Welcome to Lian_YU, this Arrowverse themed beginner CTF box! Capture the flags and have fun.
First thing we are going to do here is launch our VM and attackbox to get this lab rolling
It would like us to locate a web directory. So going to run gobuster against the IP and see what we can find
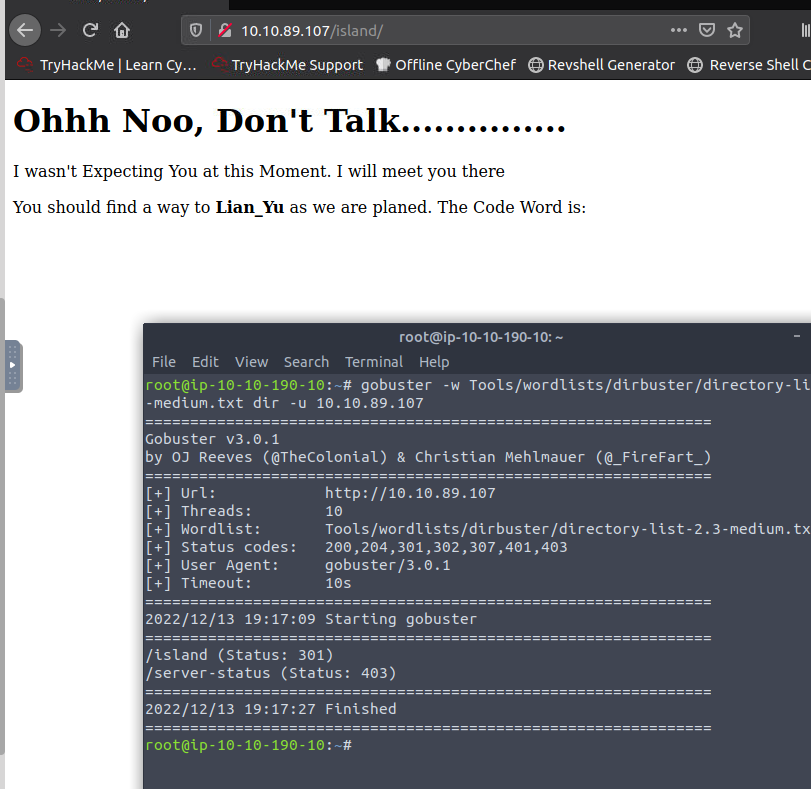
We locate a directory called /island.
It states there is a codeword but its not showing. Highlighting over, it appears to just be in white font
Codeword: Vigilante
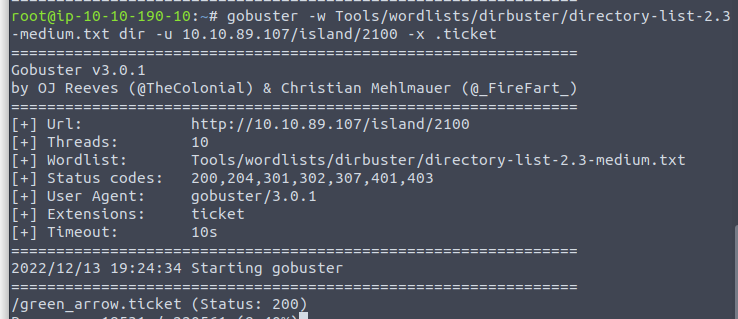
Running gobuster again against /island we find a directory called /2100
From here we get a youtube video that no longer appears to be valid. Crap
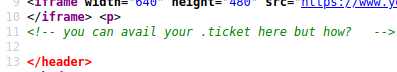
Checking into the source, we see this comment. SO I believe we are looking for a .ticket
From here I ran gobuster again and added -x .ticket to the end of it and boom! /green_arrow.ticket
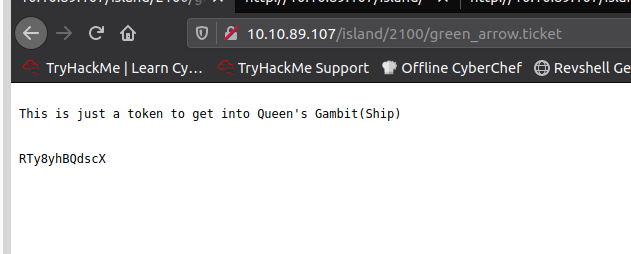
RTy8yhBQdscX
Checking into some walk throughs, It appears this is base58 encoded
Using Cyberchef it comes out to
!#th3h00d
I got so excited about running gobuster that I forgot to enumerate with Nmap. So lets go!
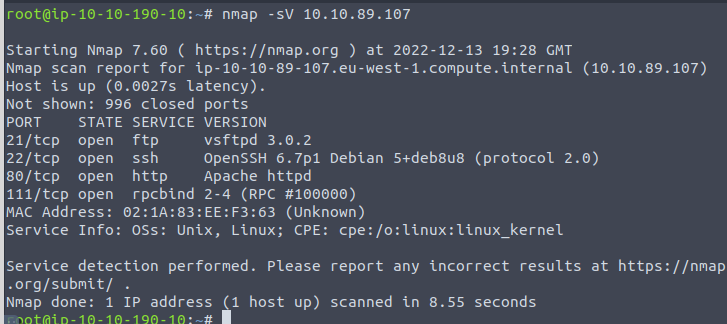
We have alot of fun stuff here.
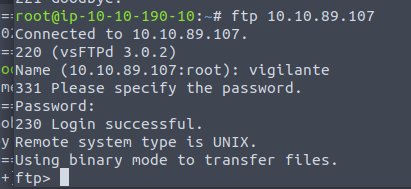
going to attempt to access ftp first anonymously
Did not work.
