A challenge that tests your reconnaissance and OSINT skills.
SuperSecure Corp, a fast-paced startup, is currently creating a blogging platform inviting security professionals to assess its security. The challenge involves using OSINT techniques to gather information from publicly accessible sources and exploit potential vulnerabilities in the web application.
Your goal is to identify and exploit vulnerabilities in the application using a combination of recon and OSINT skills. As you progress, you’ll look for weak points in the app, find sensitive data, and attempt to gain unauthorized access. You will leverage the skills and knowledge acquired through the Red Team Pathway to devise and execute your attack strategies.
Lets go ahead and enumerate
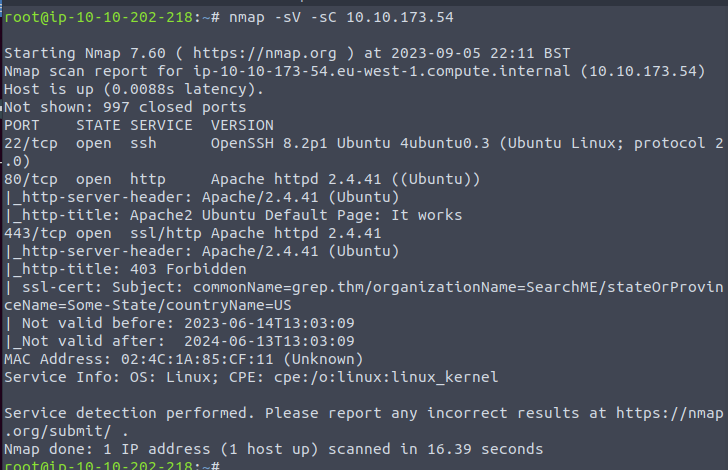
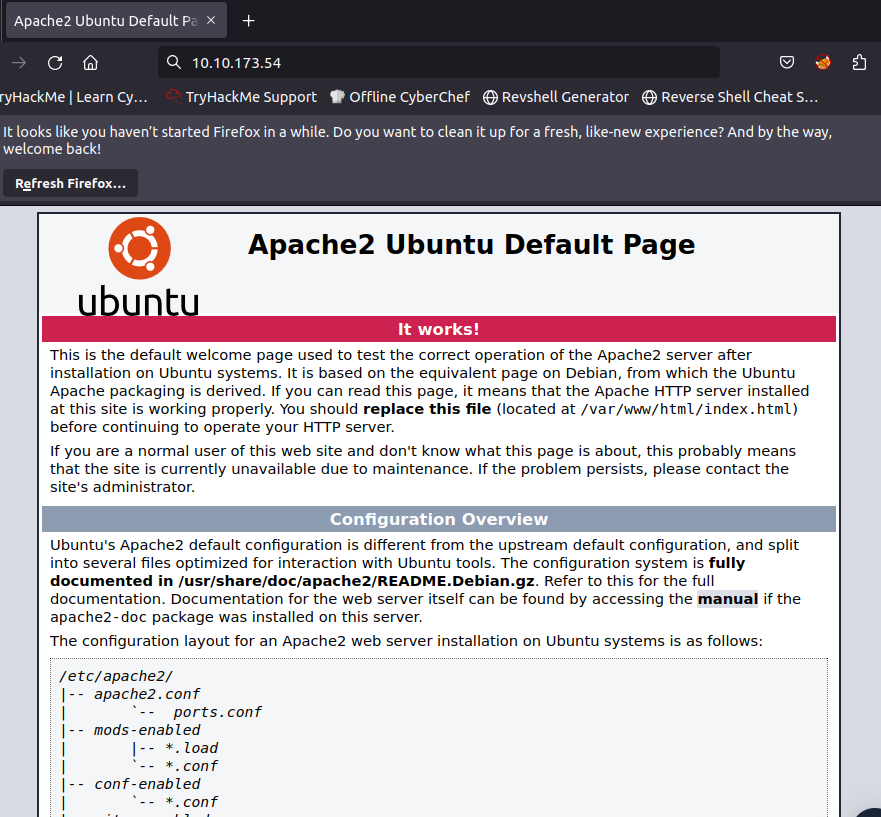
Looks like we have ports 80 and 443 open, so lets navigate there in the browser. We get an apache webpage
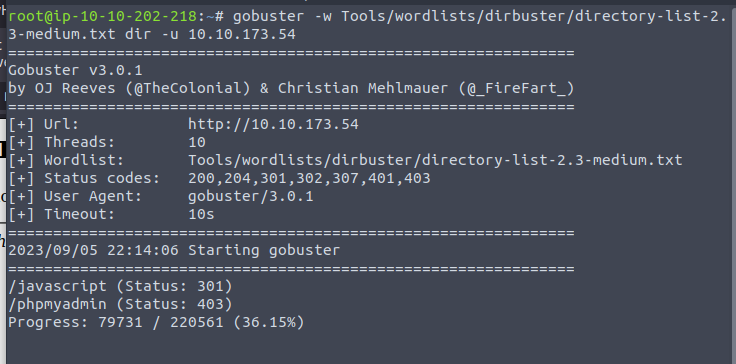
Using gobuster we discover a /javascript folder
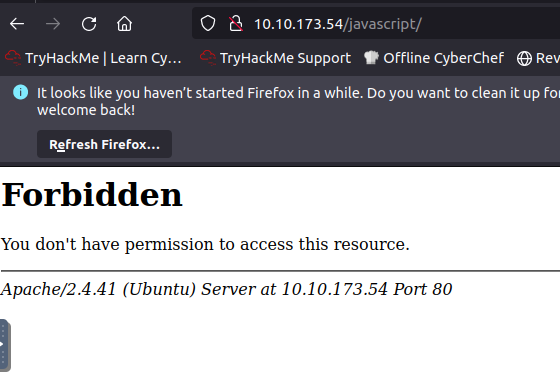
We dont have access to this resource it appears.
