directories listed.
The /admin brings us to a login page
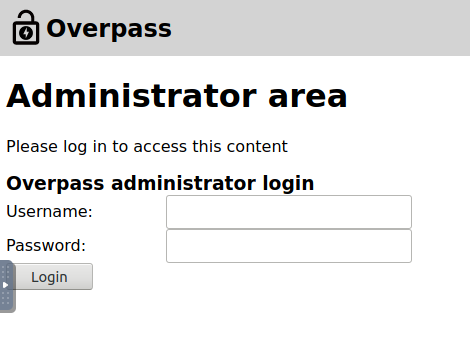
Checking into the source of the page we find this information in a login.js file
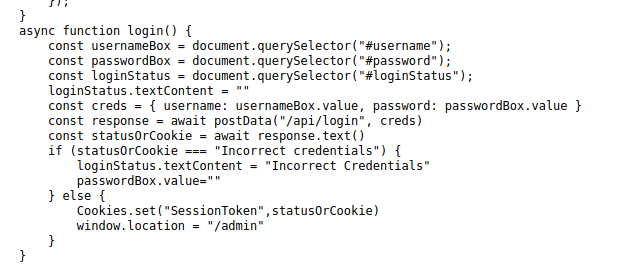
With this I am going to download the tool “Cookie Editor”


After refreshing the page we are in!

With this I am going to create a new text file with that private key and attempting to ssh using that key

With this I am going to use the ssh2john python script to attempt to crack
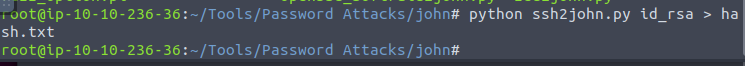
After using john to crack we get the password james13
Using james13 as the secret key, we were able to access!

Right in the home directory we are able to locate the user.txt flag that contains thm{65c1aaf000506e56996822c6281e6bf7}