Using username Vigilante and password !#th3h00d we were able to access!
with LS we get 3 files
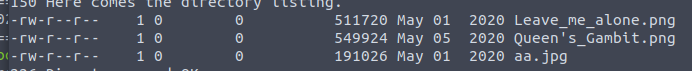
File itself appears corrupted. Using tool hexedit (Sudo apt install hexedit) and the info below, I was able to correct the header and fix the image
Byte 1 should be [0x89]: 89
Byte 2,3 and 4 should be [0x50 0x4E 0x47]: 504E47
Byte 5 and 6 should be [0x0D 0x0A]: 0D0A
Byte 7 should be [0x1A]: 1A
Byte 8 Should be [0x0A]: 0A
Opening the file gives us the password password
Using Steghide we are able to extract an ss.zip file out of the aa.jpg image
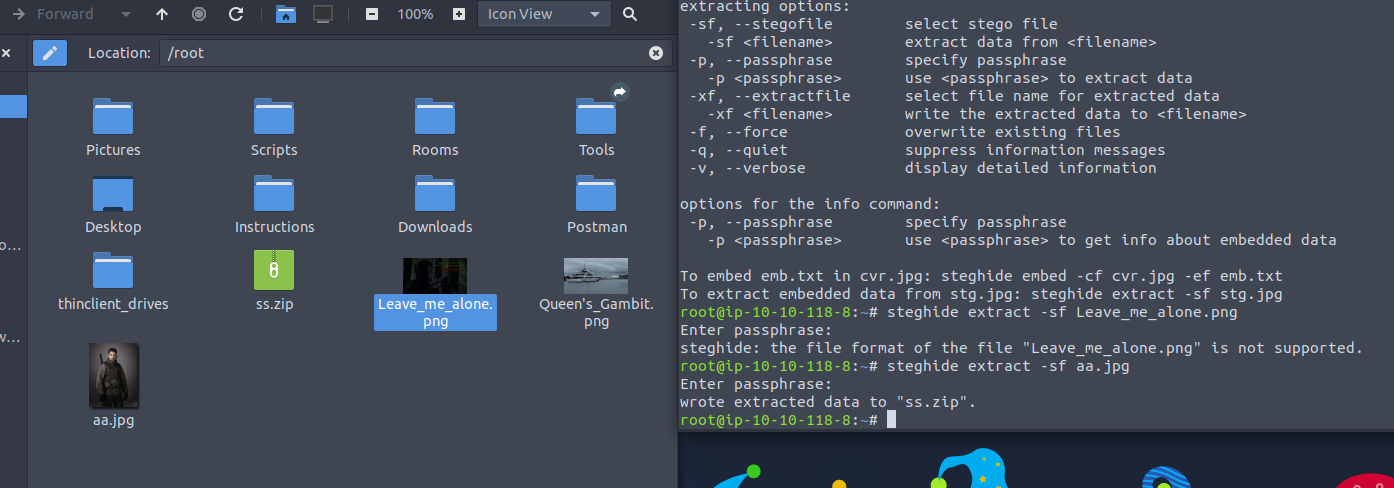
the ss.zip file gives us the following information
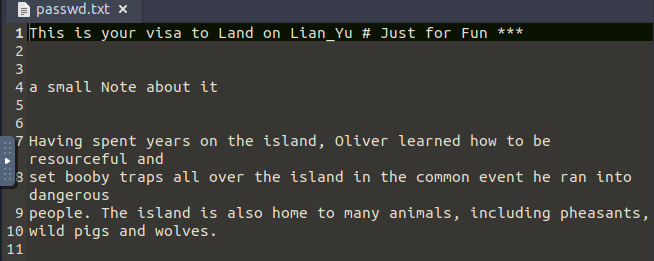
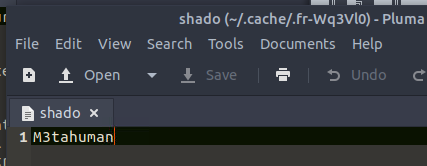
Using this to SSH into Slade’s account
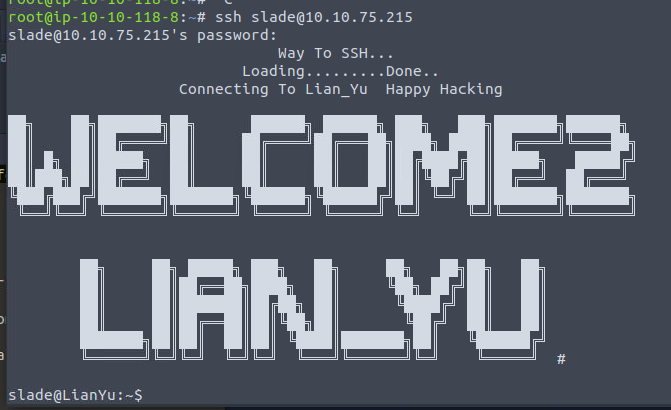
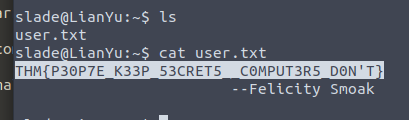
Next step is to get root access for the flag
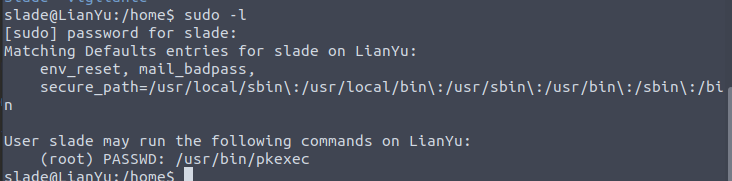
From here it looks like /usr/bin/pkexec is open
heading over to GTFO bins we locate this comand



