A multinational technology company has been the target of several cyber attacks in the past few months. The attackers have been successful in stealing sensitive intellectual property and causing disruptions to the company’s operations. A threat advisory report about similar attacks has been shared, and as a CTI analyst, your task is to identify the Tactics, Techniques, and Procedures (TTPs) being used by the Threat group and gather as much information as possible about their identity and motive. For this task, you will utilise the OpenCTI platform as well as the MITRE ATT&CK navigator, linked to the details below.
Reading through the document provided, we locate that the TTPs that APT X uses is Spear-phishing emails
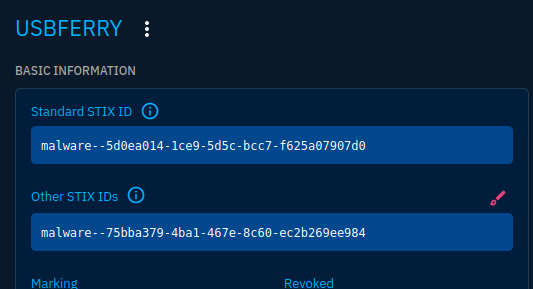
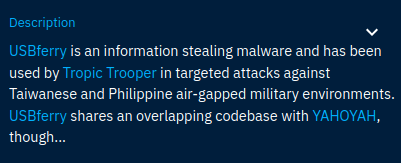
We also locate that the malware that is being used is called USBFerry
Next we want the malware STIX ID. This can be located using OpenCTI.
With the use of a USB, what technique did APT X use for initial access? For this answer, we are going to use the ATT&CK navigator. Highlighted, we get Replication through removable media
Next we are going to locate the actual identity of APT X. OpenCTI is showing us Tropic Trooper
On OpenCTI, how many Attack Pattern techniques are associated with the APT? Pivoting to this page — https://attack.mitre.org/groups/G0081/ — we just have to count. We end up with 39 different techniques
Next up we want the tool linked with Tropic Trooper. This can be found in the link from the previous section. It is BitsAdmin
Load up the Navigator. What is the sub-technique used by the APT under Valid Accounts? This is Local Accounts
The tactics that this falls under are Defense Evasion, Persistence, Privilege Escalation, Initial Access
Lastly, we want to know what technique the group is known for under the tactic collection. This is Automated Collection

