This box is an easy rated box. Appears to only be looking for user and root flag. So lets go!

Nmap scan shows us that 22 and 80 are open. Lets roll into the webpage

Here we get an apache web server. With this info we are going to run gobuster to find some directories

We find the directory /sitemap
Digging through the webpage I wasn’t able to locate anything noteworthy. Checked source code as well
Metasploit didnt return any results from searching “unapp”
So decided to run gobuster again against /sitemap

Hit a standstill with these directories.
Started testing against it with a different wordlist (one of my new techniques) and received a few additional hits

This yielded some additional results. Some interesting ones involved here. Especially the /.ssh one (knowing that SSH is open on this box)
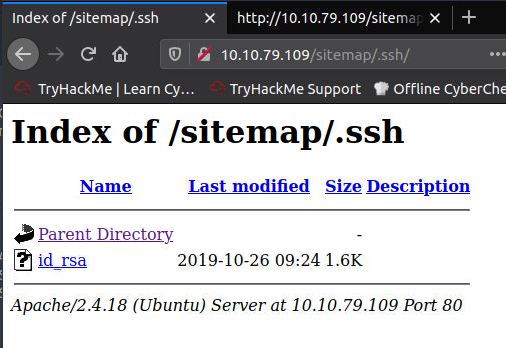
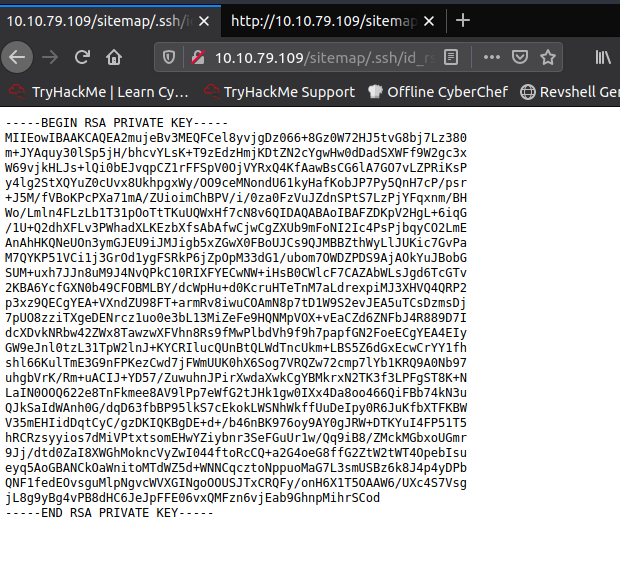
Opening id_rsa we get an SSH key!
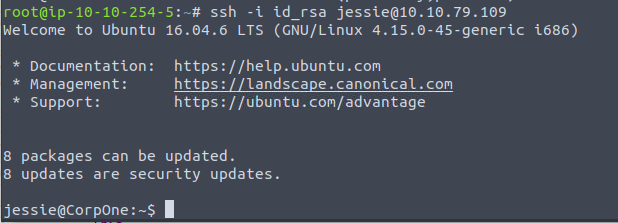
Trying to SSH with just the key is going to default to Root. Since we have a user flag we are looking for as well we will want to locate a username
Going through page source again we find “Jessie”

And we are in!
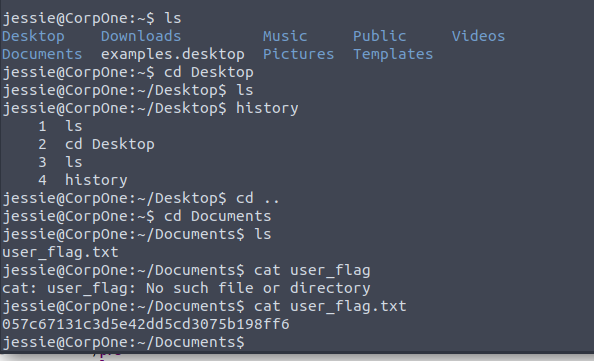
Searching the files we have our first flag!
Running sudo -l we get the following

Lets run out to GTFO bins to see if we can get an way to get root!
https://gtfobins.github.io/gtfobins/wget/
A little trial and error on this one and we get our root flag!


