You have found yourself in a strange corridor. Can you find your way back to where you came?
In this challenge, you will explore potential IDOR vulnerabilities. Examine the URL endpoints you access as you navigate the website and note the hexadecimal values you find (they look an awful lot like a hash, don’t they?). This could help you uncover website locations you were not expected to access.
This challenge is looking for one thing, the flag
So lets go ahead and enumerate with nmap
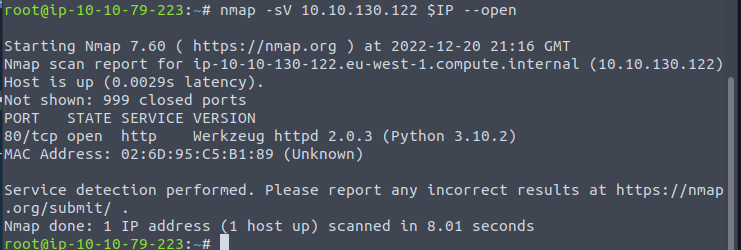
Looks like 80 is open. So lets go ahead and navigate to the webpage
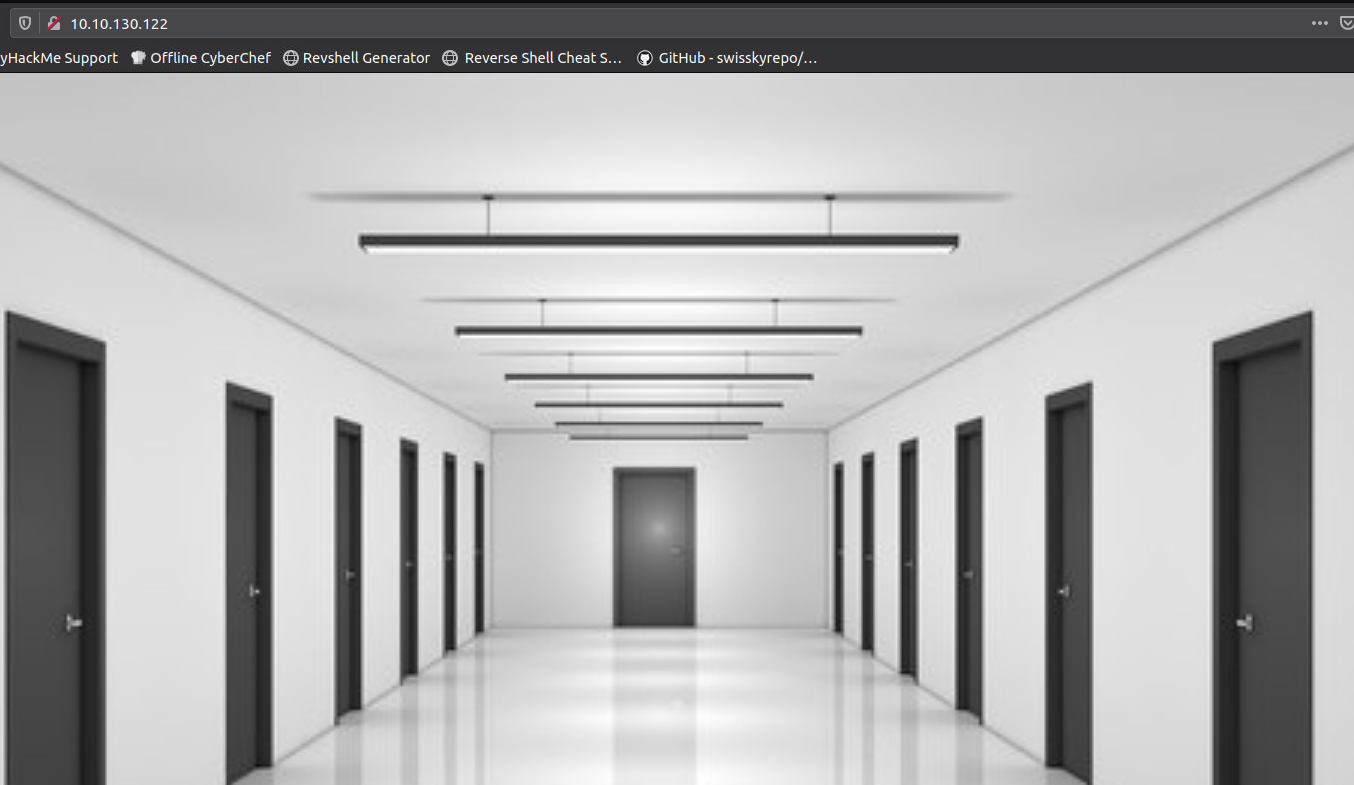
Looks like we get alot of doors. Clicking on the doors brings us to webpage that has an interesting directory
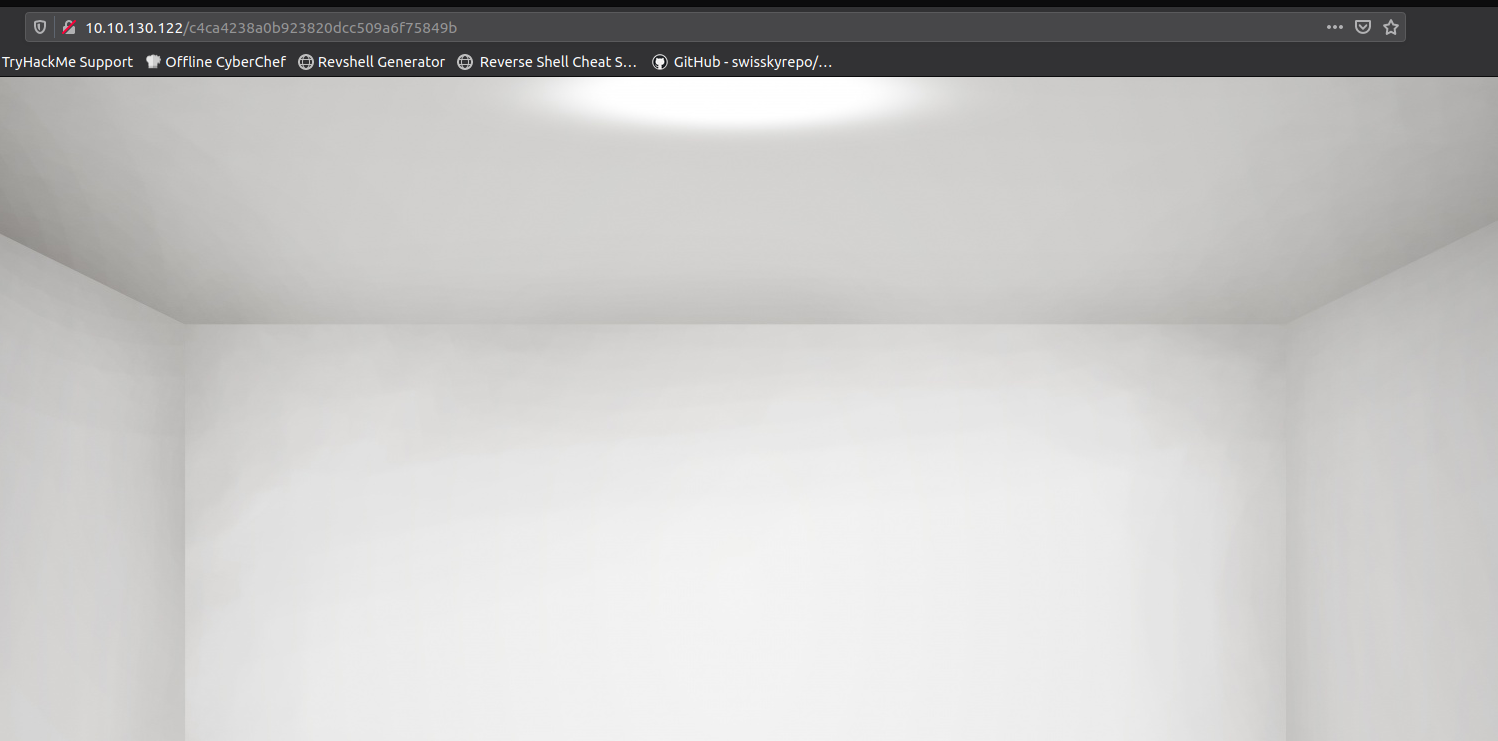
From experience the directory naming scheme looks like MD5 hashes
So lets gather each one and add to a .txt file (in hopes to cracking the hash)
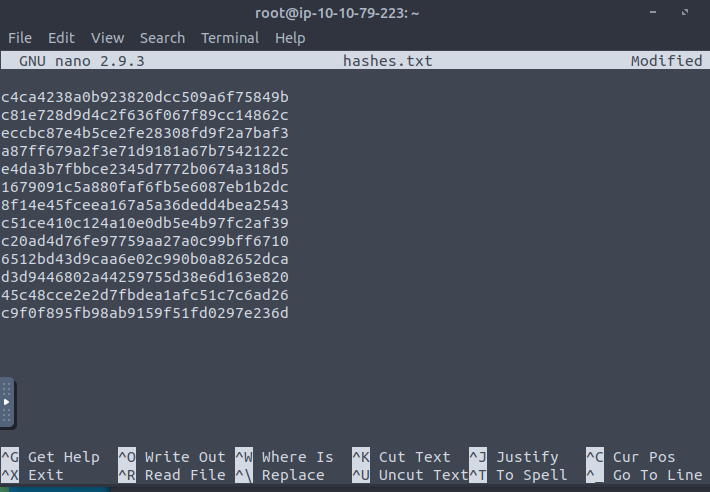
