You’ve learned some great nmap skills! Now can you combine that with other skills with netcat and protocols, to log in to this machine and find the flag? This VM 10.10.215.206 is listening on a high port, and if you connect to it it may give you some information you can use to connect to a lower port commonly used for remote access!
Pretty quick box on this one. Going to put our Nmap skills to the test
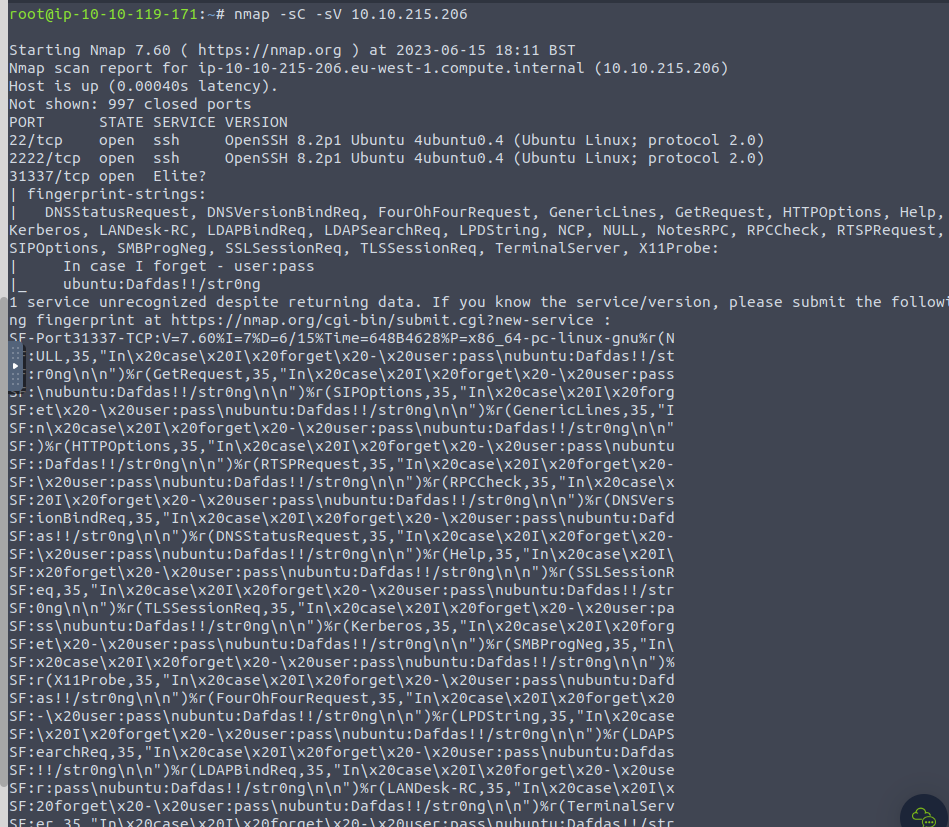
Using the -sC option, we are able to gather some information from port 31337. -sC is used for nmap scripts.
It was able to locate the following
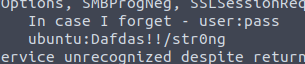
Thats a username and password. Lets try and SSH in using those credentials (port 22)
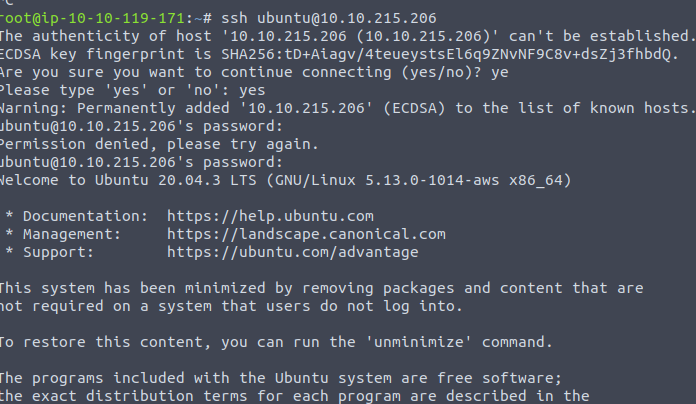
We are in! Navigating from here to the /home/user folder, we are able to locate our flag!