This lab look involves gathering data and locating a flag
First thing I’m going to do is scan the machine and see what available ports are open

We located a few juicy open ports (ftp/http/ssh)

Seems to be running an apache service on port 80
Next Im going to run Gobuster against this machine
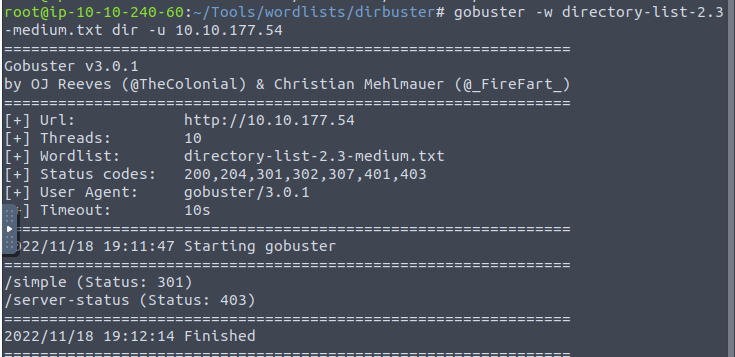

navigating to /simple we are presented with CMS
Bottom of the page states “This site is powered by CMS Made Simple version 2.2.8”
CVE we are going to utilize is CVE-2019-9053
https://www.exploit-db.com/exploits/46635
Downloaded the exploit and attempted to run it

Looks like we’ll need some arguments with it
Troubleshooting for some time I was able to narrow down that python2 is required for this work properly.
Then ran into an issue where “requests” was needed, so I installed with command sudo apt-get install python-requests
It then required a module called termcolor using sudo apt-get install python-termcolor
Ran it again and boom!

password we get is secret
From here we have a username (mitch) and a password (secret).
Lets go ahead and login with SSH

Had to add a -p argument since ssh is running on port 2222

in the home directory we find another user
from here we want to elevate priviledges.
Running sudo -l we see that Vim can run

off to GTFO bins we go!
From there we find we can run the command to get a root shell
sudo vim -c ‘:!/bin/sh’