From here we are going to attempt to crack using the rockyou.txt file and the hashcat tool
Using the command hashcat -m 0 hashes.txt Tools/wordlists/rockyou.txt
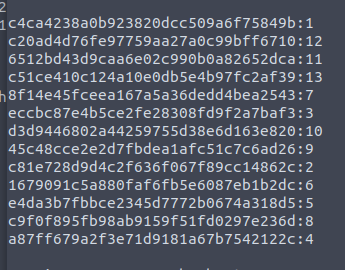
Looks like the cracked hashes are numbers. From here we are going to try the next logical number (14) in hash form. Using Cyberchef we get the below md5 hash
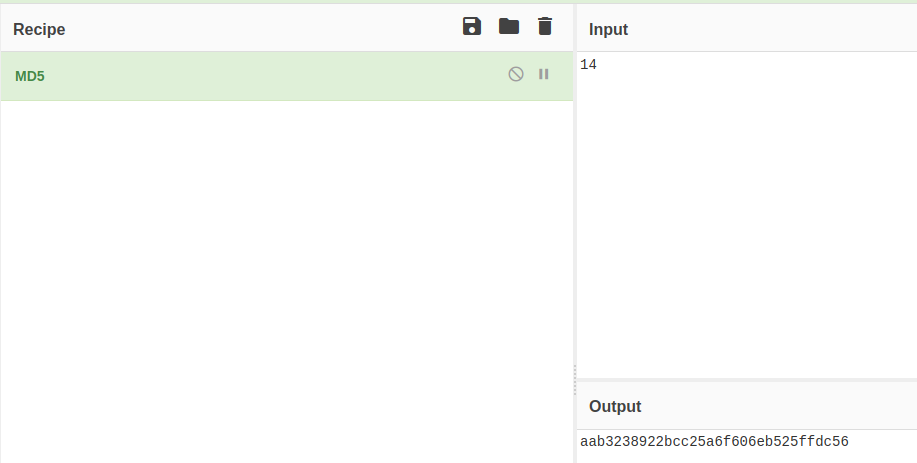

Failed. Going to try another route and go with 0 (zero)
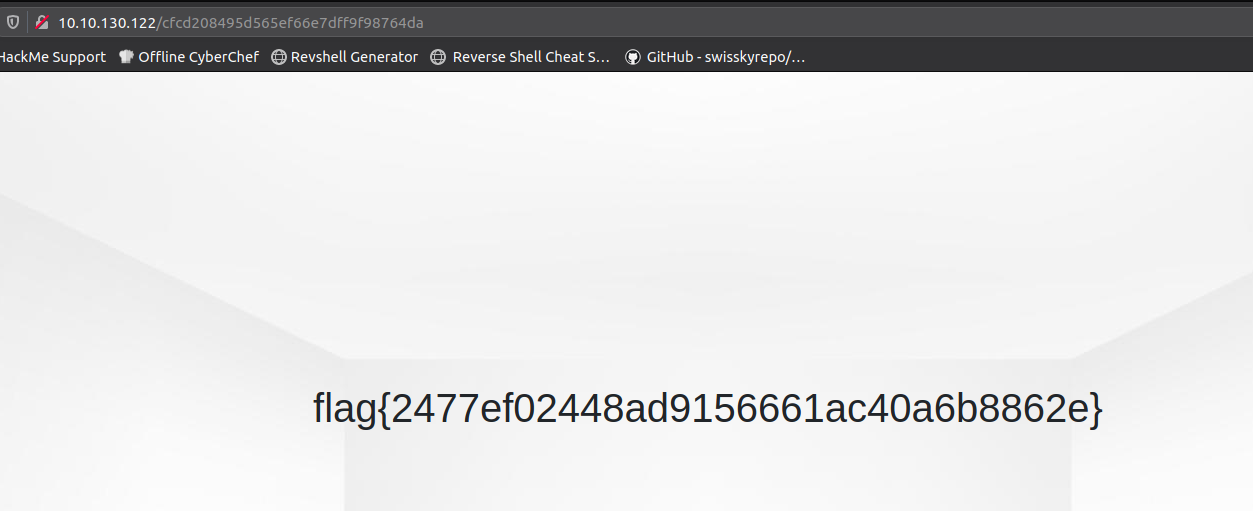
And boom! We have our flag!

