This box doesn’t give too much info. Appears they are only looking for 2 flags (user and root)
Going to start out with trusty nmap

Looks like port 22 and 80 are open
The webpage seems to be running apache

Using gobuster I was able to locate a directory called /content


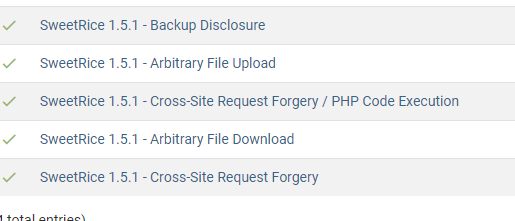
Using searchsploit I was able to locate the following exploits

It looks like This is going to be the route we go — https://www.exploit-db.com/exploits/40718
Navigating to that path we locate the backup content. Woo!
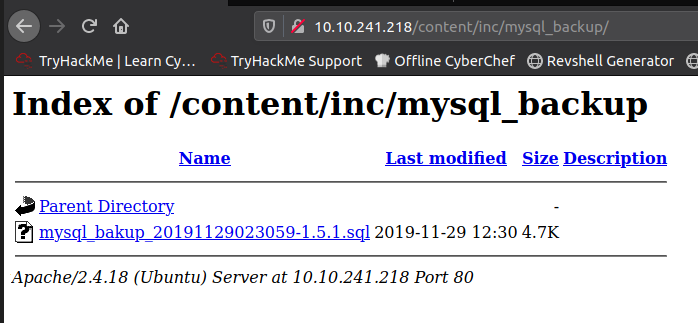
Downloading the file and looking through the backups we find the username – manager and password 42f749ade7f9e195bf475f37a44cafcb
Using hashcat we find the password is Password123 — hashcat password.txt Tools/wordlists/rockyou.txt

From here I was unsure where to locate the admin portal with our credentials. Looked towards a tutorial and located that that had run gobuster once more against the /content folder
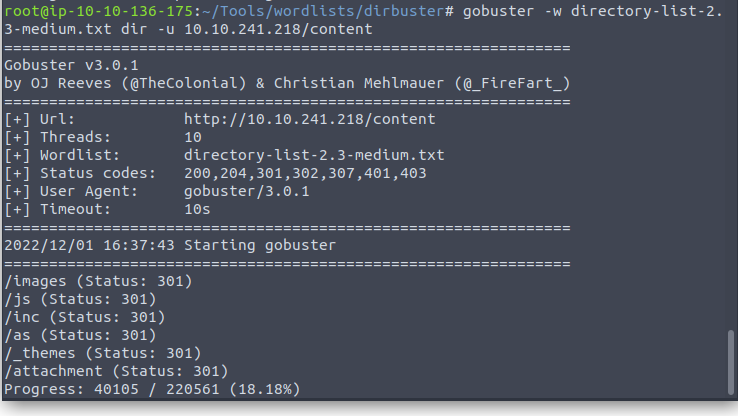
Checking into each of these we see that /content/as is the login portal we are looking for.


The version in the top left is showing version 1.5.1
We are going to use the Arbitrary File download exploit — https://www.exploit-db.com/exploits/40698
Running the program in the terminal brings us a prompt to enter target URL