Same if we backtrack and use https to access the site
After some digging, if we add grep.thm to the host file for that IP, it then will allow us to access
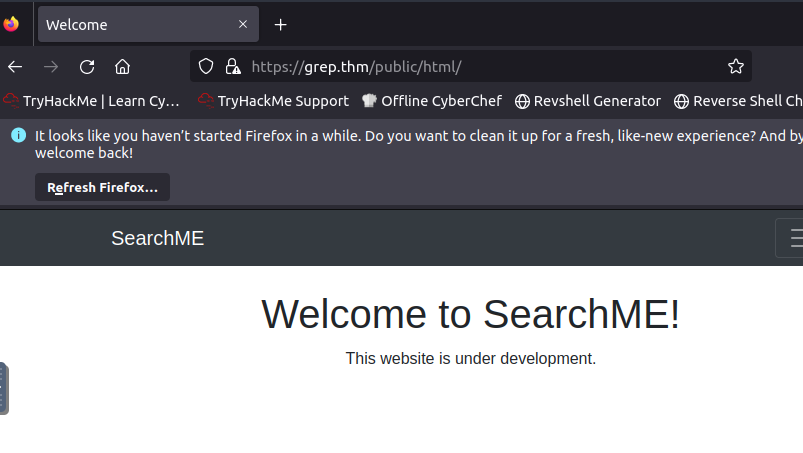
This site looks like it is under development. When we try and create an account in the register tab, we get an error stating “Invalid or expired API key”
This lab is based around OSINT, so we are going to search for “SearchME!” and we know its the php language so we are going to search both on github.
One of the options we come across is https://github.com/supersecuredeveloper/searchmecms
Checking into the commits on the repository, we locate the initial commit as well as the commit when they removed the key
The initial commit gives us an API key of ffe60ecaa8bba2f12b43d1a4b15b8f39
Now we will launch Burp and try and login to the site
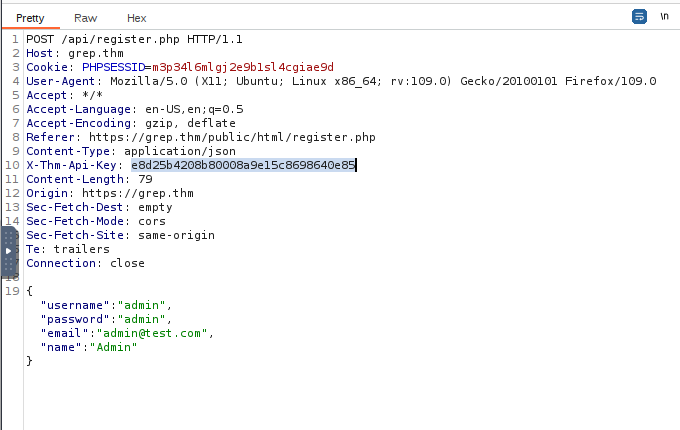
We have our spot to update the API key.
Admin was taken so I changed the user info to Nate and we are in!

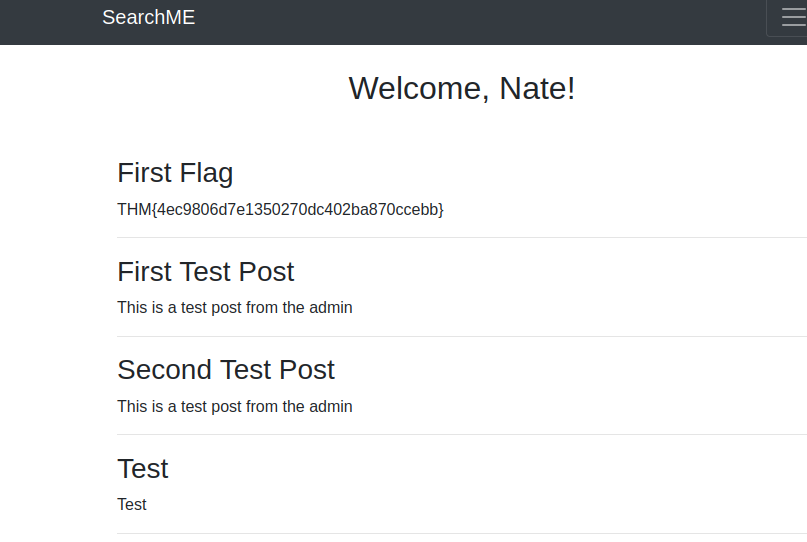
and we get our first flag of THM{4ec9806d7e1350270dc402ba870ccebb}
Next we want to look for the email of the admin user

