Hello there,
I am the CEO and one of the co-founders of futurevera.thm. In Futurevera, we believe that the future is in space. We do a lot of space research and write blogs about it. We used to help students with space questions, but we are rebuilding our support.
Recently blackhat hackers approached us saying they could takeover and are asking us for a big ransom. Please help us to find what they can takeover.
Our website is located at https://futurevera.thm
Hint: Don’t forget to add the MACHINE_IP in /etc/hosts for futurevera.thm ; )
This box seems to be looking for one flag. It appears to be located around subdomain enumeration
This lab is exactly what I’ve been looking for to strengthen my subdomain enumeration skills
Based on the hint we will want to add our IP address for futurevera.thm to the host file


We have our homepage. From here lets locate some subdomains

Our results show us both Portal and payroll are available as subdomains

Seeing a there was nothing at Payroll.futurevera.thm and portal.futurevera.thm, I did some research.
For WordPress sites, blog.domain is typically a subdomain that is used.
So testing blog.futurevera.thm, we get the following
 Looks to be a standard WordPress site here
Looks to be a standard WordPress site here
Navigating around I didnt find too much to work with
So moving on we are testing support.futurevera.thm (support.domain is another popular one)

Checking into the certificate of this page we find another domain
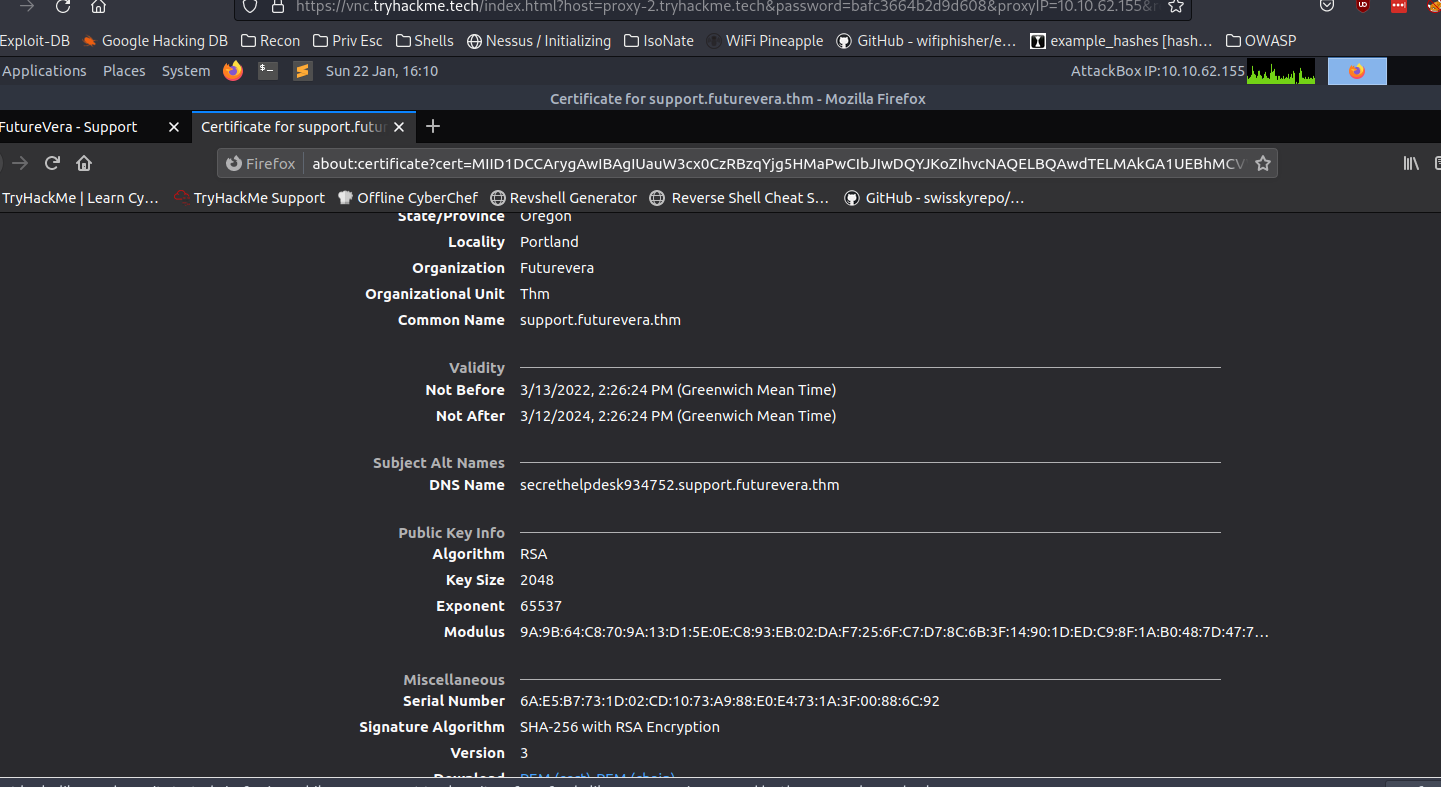
secrethelpdesk934752.support.futurevera.thm
After adding DNS name to the host file and entering into web browser, we get the flag!

This is definitely a box I would like to revisit at a later date. I believe Ffuf is able to continue to run to locate the subdomains but I need to locate the correct word lists to get to that point